AiPrise
10 min read
September 23, 2025
Understanding KYC to Prevent Identity Theft

Key Takeaways










In 2024, identity theft surged to unprecedented levels, with over 1.1 million reports filed through the FTC's IdentityTheft.gov website alone. This marks a massive uptick from previous years, underscoring the escalating threat to individuals and businesses alike.
As cybercriminals employ increasingly sophisticated tactics, such as deepfakes and AI-driven scams, the need for robust identity verification processes has never been more necessary. This is where Know Your Customer (KYC) protocols come into play, serving as a frontline defense against identity theft.
This article will explore how KYC works, its role in preventing identity theft, and why businesses must implement robust KYC practices to stay protected.
Key Takeaways
- KYC (Know Your Customer) is a regulatory process for verifying the identity of customers to prevent identity theft and fraud.
- It involves collecting personal data such as government-issued IDs and proof of address to verify customer identity.
- KYC helps identify fraudulent and synthetic identities early, protecting businesses from financial losses and reputational damage.
- The KYC process is continuous, requiring ongoing monitoring of customer behavior to detect and prevent suspicious activities.
- Implementing KYC not only builds trust with customers but also ensures compliance with global regulatory standards, protecting businesses from legal and financial repercussions.
What is KYC?
KYC (Know Your Customer) is a global regulatory process used by businesses, to verify the identity of their customers. The primary goal of KYC is to prevent fraud, identity theft, and money laundering by ensuring that businesses know who they are dealing with before engaging in any transaction or offering services.
KYC is a crucial step in complying with international regulations and establishing trust between businesses and customers. It involves collecting a range of personal and financial information to assess the identity of individuals or organizations. The KYC process is widely adopted by banks, financial institutions, insurance companies, and even cryptocurrency platforms to ensure a secure environment.
The key steps in the KYC process typically include:
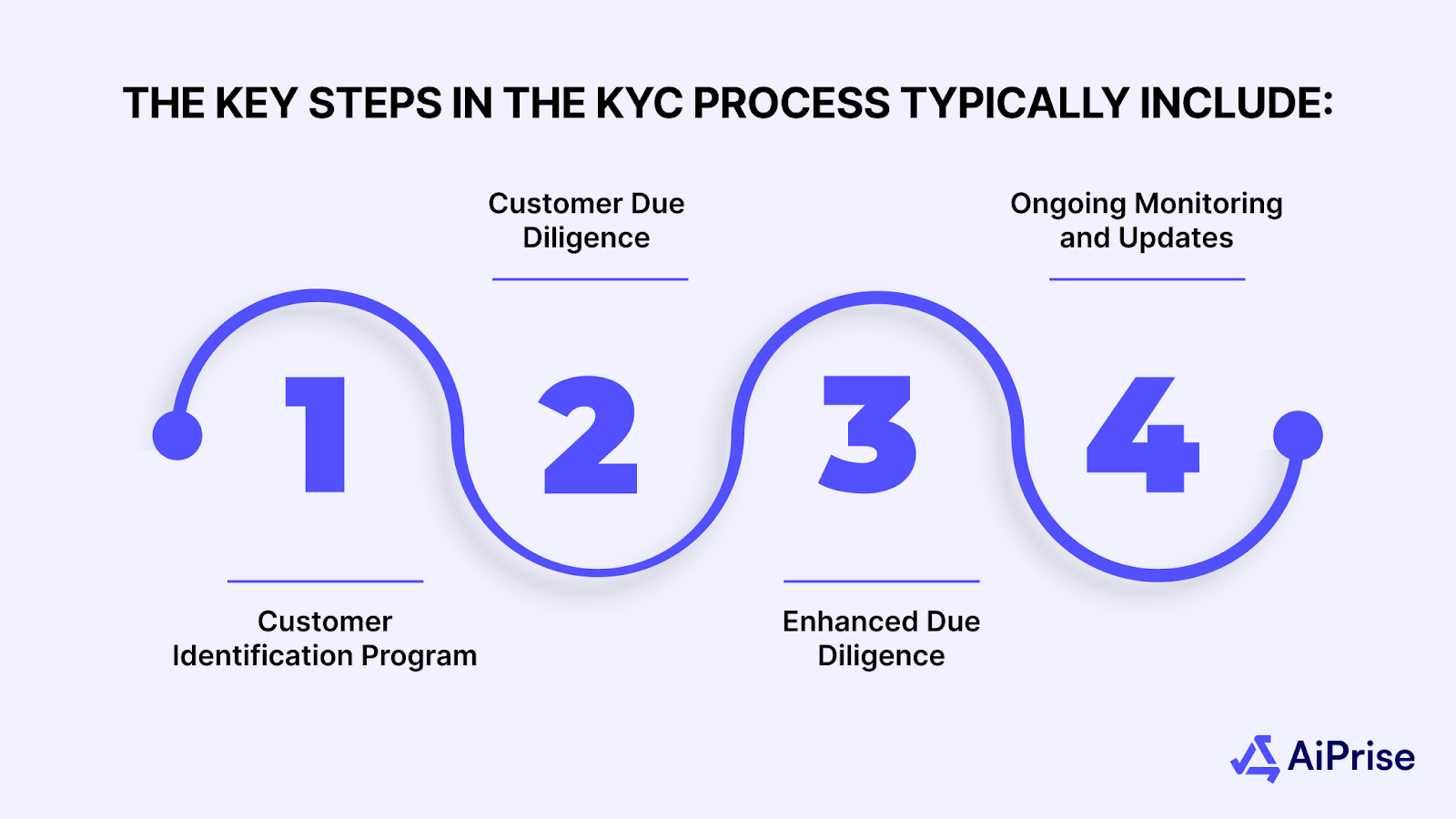
1. Customer Identification Program (CIP)
The first step in KYC involves gathering basic information to confirm the identity of the customer. This includes:
- Full name
- Date of birth
- Residential address
- Government-issued ID number (e.g., passport number, national ID, or driver’s license)
Businesses will often cross-check this information against trusted databases to verify its authenticity. This ensures that the customer’s identity is legitimate and that they are not involved in illegal activities.
2. Customer Due Diligence (CDD)
After the identification phase, businesses perform Customer Due Diligence (CDD) to assess the customer’s risk profile. This due diligence process involves analyzing the customer's:
- Nature of business or occupation
- Transaction history
- Financial activity to ensure it aligns with their known financial status
CDD helps businesses identify high-risk customers, such as those who may be involved in fund laundering or terrorism financing. The level of due diligence applied varies based on the perceived risk of the customer.
3. Enhanced Due Diligence (EDD)
For higher-risk customers—such as politically exposed persons (PEPs), individuals with a history of financial crime, or customers from high-risk regions—businesses perform Enhanced Due Diligence (EDD). EDD involves deeper scrutiny, including:
- In-depth background checks
- Monitoring for unusual transaction patterns
- Periodic re-verification of customer information
This additional diligence is crucial for mitigating the risk of engaging with customers who could potentially use the business for illegal activities.
4. Ongoing Monitoring and Updates
KYC is not a one-time process; it requires continuous monitoring of customer activity and periodic updates. This ensures that any changes in a customer’s behavior, such as large transactions or a sudden change in activity, are flagged for review. Continuous monitoring helps businesses detect potential fraud or suspicious activity early, preventing identity theft and other financial crimes.
Across the globe, KYC regulations vary based on local laws but adhere to common international standards set by organizations like the Financial Action Task Force (FATF). These regulations help create a universal framework for anti-money laundering (AML) efforts. While the specific requirements can differ between countries, the basic principles of KYC remain consistent: verifying the identity of customers, assessing their risk level, and ensuring compliance with financial security standards.
Now that we’ve established what KYC is, it’s important to understand how KYC specifically works to prevent identity theft and other financial crimes.
Read: Understanding Fraud: Patterns and Prevention Strategies
How KYC Helps Prevent Identity Theft
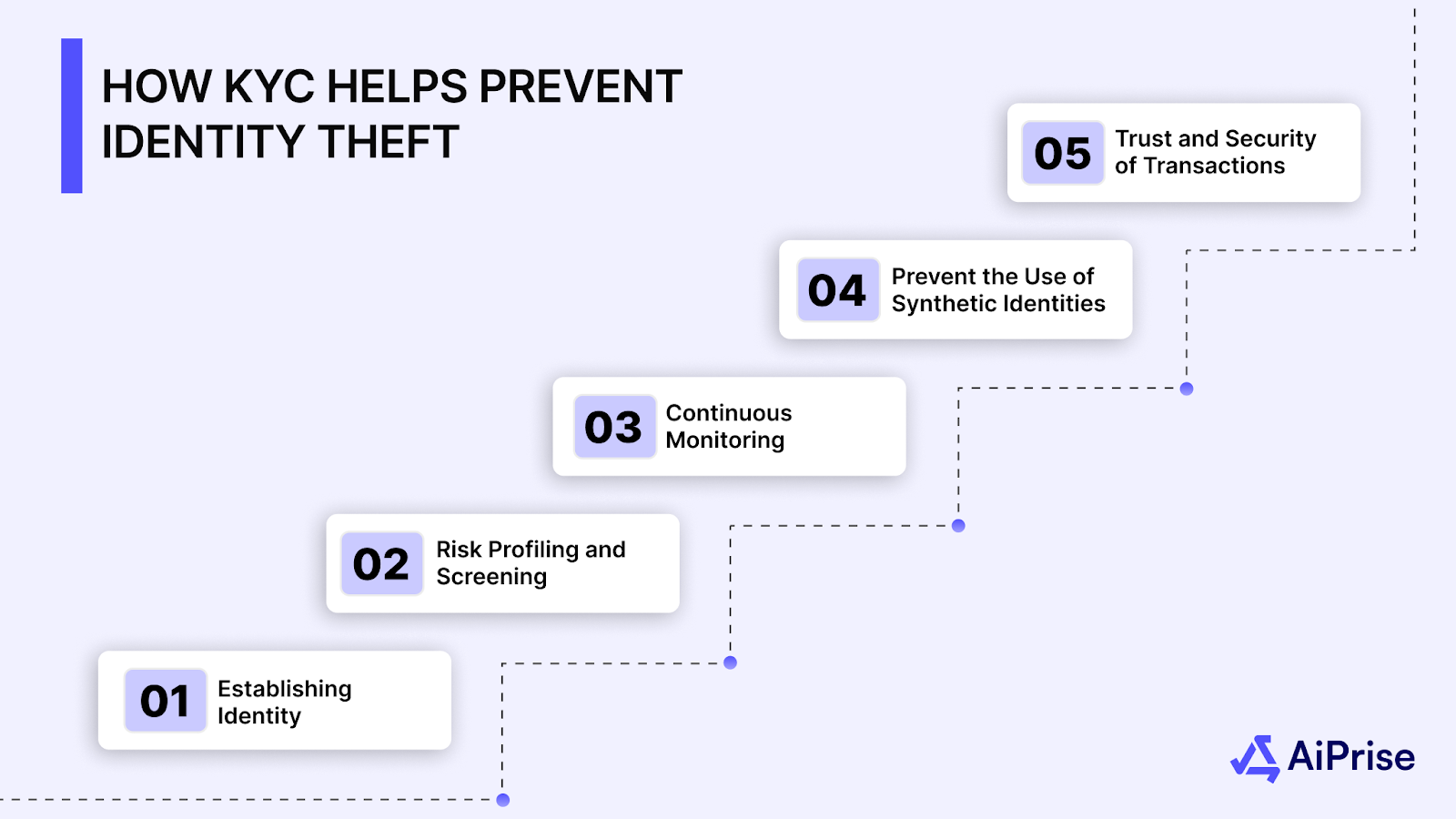
KYC (Know Your Customer) plays a vital role in protecting identities by ensuring that only legitimate individuals or entities gain access to services, especially in industries like banking, finance, and insurance. Here's how KYC prevents identity theft:
1. Establishing Identity with Reliable Documentation
One of the first steps in the KYC process is collecting personal information, such as government-issued IDs, that can be cross-checked with official records. This verification helps detect fake identities before they are used for fraudulent activities. If there’s a mismatch between the documents presented and trusted databases, the transaction is flagged, preventing unauthorized access.
- Tip: Ensure that the ID documents are validated against official sources like government registries and public records.
2. Risk Profiling and Screening
Through Customer Due Diligence (CDD), businesses assess the risk level of customers, identifying suspicious patterns in their activities or backgrounds. This step ensures that businesses are not engaging with individuals who could be using stolen or falsified identities to carry out fraud. KYC also involves screening for potential connections to illegal activities, such as money laundering or terrorism financing, which are often associated with identity theft.
- Tip: Use advanced machine learning algorithms to spot high-risk profiles that may indicate synthetic identities or fraudulent behavior.
3. Continuous Monitoring for Suspicious Activity
KYC is an ongoing process. By continuously monitoring customer transactions and behaviors, businesses can detect irregularities like sudden large transactions or account changes, which may signal attempts to commit identity theft. This proactive approach helps businesses to take immediate action, such as freezing accounts or requiring additional verification, before the theft progresses further.
- Tip: Implement real-time fraud detection systems to quickly identify unusual behavior and prevent the misuse of an account.
4. Preventing the Use of Synthetic Identities
Synthetic identity theft is when fraudsters create a new identity using a mixture of real and fictitious data. KYC processes help prevent synthetic identities by scrutinizing the information provided during registration. For instance, discrepancies in names, addresses, or other identifiers can be flagged for further review, ensuring that fraudulent identities aren’t overlooked.
- Tip: Integrate biometric verification like facial recognition or fingerprint scanning to add another layer of protection against synthetic identity fraud.
5. Enhancing the Trust and Security of Transactions
By verifying customers' identities through KYC, businesses can increase the trust factor in online transactions. Consumers are more likely to feel secure knowing that businesses take steps to protect their data. KYC also protects businesses from potential financial losses or reputational damage caused by identity theft, reducing the overall risks associated with fraud.
- Tip: Use two-factor authentication (2FA) alongside KYC to provide more layers of security and ensure that only legitimate users access sensitive services.
By establishing the identity of customers, businesses can enhance security and prevent fraud, but it’s also crucial to implement best practices to manage KYC data securely.
Read: Understanding Customer Screening for AML Compliance
Best Practices for Businesses in Managing KYC Data Securely
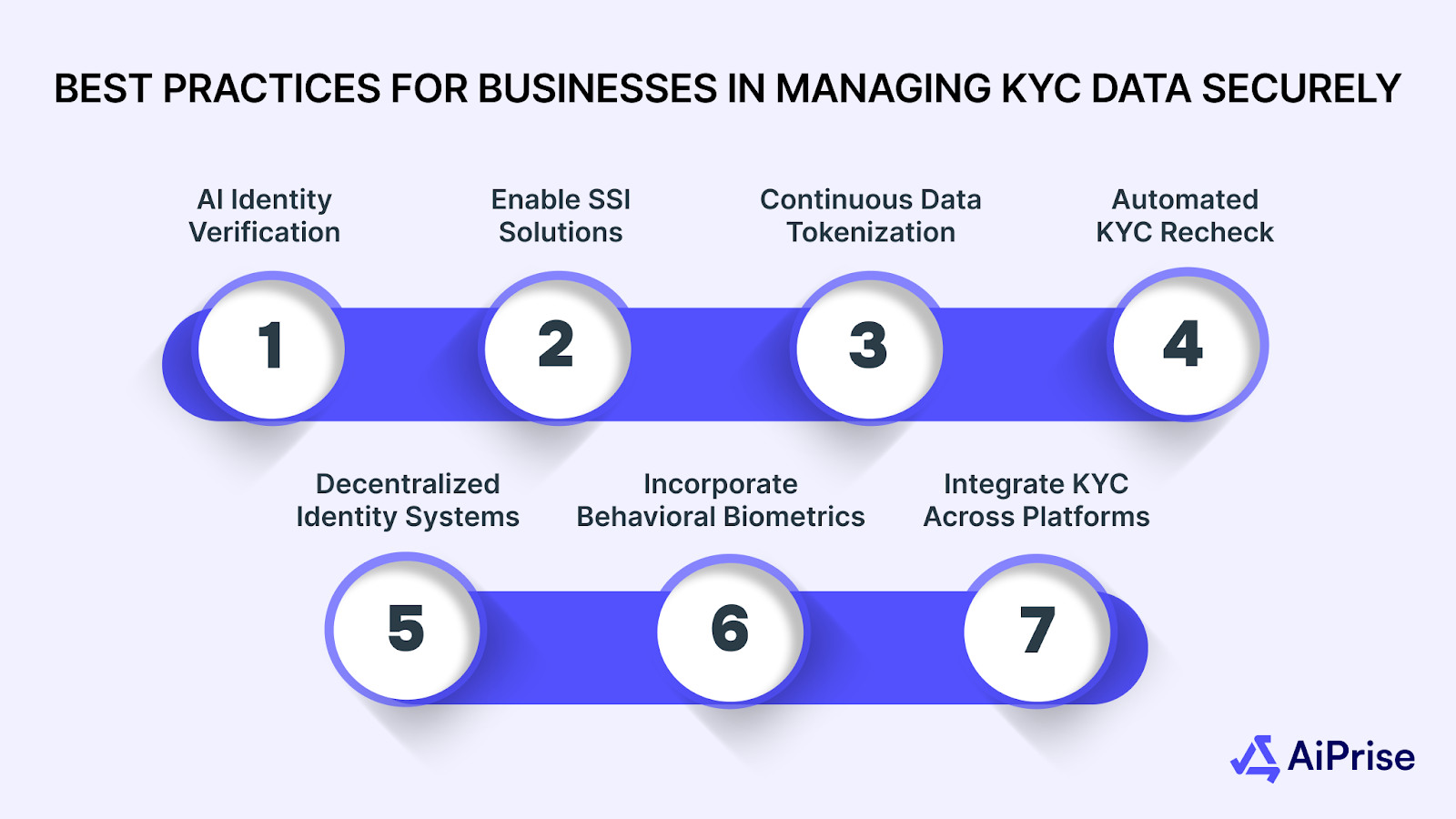
With sensitive personal and financial information being processed and stored, businesses must adopt strong practices to ensure this data remains secure. Below are some of the best practices businesses should implement to protect KYC data effectively:
1. Use AI-Powered Identity Verification Tools
Advanced AI algorithms can assist in identifying suspicious behaviors and verifying customer identities more accurately. AI-driven tools can analyze real-time data, detect anomalies in documents, and even predict potential fraud based on patterns and risk factors.
- Tip: Integrate AI-based document verification and machine learning algorithms that can cross-check the validity of customer screening data using millions of data points.
- Avoid: Relying only on manual methods or outdated verification tools that may miss nuanced fraudulent activities.
2. Enable Self-Sovereign Identity (SSI) Solutions
SSI solutions allow customers to maintain control of their own digital identities, where they store their personal information securely and share only the necessary data with businesses. With blockchain-based SSI, customers can selectively disclose information to a business without the company needing to hold or process that data directly, enhancing privacy and security.
- Tip: Adopt Self-Sovereign Identity platforms to allow users to authenticate using their personal, encrypted credentials, ensuring their data stays within their control.
- Avoid: Relying solely on centralized databases that store and manage vast amounts of sensitive personal information.
3. Use Continuous Data Tokenization for Enhanced Security
Tokenization involves replacing sensitive KYC data with unique tokens that can only be traced back to the original data through a secure and encrypted database. Even if a hacker gains access to the tokenized data, they cannot retrieve the actual sensitive information.
- Tip: Implement tokenization for sensitive data, such as passport numbers or social security numbers, to protect personal information throughout the customer lifecycle.
- Avoid: Storing real customer data without using any form of tokenization or encryption, which increases the risk of data exposure.
4. Automated KYC Re-Verification with Machine Learning
Machine learning algorithms can automate the periodic re-verification of customers’ KYC data to ensure that their information remains accurate and up-to-date. This includes monitoring for changes in financial behavior, address changes, or signs of suspicious activity that might indicate identity theft or fraud.
- Tip: Implement AI-driven re-verification systems that automatically flag outdated or inconsistent data for review and verification.
- Avoid: Only verifying identities during the initial registration and neglecting ongoing updates, which could expose the system to evolving fraud tactics.
5. Use Decentralized Identity Management Systems
Decentralized Identity Management systems leverage blockchain technology to store and verify KYC information without relying on a centralized authority. In such systems, a person can use a digital wallet to manage their identity across different platforms without the need for multiple, centralized databases that can be hacked or compromised.
- Tip: Consider using decentralized identity networks to provide secure, interoperable ways of verifying customer identities across various industries and jurisdictions.
- Avoid: Storing all sensitive data in a centralized system where it’s vulnerable to single-point failures or hacks.
6. Incorporate Behavioral Biometrics
Behavioral biometrics is a method of continuously verifying a user’s identity based on their behavioral traits, such as typing speed, mouse movement, or touchscreen behavior. This is a non-invasive way of tracking identity and preventing fraud in real time.
- Tip: Incorporate behavioral biometrics alongside traditional KYC to continuously monitor and authenticate customers while they interact with digital platforms.
- Avoid: Relying solely on static authentication methods like PINs that can be easily compromised.
7. Integrate KYC with Cross-Platform Identity Management
Many customers use multiple devices and platforms to interact with businesses. By integrating KYC with cross-platform identity management systems, businesses can verify identities consistently across all channels (mobile, web, in-store) and detect any inconsistencies in real-time.
- Tip: Use cross-platform authentication tools that link online and offline identity verification processes to ensure consistency.
- Avoid: Treating each platform or device as an isolated identity verification system, which can lead to gaps in data security.
Incorporating these security practices into your KYC processes is just one part of the broader strategy to mitigate the risks of identity theft. But even with robust KYC protocols, businesses must stay updated with evolving security trends to remain ahead of fraudsters.
Why AiPrise is Your Partner in Identity Protection
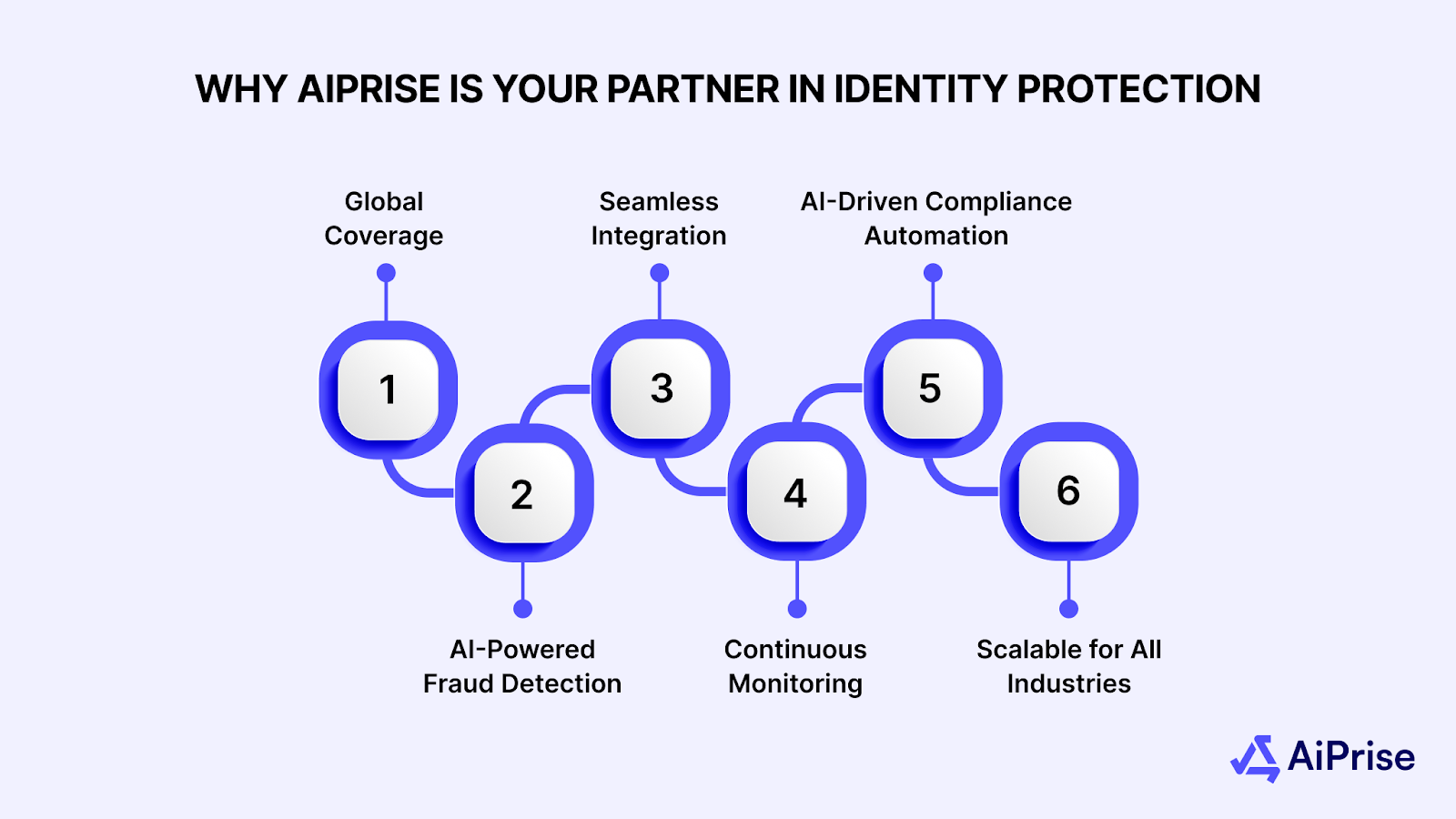
As identity theft becomes increasingly sophisticated, businesses need advanced tools to stay ahead of cybercriminals. AiPrise offers AI-powered KYC solutions that streamline the identity verification process while ensuring the highest level of security. Our technology provides businesses with a comprehensive framework to verify customer identities, detect fraud, and comply with regulatory requirements.
- Global Coverage: Verify customers from 200+ countries with support for various ID types (passports, national IDs, driver’s licenses).
- AI-Powered Fraud Detection: Leverage AI and machine learning to spot fraudulent activity in real-time and protect against identity theft.
- Seamless Integration: Easily integrate KYC solutions into your existing systems with user-friendly SDKs for web and mobile platforms.
- Continuous Monitoring & Reverification: Keep customer data updated with real-time monitoring and periodic reverification to ensure compliance.
- AI-Driven Compliance Automation: Automate routine compliance tasks, including sanctions screening and risk detection, to save time and enhance efficiency.
- Scalable for All Industries: Flexible, scalable KYC solutions tailored to the different needs of businesses across various sectors like fintech, e-commerce, and more.
Protect your business, build customer trust, and stay ahead of fraudsters with AiPrise’s KYC solutions.
Conclusion
Implementing comprehensive KYC procedures is not merely a regulatory need but a strategic imperative to safeguard against the pervasive threat of identity theft. By verifying the identities of all customers, businesses can mitigate risks, enhance trust, and protect both their assets and reputation. As cyber threats continue, adopting advanced KYC solutions is essential for staying ahead of fraudsters.
To fortify your defenses against identity theft, consider partnering with AiPrise. Our AI-powered KYC solutions offer seamless and secure identity verification, ensuring compliance and protecting your business from emerging threats. Book a demo with AiPrise today and take the first step towards enhanced security!
FAQs
1. What is the difference between KYC and AML (Anti-Money Laundering)?
KYC focuses on verifying the identity of customers, while AML involves monitoring financial transactions to detect and prevent illegal activities such as money laundering and fraud.
2. Can KYC help businesses identify politically exposed persons (PEPs)?
Yes, KYC processes often include screening for PEPs—individuals who may present a higher risk due to their political influence—ensuring that businesses remain compliant and mitigate risk.
3. How does KYC help with compliance in different regions?
KYC ensures businesses adhere to local and international regulations, such as the FATF guidelines, and helps them meet the requirements of countries’ data protection and anti-money laundering laws.
4. Can KYC be done without physical presence?
Yes, many businesses now use digital KYC processes, which allow remote identity verification through video conferencing, document scanning, and biometric authentication, removing the need for physical presence.
5. What are the consequences of not complying with KYC regulations?
Non-compliance with KYC regulations can lead to significant fines, legal actions, and reputational damage, making it essential for businesses to maintain up-to-date verification processes.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.










.jpeg)


.jpg)
















.jpeg)









.png)














.png)




















