AiPrise
21 min read
December 18, 2025
KYC Startups: Solutions and Challenges 2026

Key Takeaways










In 2026, startups focused on Know Your Customer (KYC) are no longer niche players; they’re mission-critical infrastructure for every business that handles digital onboarding, compliance, and fraud risk. The identity verification market is expected to grow from about USD 13.75 billion in 2025 toward nearly USD 39.82 billion by 2032.
But this growth comes with real pressure on businesses like yours. Legacy verification processes struggle with global regulations and fraud threats, while customers demand faster, seamless onboarding without compromising security. In this scene, KYC startups are innovating with AI, biometrics, and automated workflows to meet these demands.
In this blog, you’ll explore the key challenges KYC startups face in 2026, the leading solutions and trends, how to evaluate them, and what it means for your business.
Key Takeaways
- KYC startups are growing rapidly in 2026 due to rising compliance pressure, advanced fraud tactics, and demand for faster, scalable onboarding.
- Core challenges include regulatory complexity, high verification costs, fragmented data, sophisticated fraud, and infrastructure scalability.
- Emerging solutions focus on AI-driven verification, automated KYB and UBO checks, biometrics, behavioral risk scoring, and reusable digital identity models.
- Businesses evaluating KYC startups must prioritize accuracy at scale, global coverage, seamless integration, and predictable pricing.
- Unified platforms like AiPrise help address these challenges by combining KYC, KYB, AML, and fraud risk management into a single, audit-ready system.
Why Are KYC Startups Growing So Fast in 2026?
You are onboarding users in real time, across borders, and often inside products that were never designed for compliance-first workflows. In 2026, growth is no longer limited by customer demand but by how quickly you can verify trust without breaking user experience or regulatory rules.
Traditional approaches cannot keep up with your launch speed, market expansion plans, or fraud exposure. This gap is where modern KYC startups are accelerating fast and becoming default partners for regulated growth.
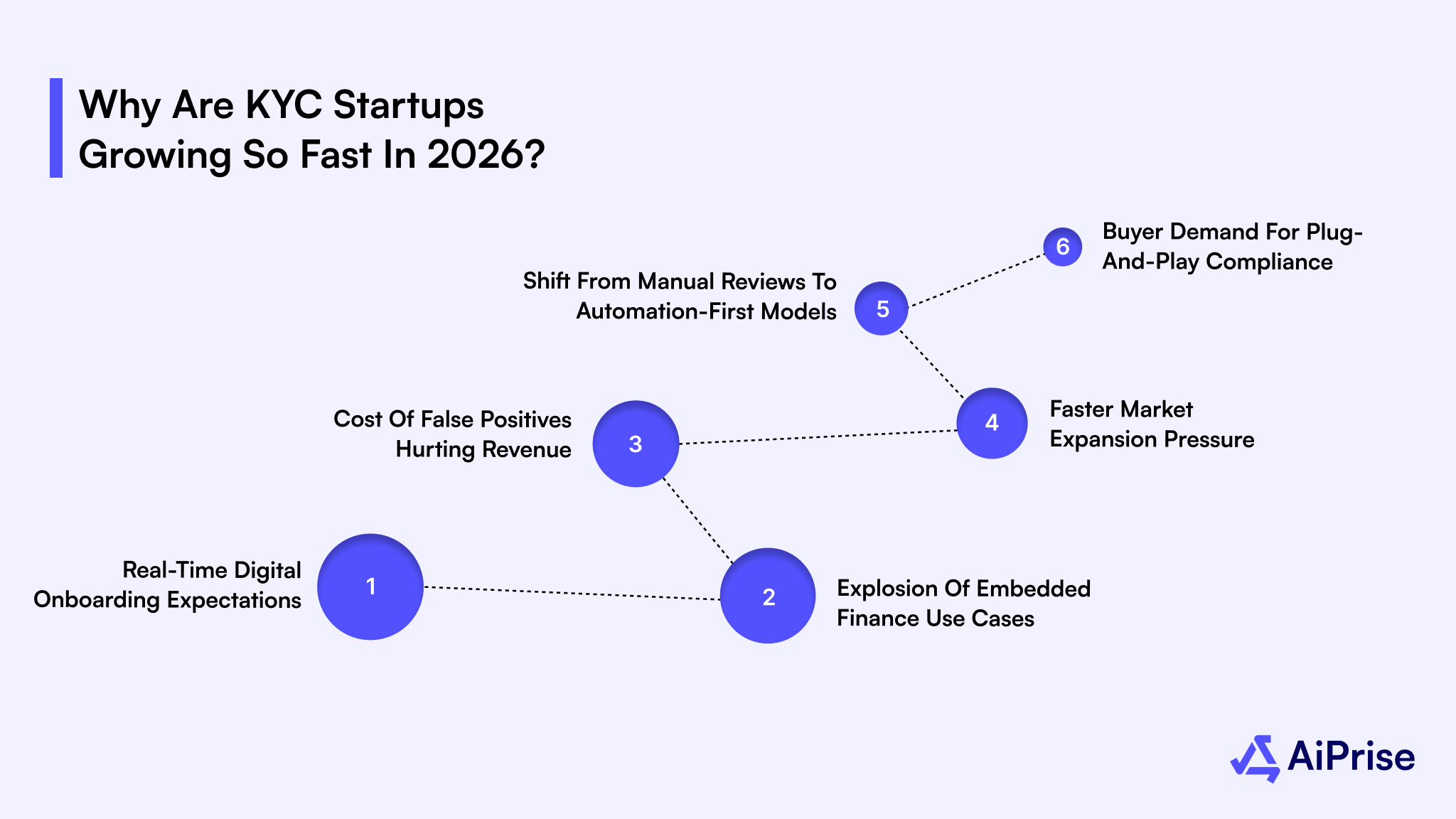
Here are the key reasons driving this momentum:
- Real-Time Digital Onboarding Expectations: You are expected to onboard users in seconds, not days, especially in payments, crypto, and embedded finance flows.
- Explosion of Embedded Finance Use Cases: When KYC runs inside lending, wallets, or SaaS platforms, you need flexible verification processes that adapt to product logic.
- Cost of False Positives Hurting Revenue: Overblocking legitimate users directly impacts conversions, churn, and lifetime value at scale.
- Faster Market Expansion Pressure: Entering new regions quickly requires verification coverage without rebuilding compliance from scratch.
- Shift From Manual Reviews to Automation-First Models: You cannot rely on analyst-heavy reviews when onboarding spikes overnight during product launches or campaigns.
- Buyer Demand for Plug-and-Play Compliance: You want APIs that work out of the box, not long enterprise integrations that slow your roadmap.
Also read: KYC and AML in France: How Identity Verification Works.
Despite rapid growth, KYC startups in 2026 are simultaneously grappling with several critical challenges.

Major Challenges Faced by KYC Startups in 2026
By 2026, building a KYC startup is not just about verifying identities. You are expected to operate at the intersection of regulation, security, user experience, and scale from day one. Buyers no longer compare you only with other startups. They compare you with internal compliance teams, legacy vendors, and in-house risk engines.
At the same time, regulators expect consistency, transparency, and defensible decisions across millions of checks. One weak layer in your system can expose both you and your customers to fines, fraud losses, or reputational damage.
Below are the most pressing challenges shaping KYC startups in 2026.
Increasing Regulatory Complexity Across Markets
In 2026, regulatory complexity is no longer about understanding one rulebook. It is about managing constant regulatory motion across jurisdictions where enforcement intensity differs by market.
Expansion into new regions now exposes verification systems to overlapping laws, local regulator interpretations, and sudden policy updates. What worked for one country last quarter can trigger compliance gaps in another today. This creates operational stress for products that must stay compliant without slowing onboarding or increasing manual intervention.
Below are the core regulatory challenges creating friction at scale:
- Diverging KYC Standards Between Jurisdictions: Identity requirements vary widely across the US, EU, and emerging markets, forcing verification logic to change by region. A document or check accepted in one market may be insufficient or non-compliant in another.
- Regulators Expecting Localized Decision Logic: Authorities increasingly expect verification outcomes to reflect local risk patterns, not generic global rules. This becomes critical when serving crypto platforms or cross-border payment providers.
- Frequent Regulatory Updates With Short Lead Times: New guidance from bodies like FinCEN or regional regulators often arrives with limited implementation windows. Engineering teams must adapt quickly without breaking existing workflows.
- Higher Scrutiny During Audits and Examinations: Buyers now demand proof that verification decisions are explainable and consistently applied. Missing audit trails can stall enterprise deals or trigger post-onboarding reviews.
- Cross-Border Data Handling Restrictions: Expanding internationally introduces data storage and processing constraints that affect how verification data is collected, stored, and shared across systems.
Also Read: How to Build Effective KYB Workflows for Seamless Business Compliance
High Cost of Verification & Data Acquisition
By 2026, the economics of verification will have become harder to manage as data quality expectations rise. Every additional data source, document type, or fraud signal increases cost before value is realized.
At the same time, customers expect higher approval rates and fewer manual reviews. This creates margin pressure, especially when onboarding volumes fluctuate. Pricing mistakes at the verification layer now directly impact customer acquisition cost, unit economics, and the ability to scale profitably across products.
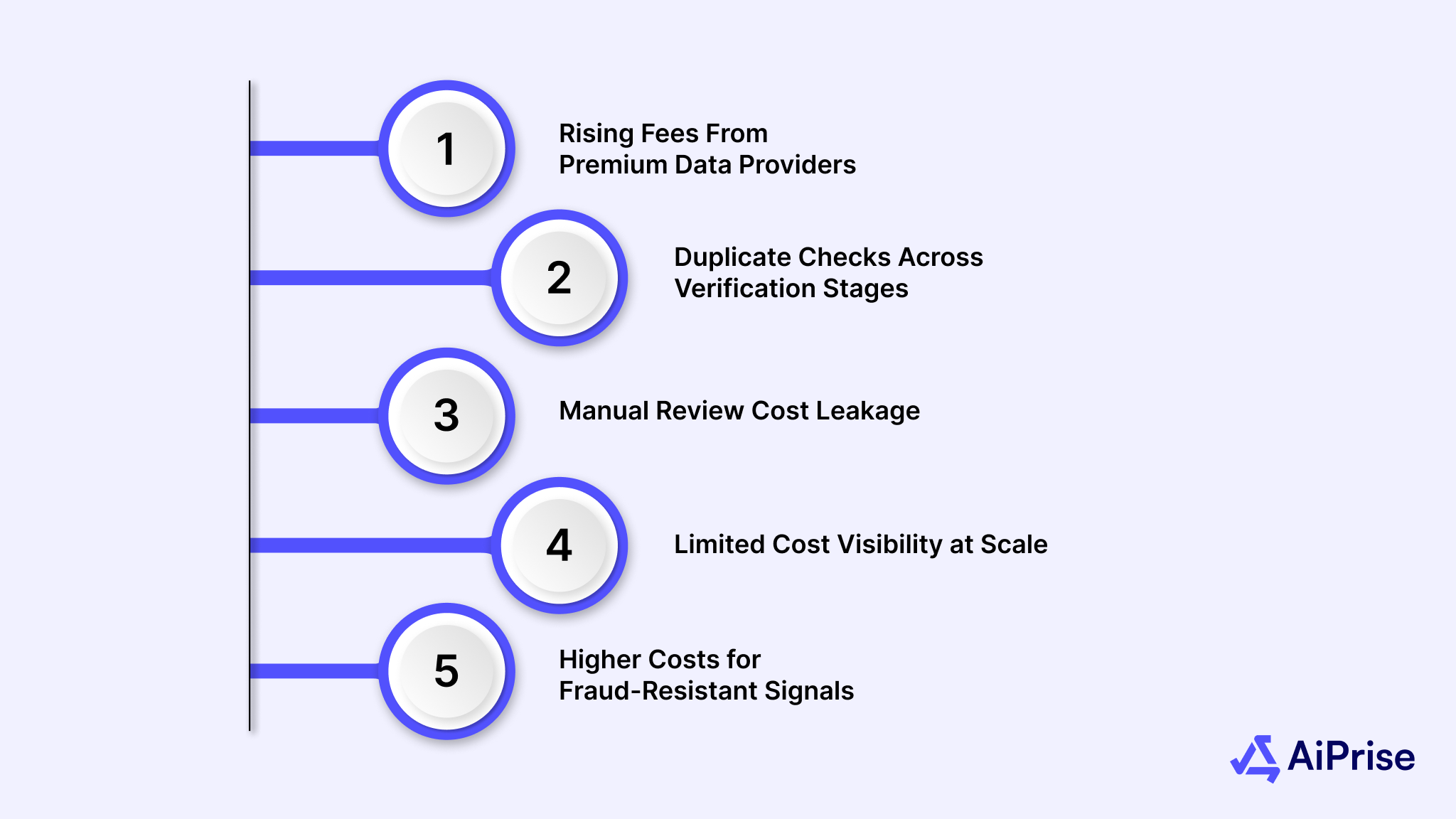
Below are the main cost drivers shaping this challenge:
- Rising Fees From Premium Data Providers: Accessing authoritative government, credit, and business registries often comes with usage-based pricing. Costs increase sharply as transaction volumes grow across regions.
- Duplicate Checks Across Verification Stages: Identity, business, and risk checks often pull overlapping data from different sources. Without optimization, the same information is paid for multiple times within one onboarding flow.
- Manual Review Cost Leakage: Low-confidence matches trigger analyst reviews that scale linearly with volume. Each manual intervention adds operational cost and slows customer onboarding.
- Limited Cost Visibility at Scale: When verification is abstracted behind APIs, it becomes difficult to track the cost per successful onboarding. This makes pricing and forecasting harder for fast-growing platforms.
- Higher Costs for Fraud-Resistant Signals: Advanced checks like document authenticity or behavioral signals are more expensive but increasingly necessary. Skipping them increases fraud exposure, while adding them raises verification spend.
Rising fraud losses and verification spend are making it harder to scale onboarding profitably. AiPrise helps reduce fraud exposure and unnecessary checks using its intelligent Fraud Risk Scoring engine.
Balancing Speed With Accuracy in Identity Checks
Fast onboarding is now a growth lever, but accuracy defines long-term survival. In 2026, customers abandon flows that take too long, while regulators penalize weak verification outcomes. This puts direct pressure on how identity decisions are made in milliseconds.
Every added check can slow conversion, yet removing steps increases risk exposure. The real challenge is not choosing speed or accuracy, but designing systems that adapt dynamically based on risk, context, and user behavior.
Below are the key friction points you must manage carefully:
- User Drop-Off During Multi-Step Verification: Long document uploads or repeated retries cause abandonment, especially on mobile-first platforms. Even small delays can reduce completion rates at scale.
- Over-Strict Matching Thresholds Blocking Real Users: Aggressive accuracy rules reject legitimate users due to lighting, device quality, or name variations. This directly impacts revenue and customer trust.
- Latency From Third-Party Checks: External data sources introduce response delays that compound across multiple checks. These delays become visible to users during real-time onboarding.
- One-Size-Fits-All Verification Logic: Treating low-risk and high-risk users the same increases friction unnecessarily. Adaptive flows are required to maintain both speed and confidence.
- Limited Feedback Loops for Model Tuning: Without clear signals from approvals and rejections, it becomes difficult to improve decision quality. This leads to stagnant performance over time.
Fragmented Global Databases & Data Silos
Identity data is not centralized, standardized, or evenly accessible in 2026. Each country maintains its own registries, formats, and access rules, often with varying data quality. When onboarding users or businesses across borders, verification outcomes depend on how well fragmented sources can be stitched together in real time.
Below are the core challenges created by data fragmentation:
- Inconsistent Data Formats Across Regions: Names, addresses, and identifiers follow different structures by country. Normalizing this data in real time adds complexity and increases error rates during matching.
- Uneven Data Depth by Market: Some regions offer rich, digitized records while others rely on limited or outdated sources. This makes verification reliability unpredictable across geographies.
- Delayed Access to Authoritative Registries: Many government or business registries do not support real-time queries. Batch updates introduce latency and reduce confidence in verification outcomes.
- Disconnected Identity and Business Records: Individual identity data often exists separately from company ownership or director information. This weak linkage complicates KYB and UBO checks.
- Operational Overhead From Multi-Vendor Data Stacks: Relying on multiple providers for coverage creates integration complexity. Each added source increases failure points and maintenance effort.
Rising Fraud Sophistication (Synthetic IDs, Deepfakes)
Fraud in 2026 is engineered, automated, and designed to pass basic verification checks. Identity attacks are no longer random or low effort. Synthetic profiles blend real and fake data, while AI-generated faces and voices are built to bypass traditional liveness controls.
As onboarding volumes grow, fraud attempts scale faster than manual intervention can handle. This shifts the challenge from catching obvious fraud to detecting subtle inconsistencies without creating friction for genuine users.
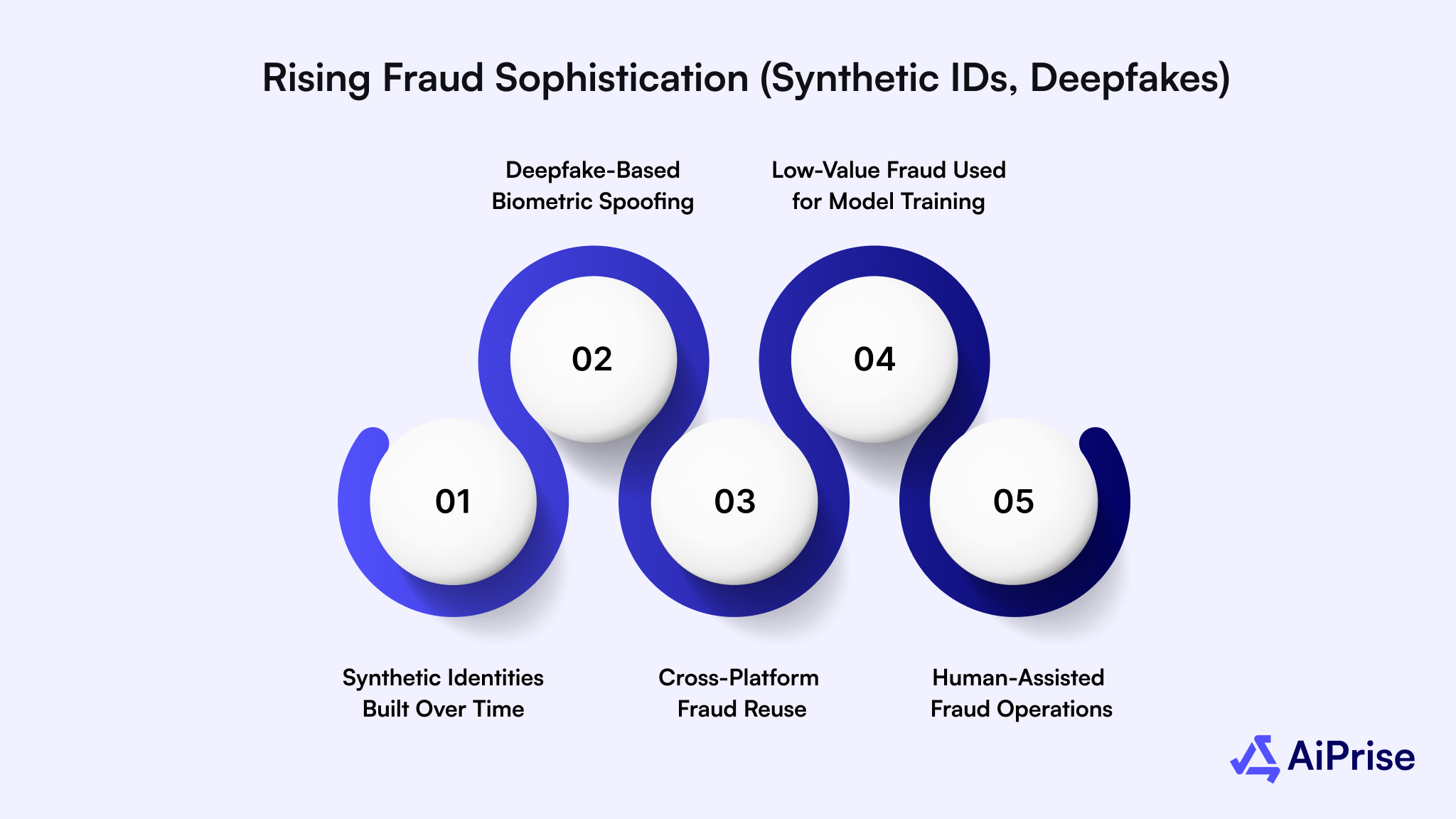
Below are the key fraud patterns increasing pressure on verification systems:
- Synthetic Identities Built Over Time: Fraudsters combine real social security numbers, phone data, and fabricated names to create profiles that look legitimate across multiple checks.
- Deepfake-Based Biometric Spoofing: AI-generated video and voice samples are used to defeat basic face match or selfie checks, especially in remote onboarding flows.
- Cross-Platform Fraud Reuse: Verified identities from one platform are reused to attack others. Lack of shared intelligence makes early detection difficult.
- Low-Value Fraud Used for Model Training: Small, repeated transactions are used to test system weaknesses. These attacks prepare larger fraud attempts later.
- Human-Assisted Fraud Operations: Fraud rings now combine automation with human oversight to adapt quickly when verification logic changes.
Privacy, Data Security & Cross-Border Compliance Issues
Handling identity data in 2026 carries expectations far beyond basic protection. You are trusted with highly sensitive personal and business information, often collected across multiple jurisdictions in a single onboarding flow.
Any weakness in data handling can lead to regulatory penalties, customer churn, or lost enterprise deals. At the same time, privacy laws continue to tighten, forcing verification systems to minimize data exposure while still delivering reliable outcomes.
Below are the key privacy and security challenges shaping this area:
- Conflicting Privacy Laws Across Regions: Data collected in one country may not be legally processed or stored in another. This complicates centralized verification architectures.
- Shorter Data Retention Expectations: Regulators increasingly question how long identity data is stored and why. Retention policies must balance compliance with audit needs.
- Heightened Buyer Security Assessments: Enterprise customers now demand detailed security documentation, penetration test results, and incident response plans before onboarding vendors.
- Risk of Breaches at Verification Touchpoints: Every document upload, biometric capture, or API call becomes a potential exposure point. Securing the entire data flow is critical.
- User Consent and Transparency Requirements: Clear consent capture and explainability around data usage are now mandatory. Poor communication increases legal and reputational risk.
Scaling Infrastructure for High-Volume Onboarding
Onboarding volume in 2026 is unpredictable and often tied to product launches, partnerships, or sudden market shifts. Verification systems must handle sharp spikes without degrading performance or accuracy.
Infrastructure that works at steady volume often breaks under peak load, creating delays and failures at the worst possible time. Scaling is about maintaining consistent decision quality, uptime, and user experience as demand changes rapidly.
Below are the core infrastructure challenges that emerge at scale:
- Traffic Spikes During Campaigns or Launches: Sudden onboarding surges stress APIs, queues, and downstream services. Any bottleneck becomes immediately visible to end users.
- Latency Growth Under Load: As concurrent requests increase, response times can degrade across verification steps. Slow decisions directly impact completion rates.
- Dependency Failures Across Verification Layers: Infrastructure relies on multiple internal and external services. A single failure can cascade across the onboarding flow.
- Limited Horizontal Scalability of Legacy Components: Some verification components are not designed to scale dynamically. This restricts rapid growth without major re-architecture.
- Operational Complexity During Peak Periods: Monitoring, alerting, and incident response become harder when volume spikes. Teams need visibility to maintain reliability in real time.
Difficulties Integrating With Enterprise Legacy Systems
In 2026, many regulated businesses still run critical workflows on legacy infrastructure built long before modern APIs existed. When verification systems must plug into these environments, integration becomes a major adoption barrier.
Even strong verification capabilities can fail to deliver value if they cannot fit existing processes. Slow integrations delay go-live timelines, increase implementation costs, and create friction between product, compliance, and engineering teams.
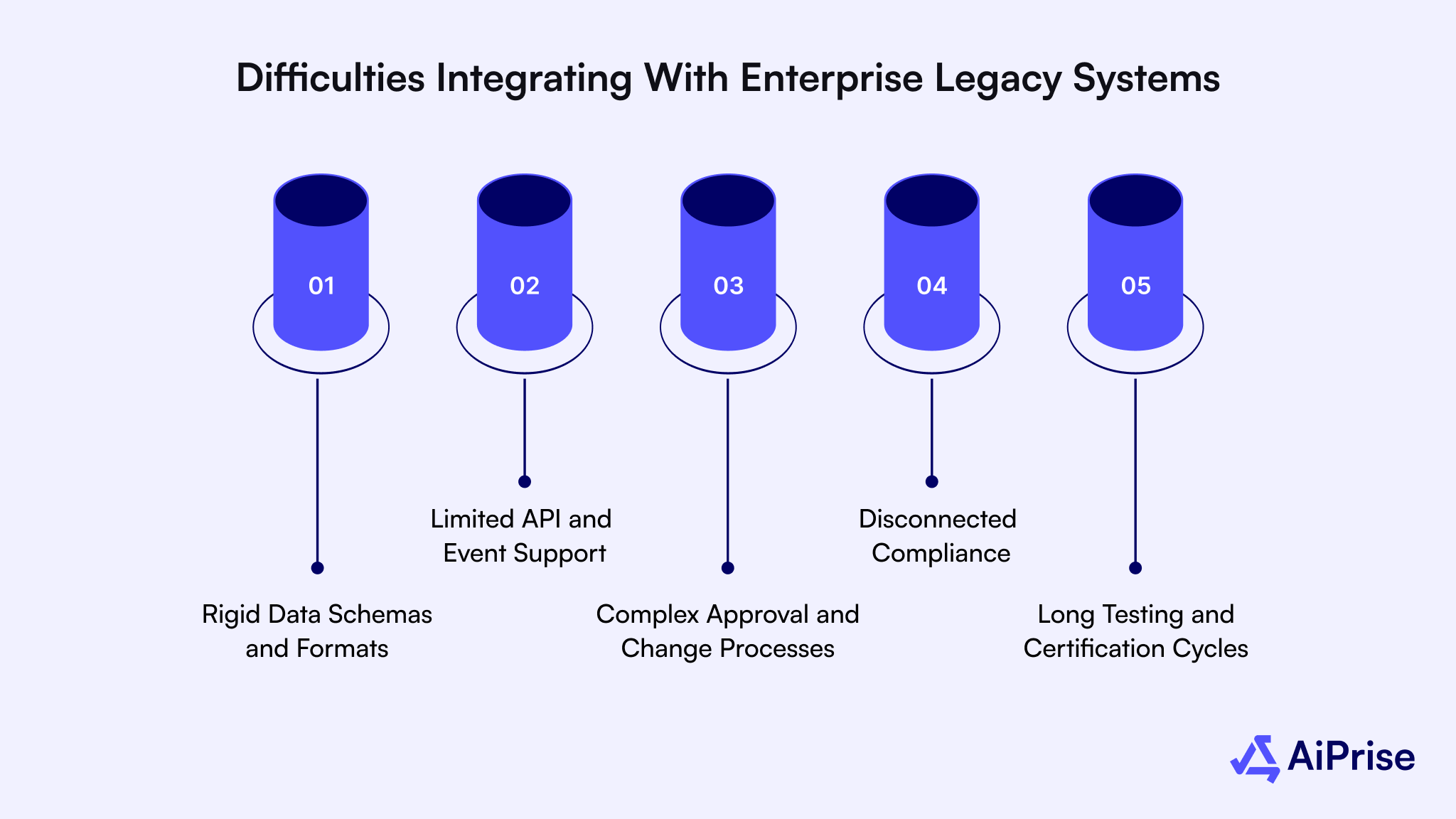
Below are the most common integration challenges encountered:
- Rigid Data Schemas and Formats: Legacy systems often require fixed field structures and naming conventions. Mapping modern verification outputs to these formats takes significant customization.
- Limited API and Event Support: Older platforms may not support webhooks or real-time callbacks. This forces polling-based workflows that slow decision-making.
- Complex Approval and Change Processes: Any system change often requires multiple internal reviews. This extends deployment timelines and increases project risk.
- Disconnected Compliance and Product Systems: Verification results may not flow cleanly into risk, CRM, or Case Management tools. Manual handoffs increase error rates.
- Long Testing and Certification Cycles: Enterprise environments demand extensive testing before production release. This delays iteration and limits rapid improvements.
As KYC startups confront these obstacles in 2026, a new wave of innovative solutions is emerging to address them.
Top 7 KYC Solutions Emerging in 2026
By 2026, KYC solutions will no longer be sold as standalone verification tools. They are built as adaptive systems that respond to risk, context, and user behavior in real time. Buyers now expect verification to function as a control layer that continuously supports onboarding, transactions, and account lifecycle events.
This shift is driven by product teams that need flexibility and compliance teams that need consistency. As a result, solution design is moving toward modular, intelligence-led architectures rather than fixed verification flows.
Below are the KYC solution categories defining this shift in 2026.
1. AI-Powered Identity Verification Platforms
In 2026, identity verification platforms powered by AI are built to make decisions, not just run checks. These systems learn from outcomes, adapt to risk signals, and improve accuracy without constant rule updates.
The value now lies in intelligence layered across the entire flow, from document capture to final approval. This matters when onboarding millions of users across products, where manual tuning is no longer realistic or sustainable.
Below are the capabilities defining modern AI-driven platforms:
- Context-Aware Decisioning: Verification outcomes adjust based on user behavior, device signals, and session patterns. Low-risk users move faster, while higher-risk cases trigger deeper checks.
- Continuous Model Learning: Models improve using feedback from approvals, rejections, and post-onboarding events. This reduces error rates over time without manual recalibration.
- Automated Exception Handling: Edge cases are resolved using probabilistic scoring instead of default rejections. This helps maintain conversion without lowering confidence thresholds.
- Fraud Signal Correlation Across Layers: Document, biometric, and behavioral signals are evaluated together. Isolated checks are replaced with holistic risk views.
- Operational Efficiency at Scale: AI reduces dependency on manual reviews, allowing onboarding volume to grow without proportional increases in compliance teams.
2. Automated KYB & UBO Verification Systems
Business onboarding in 2026 is far more complex than verifying a legal name and registration number. You are expected to understand ownership structures, control relationships, and risk exposure before accounts go live.
Manual KYB processes cannot keep pace with modern platform growth or complex entity structures. Automated KYB and UBO systems now act as decision engines that continuously validate businesses as they develop.
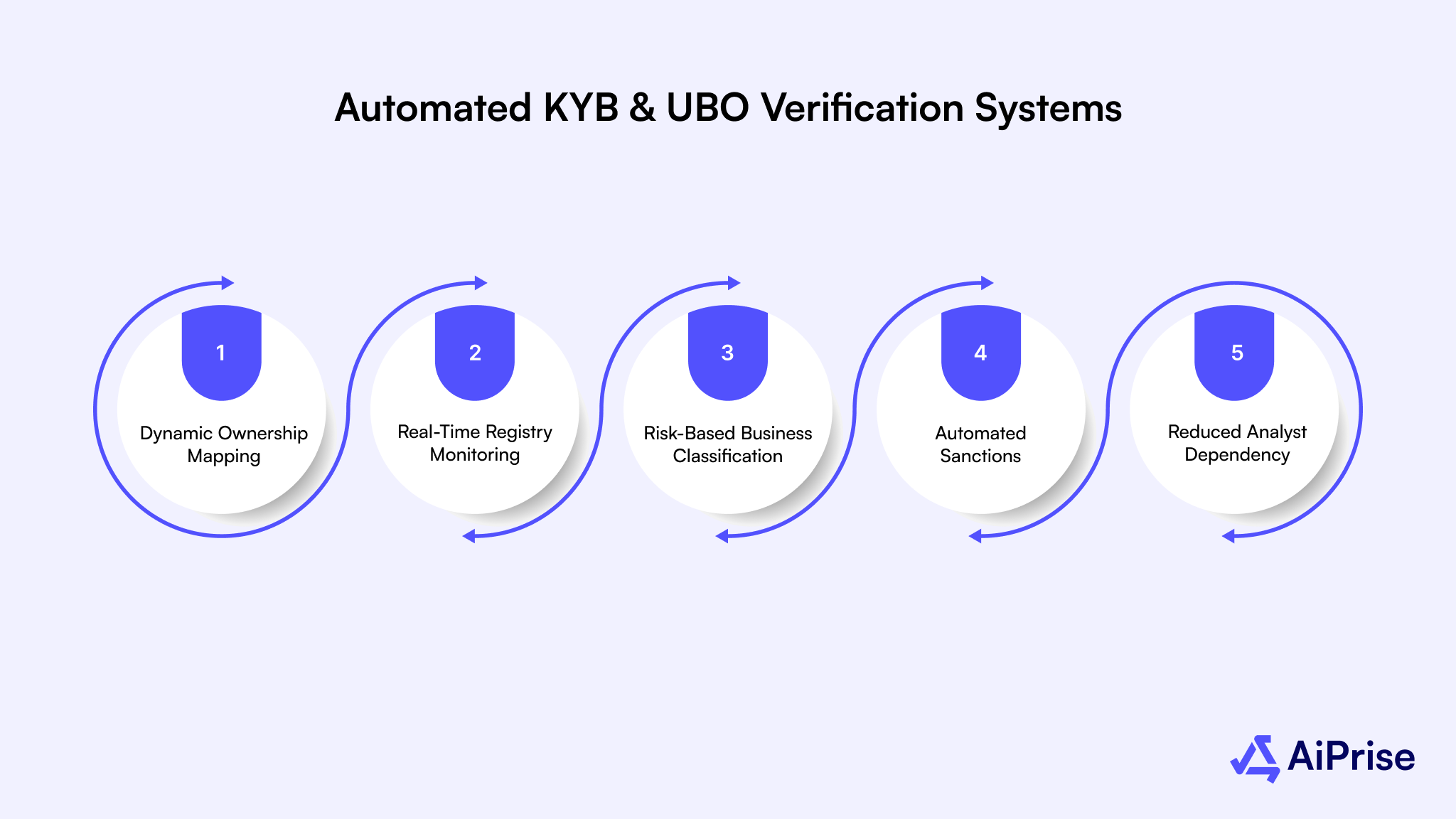
Below are the capabilities driving adoption of these systems:
- Dynamic Ownership Mapping: Corporate structures are analyzed across layers to identify ultimate beneficial owners. This is critical for onboarding marketplaces, payment processors, and crypto platforms.
- Real-Time Registry Monitoring: Changes in directors, shareholders, or legal status are detected after onboarding. This supports ongoing compliance without repeated manual checks.
- Risk-Based Business Classification: Businesses are scored based on industry, geography, and ownership patterns. Higher-risk entities trigger enhanced due diligence automatically.
- Automated Sanctions and Watchlist & Sanctions Screening: Ownership data is continuously screened against sanctions and enforcement lists. This reduces delayed risk discovery.
- Reduced Analyst Dependency: Automation replaces spreadsheet-driven reviews and document chasing. Teams can scale onboarding without growing headcount linearly.
3. Biometric Authentication (Liveness, Face Match, Voice ID)
Biometrics in 2026 are no longer a single checkpoint during onboarding. They are used as adaptive identity signals that strengthen trust across sessions and channels. When documents can be forged and credentials reused, biometric authentication helps confirm that the person behind the screen is present and genuine.
The challenge lies in applying these checks without increasing friction, especially for mobile-first users and high-frequency platforms.
Below are the biometric capabilities shaping verification strategies:
- Advanced Liveness Detection: Motion, depth, and interaction signals confirm real presence. This helps block replay attacks using photos, videos, or screens.
- Face Matching Across Sessions: Identity consistency is validated during re-verification events. This reduces account sharing and unauthorized access.
- Voice Authentication for Call-Based Flows: Voice signals support verification in support and call center interactions. This adds protection beyond digital channels.
- Device-Aware Biometric Capture: Capture quality adapts to camera and network conditions. This improves success rates across varied user environments.
- Privacy-Conscious Biometric Storage: Templates are stored securely and often tokenized. This reduces exposure while supporting repeat verification.
4. Blockchain-Based KYC for Reusable Digital Identity
By 2026, repeated verification across platforms is becoming a visible pain point for both users and businesses. Reusable digital identity models aim to reduce duplication while maintaining trust boundaries. Blockchain-based KYC introduces shared verification proofs without exposing raw identity data.
Adoption is still selective, but momentum is growing in ecosystems that rely on frequent identity validation.
Below are the key characteristics driving interest in this model:
- User-Controlled Identity Proofs: Verified credentials are held by users and shared with consent. This reduces repeated document submissions across platforms.
- Tamper-Resistant Verification Records: Blockchain ledgers provide immutable proof that checks were completed. This improves confidence during audits and disputes.
- Selective Disclosure Mechanisms: Only required attributes are shared, not full identity records. This supports privacy-first verification flows.
- Ecosystem-Based Adoption Models: Value increases when multiple platforms accept the same identity proof. Payments, wallets, and marketplaces benefit most.
- Reduced Verification Redundancy: Fewer repeated checks lower onboarding friction and operational cost over time.
5. Global ID Graphs & Real-Time Data Aggregation
In 2026, identity signals exist everywhere but rarely in one place. Global ID graphs aim to connect these signals into a unified view without relying on a single database. This matters when users interact across products, devices, and geographies within minutes.
Real-time aggregation allows identity decisions to reflect current behavior instead of static records. For platforms handling high-velocity onboarding, this approach improves confidence without adding visible friction.
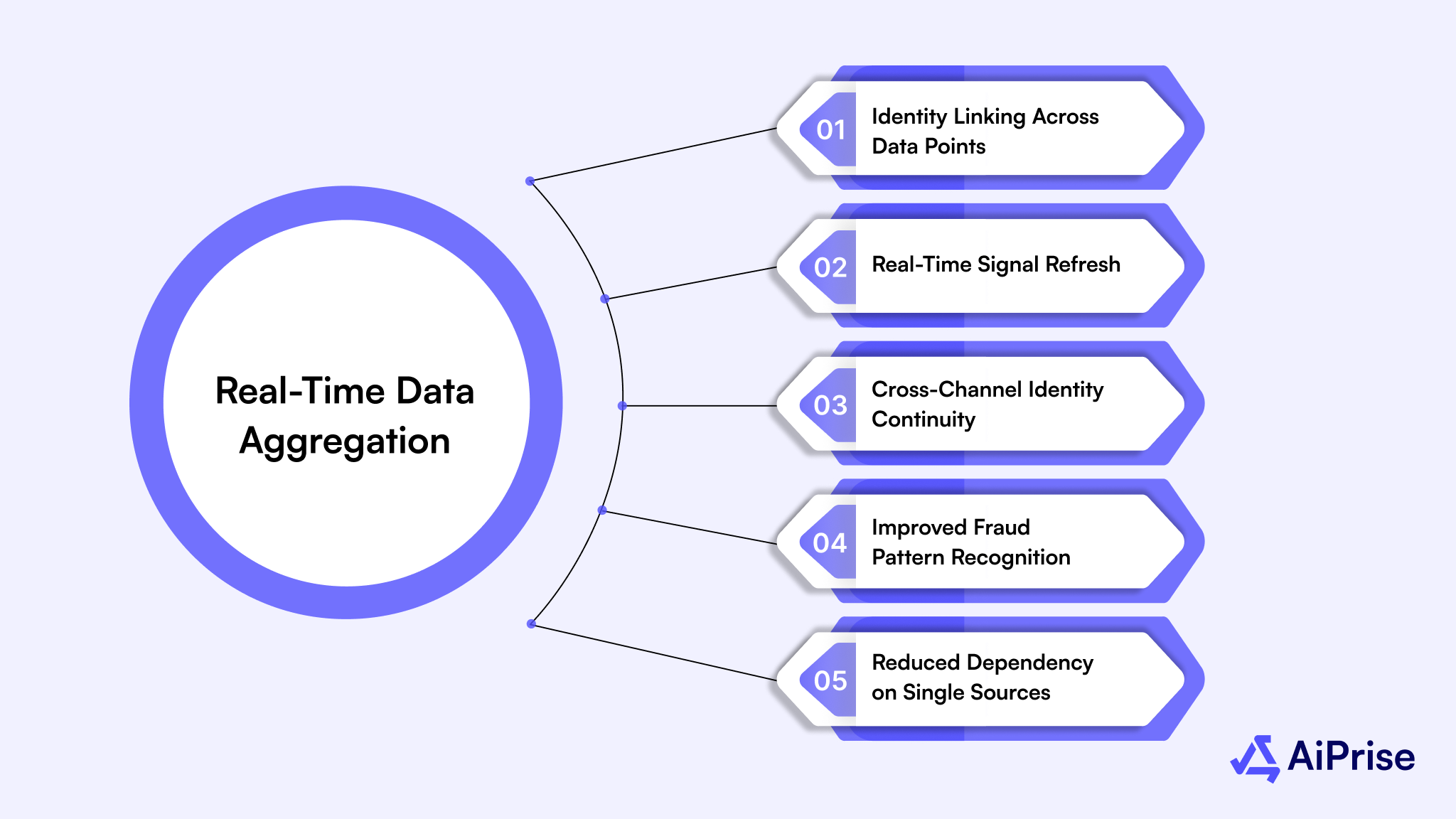
Below are the capabilities that make global ID graphs valuable:
- Identity Linking Across Data Points: Emails, phone numbers, devices, and documents are connected to form a consistent identity view. This helps detect mismatches early.
- Real-Time Signal Refresh: Decisions use live data instead of cached records. This improves accuracy during rapid onboarding or transaction spikes.
- Cross-Channel Identity Continuity: Activity across web, mobile, and support channels is correlated. This reduces blind spots during re-verification.
- Improved Fraud Pattern Recognition: Linked data reveals repeated behavior across accounts or platforms. This strengthens early identity fraud detection.
- Reduced Dependency on Single Sources: Aggregation minimizes risk when one provider fails or returns incomplete data.
6. Risk Scoring Engines With Behavioral Analytics
Static identity checks cannot explain how risk changes after onboarding. In 2026, risk scoring engines rely on behavioral analytics to evaluate intent, not just credentials. This allows identity trust to develop based on how users interact with your product.
Behavioral signals add depth to decision-making, especially for platforms where account misuse appears days or weeks after approval. The focus shifts from pass or fail decisions to continuous risk awareness.
Below are the core capabilities driving these engines:
- Behavior-Based Risk Adjustments: Login patterns, transaction timing, and navigation behavior influence risk scores. Unusual changes trigger adaptive responses.
- Early Detection of Account Takeover Signals: Sudden shifts in device or usage behavior are flagged quickly. This reduces downstream fraud impact.
- Adaptive Threshold Management: Risk thresholds shift based on current behavior instead of fixed rules. This improves accuracy over time.
- Reduced Dependence on Heavy Upfront Checks: Initial onboarding can remain light while monitoring continues post-approval. This balances user experience with protection.
- Actionable Risk Outputs for Operations: Scores translate into clear actions such as step-up verification or review. This helps teams respond consistently.
7. Video KYC and Agent-Assisted Verification Innovations
Video-based verification in 2026 is no longer limited to manual face checks over a call. It has developed into a hybrid model that combines automation with human oversight for high-risk or regulated use cases.
Video KYC offers a controlled environment where identity intent, document ownership, and live presence can be validated with higher confidence.
Below are the innovations shaping modern video KYC workflows:
- Hybrid Human and AI Verification: AI pre-screens sessions while agents intervene only when needed. This improves efficiency without losing judgment quality.
- On-Demand Agent Availability: Verification sessions can be triggered dynamically for flagged users. This avoids forcing all users through video flows.
- Structured Agent Decision Frameworks: Agents follow standardized prompts and scoring logic. This reduces subjectivity and improves audit readiness.
- Integrated Document and Biometric Review: Live document checks are combined with biometric confirmation. This strengthens confidence for complex cases.
- Regulator-Friendly Verification Records: Session recordings and decision logs are securely stored. This supports audits and dispute resolution.
These leading KYC solutions are closely tied to the broader technology trends reshaping the KYC scene in 2026.
Key Technology Trends Transforming KYC in 2026
KYC technology in 2026 is shaped by how quickly risk develops after onboarding. Verification is no longer a single event tied to account creation. It is embedded across user journeys, transactions, and account lifecycle decisions.
Technology choices now determine how well trust signals adapt over time without disrupting customer experience. For regulated platforms, these trends directly influence approval rates, fraud losses, and regulatory confidence.
Below are the technology trends redefining how KYC operates in 2026:
- Multi-Modal Identity Signal Fusion: Identity decisions combine documents, biometrics, device data, and behavior. This creates stronger confidence without adding visible steps.
- Privacy-First Verification Architectures: Systems are designed to minimize data exposure while maintaining verification strength. This supports stricter privacy expectations.
- Event-Driven Verification Triggers: Checks activate based on behavior or risk events, not fixed timelines. This aligns verification with real usage patterns.
- Explainable AI for Compliance Teams: Decision logic is transparent and traceable. This helps during audits and regulatory reviews.
- Cloud-Native Verification Infrastructure: Elastic infrastructure supports rapid scaling and global availability. This improves resilience during traffic spikes.
Also read: Deepfake Selfie Verification in Identity Checks.
These transformative KYC technologies are shifting in response to shifting compliance requirements that increasingly shape how startups operate.
Compliance Requirements Affecting KYC Startups
Compliance expectations in 2026 are shaping how KYC products are built, sold, and evaluated. It is no longer enough to support basic regulatory checks. Platforms are expected to demonstrate consistency, transparency, and accountability across every verification decision.
Buyers now assess compliance readiness before technical features. This shifts compliance from a backend requirement to a core product differentiator that directly influences sales cycles and long-term partnerships.
Below are the compliance requirements most affecting KYC startups today:
- Multi-Regulator Alignment Across Jurisdictions: Rules from bodies like FATF, FinCEN, GDPR, and CCPA overlap but rarely align perfectly. Your systems must satisfy multiple interpretations at the same time.
- Audit-Ready Verification Decisions: Every approval or rejection must be traceable. Clear logs and decision rationale are required during regulatory reviews and enterprise audits.
- Explainability of Automated Decisions: AI-driven KYB outcomes must be understandable to compliance teams. Black-box decisions increase regulatory risk and buyer hesitation.
- Data Localization and Residency Obligations: Some regions require identity data to stay within national borders. This impacts infrastructure design and vendor selection.
- Ongoing Monitoring Expectations: Compliance does not stop at onboarding. Continuous screening and periodic reviews are increasingly expected across regulated sectors.
As compliance pressures intensify, businesses must apply a clear evaluation framework when selecting KYC startup partners.
Choosing the Right KYC Startup: An Evaluation Framework
Choosing a KYC startup in 2026 directly affects growth velocity, compliance confidence, and fraud exposure. The wrong choice creates hidden friction that surfaces during audits, traffic spikes, or market expansion. Evaluation must go beyond feature checklists and focus on how well the solution fits real operational conditions. The goal is not just passing onboarding today, but supporting trust as your product and risk profile develop.
Below is a practical framework to guide evaluation:
- Speed, Accuracy, and Stability Under Load: Measure decision time during peak onboarding, not demos. Consistent performance matters more than average latency.
- Coverage Across Countries, Documents, and Entities: Verify supported geographies, ID types, and business structures. Gaps become blockers during expansion.
- Integration Effort and Time to Value: APIs, SDKs, and webhooks should fit existing workflows. Long setup cycles slow product launches.
- Risk Controls and Customization Depth: The Ability to adjust thresholds, flows, and escalation logic is critical. Fixed rules limit adaptability.
- Cost Transparency And Scalability: Understand pricing per outcome, not per API call. Costs should scale predictably with growth.
Struggling to onboard customers fast without increasing compliance risk or false rejections? AiPrise simplifies customer verification with its AI-powered KYC solution built for regulated, high-growth platforms. Risk-based onboarding with global identity coverage and audit-ready workflows.
Using this evaluation framework, it becomes clearer where AiPrise fits within the shifting KYC startup scene and how it differentiates itself.

A Unified KYC Platform Built for Regulated Growth
In a market where verification tools are expected to act as trust infrastructure, differentiation comes from how well systems adapt to risk, scale, and regulation together. Modern platforms need more than point solutions.
They need unified intelligence that reduces operational drag while improving compliance confidence. This is where a consolidated approach becomes critical for fintechs, payment providers, and crypto platforms operating across regions and risk tiers.
Below is how AiPrise fits directly into these needs:
- Unified KYC, KYB, AML, and Fraud Risk Operations: Instead of managing disconnected tools, AiPrise brings KYC, KYB, AML, and fraud risk management into a single automated platform. This reduces duplicate checks, simplifies compliance workflows, and improves visibility across customer and business onboarding.
- Global Verification With Regulatory Awareness: Coverage across countries and data sources is paired with built-in compliance logic. AiPrise helps maintain alignment with shifting US and global regulations without constant rule rebuilding.
- AI-Driven Accuracy Without Slowing Onboarding: Advanced AI and ML models improve match accuracy while keeping flows fast. AiPrise supports risk-based verification that adapts to user and business context.
- Scalable Infrastructure For High-Growth Platforms: High-volume onboarding is supported through automation-first design. AiPrise helps platforms scale verification without increasing manual review dependency.
- Audit-Ready And Explainable Decisioning: Clear logs, traceable decisions, and compliance reporting are embedded into workflows. AiPrise supports smoother audits and enterprise risk reviews.
By combining verification, compliance, and risk intelligence into one system, AiPrise helps businesses move from basic identity checks to scalable trust infrastructure.
Final Thoughts
KYC startups in 2026 sit at the center of trust, growth, and regulation. Verification is no longer a background process. It directly shapes onboarding success, fraud exposure, and regulatory confidence. As identity risks grow more complex, businesses need solutions that adapt in real time, scale without friction, and remain audit-ready across markets.
AiPrise supports this shift by combining KYC, KYB, AML, and fraud risk management into a single, intelligent platform built for global scale. With AI-driven verification, regulatory alignment, and automation-first workflows, AiPrise helps businesses reduce risk while maintaining fast, reliable onboarding.
Ready to strengthen trust without slowing growth? Book A Demo to see how AiPrise can support your compliance and verification needs in 2026 and beyond.
FAQs
1. What is the difference between KYC startups and traditional KYC vendors?
KYC startups focus on automation, APIs, and real-time decisioning, while traditional vendors rely more on manual reviews and fixed workflows. Startups are built for digital-first onboarding, faster integrations, and scalability. This makes them better suited for fintechs, crypto platforms, and high-growth businesses.
2. Are KYC startups suitable for highly regulated industries like banking and insurance?
Yes, many KYC startups are designed specifically for regulated industries. They support audit trails, explainable decisions, and ongoing monitoring. Banks and insurers often adopt these solutions to modernize onboarding while meeting regulatory expectations and reducing operational overhead.
3. How long does it take to implement a modern KYC solution?
Implementation timelines vary based on integration complexity and internal systems. API-first KYC startups can often be integrated within weeks rather than months. Faster time to value is one of the main reasons businesses move away from legacy verification providers.
4. Can KYC startups support both individual and business verification in one flow?
Many modern KYC platforms support unified KYC and KYB workflows. This allows platforms to verify individuals, businesses, and beneficial owners within a single onboarding journey. It is especially useful for marketplaces, payment processors, and B2B fintech products.
5. How do KYC solutions handle ongoing monitoring after onboarding?
Ongoing monitoring includes periodic rechecks, sanctions screening, and behavior-based risk reviews. Instead of redoing full verification, systems monitor changes in risk signals. This helps businesses stay compliant while minimizing disruption to active customers.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.





Speed Up Your Compliance by 10x
Automate your compliance processes with AiPrise and focus on growing your business.





.jpeg)


.jpg)















.jpeg)










.png)














.png)






















