AiPrise
10 min read
September 23, 2025
Understanding KYC Verification Safety and Prevention Steps
Key Takeaways










How confident are you that the person you’re doing business with online is who they say they are?
With identity theft and fraud on the rise, this question has never been more critical. In fact, in 2024 alone, financial crime compliance costs hit $61 billion, as businesses grapple with increasing fraud risks and complex regulations.
KYC (Know Your Customer) verification has emerged as a key tool in protecting businesses from fraud, money laundering, and other criminal activities. But as with any data-sharing process, the question arises: Is KYC verification safe?
In this article, we’ll take a closer look at the KYC verification process, the scams targeting businesses, and actionable steps you can take to protect both your organization and its customers.
Key Takeaways:
- KYC verifies customer identities to prevent fraud and financial crimes.
- It involves identification, due diligence, enhanced checks, and ongoing monitoring.
- Common KYC scams include fake documents, identity theft, and social engineering.
- Businesses must use secure systems and AI tools to detect and prevent fraud.
- KYC is an ongoing process, requiring continuous monitoring and adaptation.
What is KYC Verification?
KYC or Know Your Customer is a process designed to protect both businesses and customers by ensuring that identities are legitimate before entering into any transactions. It’s a vital step for companies, especially in industries like banking, finance, and e-commerce, to prevent illegal activities.
At its core, KYC verification is about trust. Before any service is provided or a transaction is processed, businesses need to verify the identity of their customers to make sure they are who they claim to be.
But what does KYC actually involve?
It’s a multi-step process that ensures your identity is verified across several layers. Here’s a breakdown of what goes into the KYC process:
- Customer Identification: This is the first step where businesses collect basic personal information like your full name, date of birth, address, and government-issued ID number (e.g., a passport or driver’s license). It’s all about confirming your identity with official records.
- Customer Due Diligence (CDD): Once the basic identification is done, businesses assess the risk level associated with the customer. This includes reviewing transaction histories, business activities, and overall financial behavior. This helps ensure that the customer isn’t involved in any suspicious or illegal activities.
- Enhanced Due Diligence (EDD): For higher-risk customers, those with unusual transaction histories or who come from high-risk regions, businesses conduct deeper checks. This can involve background investigations, looking at financial stability, and even monitoring for suspicious transactions.
- Ongoing Monitoring: KYC doesn’t end after the first check. It’s an ongoing process. Businesses need to continue ongoing monitoring for any signs of suspicious activity or changes in their risk profile. If something seems off, further verification may be required.
While a verification check might seem like just another bureaucratic hurdle, it’s actually one of the best tools businesses have to protect themselves from fraud, ensure compliance, and build trust with customers. Let’s take a closer look at some of the most commonly used tactics by scammers, so you can learn how to spot and prevent them.
Common Tactics Used in KYC Scams
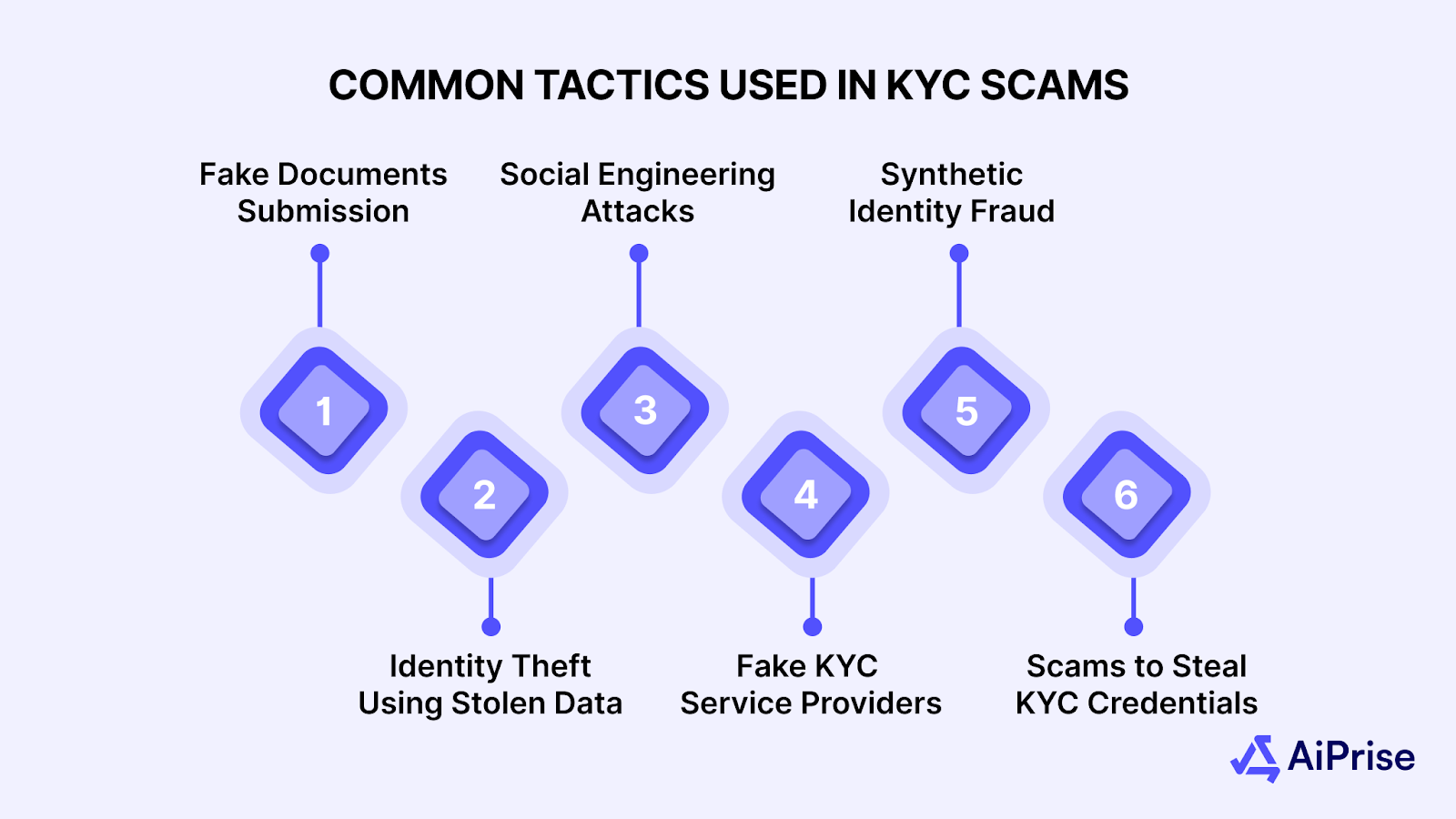
KYC (Know Your Customer) verification is essential for preventing fraud, but it’s also a common target for scammers. Understanding these scams is the first step in protecting both your business and your customers from falling victim to them. Here are some of the most common tactics used in KYC scams:
1. Fake Documents Submission
One of the most common scams involves submitting forged or altered documents during the KYC process. Fraudsters often use high-quality software to create fake IDs, passports, and utility bills that appear legitimate. These documents can be difficult to distinguish from authentic ones, especially if they are cleverly designed to mimic real government-issued IDs.
How to Spot It:
- Cross-check documents with trusted databases or use advanced verification systems to spot inconsistencies in the document's text, fonts, or images.
- Look for signs of tampering, such as blurry text or distorted photos.
2. Identity Theft Using Stolen Data
Scammers often obtain personal information from data breaches or phishing attacks and use it to create fake KYC profiles. These stolen identities are then used to bypass the KYC process, enabling fraudsters to carry out illegal activities such as money laundering or financial scams.
How to Spot It:
- Use multi-factor authentication (MFA) to add extra layers of security.
- Regularly monitor accounts for suspicious activities that could indicate the use of stolen identities.
3. Social Engineering Attacks
Scammers may attempt to manipulate or deceive employees by pretending to be legitimate customers. This could involve phone calls, emails, or even in-person interactions where the scammer impersonates a customer to gain access to sensitive KYC data. These scams often rely on psychological manipulation to get staff to skip verification procedures.
How to Spot It:
- Train employees to recognize social engineering tactics and establish clear protocols for verifying customer identity before providing access to sensitive data.
- Encourage skepticism and always follow security procedures, even if the request seems urgent or genuine.
4. Fake KYC Service Providers
Fraudsters sometimes create fake KYC service providers, offering businesses a "faster" or "cheaper" solution to handle identity verification. These fake providers may steal data from customers without actually performing the verification, putting both the business and its customers at risk.
How to Spot It:
- Ensure that the KYC service provider is reputable and has established security measures.
- Verify the provider's credentials, check their compliance with data protection regulations (e.g., GDPR), and seek reviews or certifications from trusted organizations.
5. Synthetic Identity Fraud
Synthetic identity fraud occurs when criminals combine real and fake information to create a new, fictitious identity. This can involve using a real name and combining it with fake address details, birthdates, or even social security numbers. Since the identity is based on a mix of real and false information, it can be hard to detect using standard KYC checks.
How to Spot It:
- Use advanced machine learning and AI tools to detect synthetic identity patterns.
- Cross-check provided information with multiple databases to look for discrepancies or unusual combinations of data.
6. Phishing Scams to Steal KYC Credentials
Phishing attacks target customers by tricking them into providing their KYC-related information, often through fake emails or websites that look like legitimate KYC portals. Once the scammer has access to the data, they can use it for fraud or identity theft.
How to Spot It:
- Always double-check website URLs and ensure secure HTTPS connections when handling KYC submissions.
- Educate customers to recognize phishing emails or messages and encourage them to report suspicious communications.
Now that we’ve covered the common scams, let’s turn to practical steps individuals can take to protect their KYC data.
Steps for Individuals to Protect Their KYC Data
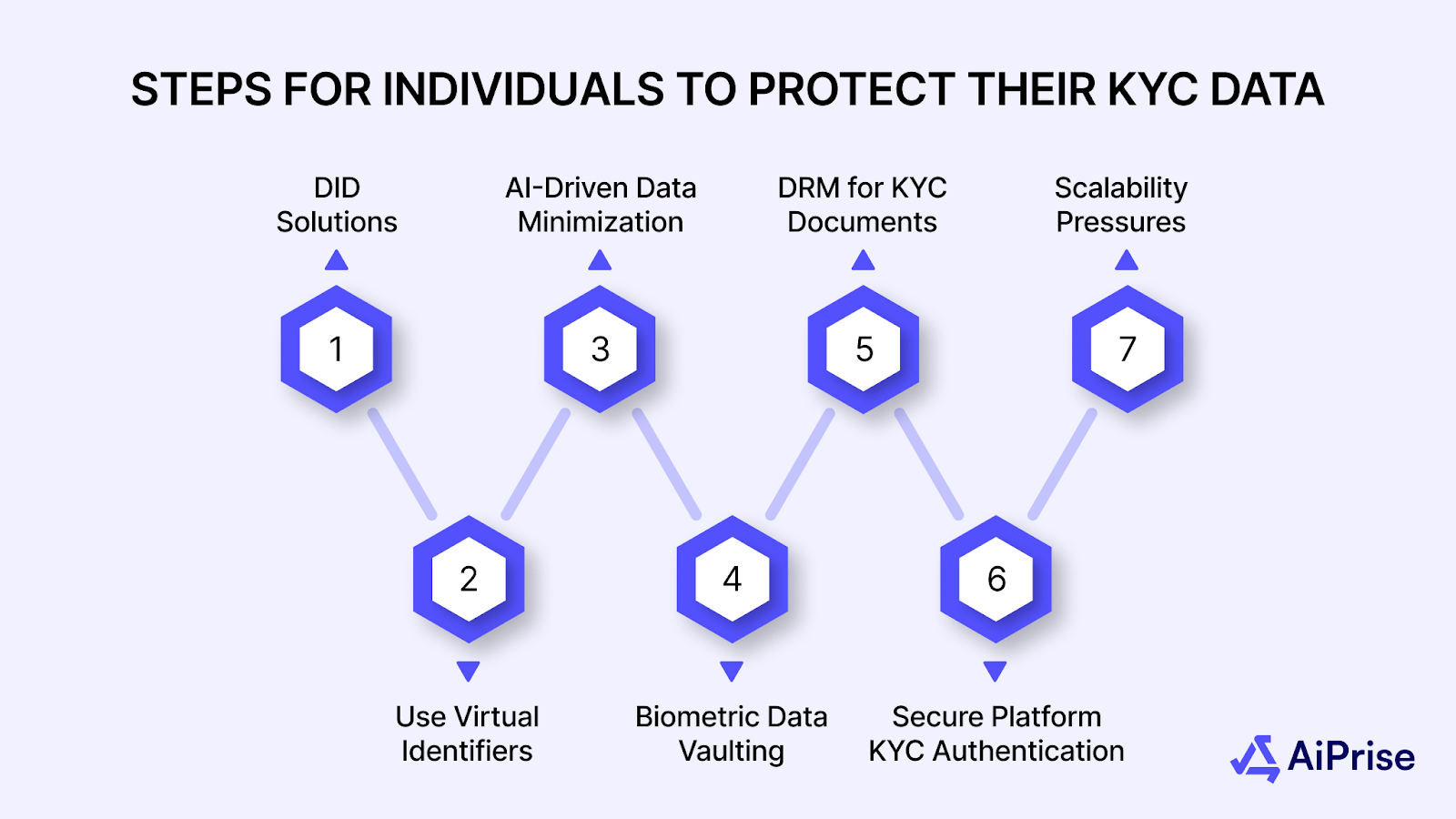
KYC data, which includes sensitive personal information, can be a prime target for cybercriminals. Whether it’s your bank account, government-issued IDs, or personal details, protecting your KYC data is crucial to preventing identity theft and fraud. Here are some essential steps individuals can take to secure their KYC data:
1. Use Decentralized Identity (DID) Solutions
Decentralized Identity (DID) is a cutting-edge technology that allows individuals to have full control over their own identity data without relying on a central authority. With DID, personal information such as your name, address, and government IDs are stored on a blockchain, where you can selectively share them only when necessary, keeping the data secure and private.
- Tip: Adopt a Self-Sovereign Identity (SSI) model where you can store and manage your KYC data digitally in a secure, blockchain-based wallet.
2. Use Virtual Identifiers for KYC Interactions
Instead of providing your real name or personal details, use virtual identifiers (such as pseudonyms or encrypted identification) during online KYC interactions. These identifiers act as placeholders, allowing you to retain your privacy while still completing the verification process.
- Tip: Use a temporary email address or disposable phone number when interacting with platforms that require KYC, ensuring your primary contact information remains private.
3. AI-Driven Data Minimization
Using artificial intelligence (AI) tools, you can opt for data minimization, the practice of only sharing the absolute minimum amount of personal information required to complete the KYC process.
AI systems can analyze requests in real-time and determine which information is necessary for verification, filtering out unnecessary data before submission.
4. Biometric Data Vaulting
Instead of allowing third-party services to store your biometric data, use biometric data vaulting, a secure method where your biometric data (like fingerprints or facial recognition) is stored locally on your device or a secure vault. This prevents unauthorized access to your sensitive biometric data, as it's not shared with anyone except trusted entities.
- Tip: Store biometric information in hardware security modules (HSMs) or encrypted devices for added protection and only share biometric data when absolutely necessary.
5. Digital Rights Management (DRM) for KYC Documents
Incorporate Digital Rights Management (DRM) technology to protect your digital KYC documents.
DRM tools can help control how your documents are accessed, shared, and used, adding an additional layer of protection by restricting copying, forwarding, or unauthorized distribution. Use DRM-protected PDFs or files that allow only authorized individuals or platforms to access your KYC data, and track who views or downloads it.
6. Data Anonymization for Risk Assessment
Before sharing your KYC data with online platforms, you can anonymize certain parts of the data, removing personally identifiable information that is not necessary for the verification process. This allows you to keep your identity partially concealed while still verifying essential aspects of your data.
7. Use Secure, Multi-Platform Authentication for KYC Submissions
Ensure that KYC submissions across platforms require multi-platform authentication.
Instead of just using your phone for verification, link your KYC process across devices like your smartphone, laptop, or a trusted device like a hardware key for added security. This ensures that even if one device is compromised, the verification process is still protected.
In addition to individual protection, businesses can further strengthen their KYC processes by integrating advanced technologies. Let’s explore how tools like AiPrise can assist in safeguarding against fraud.
Strengthen Your Security with AiPrise
As digital identity theft and fraud continue to evolve, businesses need to stay one step ahead in their KYC verification process.
AiPrise offers state-of-the-art, AI-powered solutions designed to streamline identity verification and fraud prevention, ensuring that only legitimate customers and merchants are onboarded. Our comprehensive KYC, AML, and fraud detection tools provide your business with the security, accuracy, and compliance necessary to operate safely in a rapidly changing digital landscape.
AiPrise Features Include:
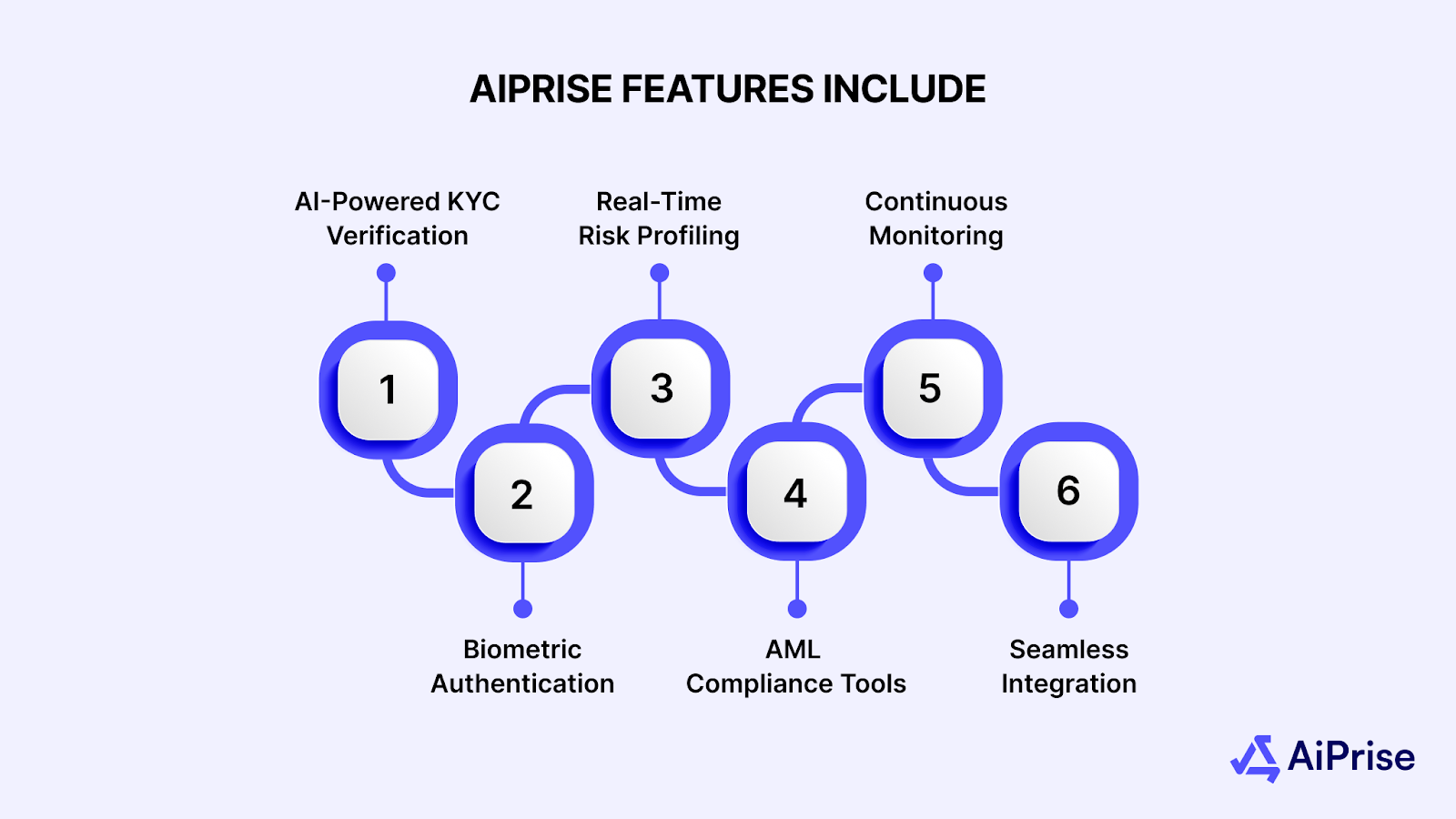
- AI-Powered KYC Verification: Automatically validate identity documents and cross-check data with official sources for unmatched accuracy.
- Biometric Authentication: Implement facial recognition, fingerprint scanning, and other biometric methods to ensure secure, multi-layered customer verification.
- Real-Time Risk Profiling: Use AI to assess the risk level of each customer or merchant based on transaction patterns and historical data.
- AML Compliance Tools: Screen customers against global watchlists, ensuring compliance with Anti-Money Laundering (AML) regulations and preventing financial crimes.
- Continuous Monitoring: Monitor transactions and behaviors in real-time to flag suspicious activity and ensure ongoing compliance.
- Seamless Integration: Easily integrate AiPrise’s KYC and fraud detection tools with your existing systems via customizable APIs and no-code SDKs.
Take action today and partner with AiPrise to ensure the integrity of your identity verification processes.
Conclusion
As online security threats evolve, KYC verification plays an increasingly crucial role in ensuring businesses maintain a secure environment for their customers. By following best practices and implementing advanced security technologies, businesses can safeguard their systems, maintain compliance, and protect against fraudulent activities.
To bolster your KYC verification process and ensure maximum safety for your business, AiPrise provides AI-powered KYC solutions that streamline identity verification while adhering to global compliance standards. Book A Demo with AiPrise today to discover how we can help you protect your business and customers from identity theft and fraud.
FAQs
1. How often should businesses update their KYC procedures?
Businesses should update their KYC processes regularly to account for new fraud tactics, regulatory changes, and emerging technologies.
2. What are the legal consequences of non-compliance with KYC regulations?
Non-compliance can result in significant fines, legal action, reputational damage, and loss of business licenses, depending on the jurisdiction.
3. Can KYC verification be outsourced to third-party providers?
Yes, businesses can outsource KYC processes to trusted third-party providers, but they must ensure these providers comply with applicable regulations and have strong data protection measures in place.
4. How does KYC affect customer experience during onboarding?
While KYC is necessary for security, businesses should aim to streamline the process to minimize customer friction, using technologies like biometric verification for faster onboarding.
5. Is KYC only required for financial institutions?
No, KYC is also required by other industries such as e-commerce, real estate, and telecommunications, especially in cases where transactions involve large sums or sensitive data.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.










.jpeg)


.jpg)
















.jpeg)










.png)














.png)




















