AiPrise
11 min read
October 14, 2025
How to Build Effective KYB Workflows for Seamless Business Compliance
Key Takeaways










Business-to-business transactions have become increasingly complex in today's interconnected economy. According to the Federal Trade Commission (FTC), fraud losses reached over $12.5 billion in 2024, marking a significant 25% increase year-over-year. Consequently, organizations are now required to implement robust verification systems to ensure both regulatory compliance and self-protection.
This is why Know Your Business (KYB) workflows become essential.
But building effective KYB workflows isn't just about checking boxes for compliance officers. It's about creating seamless processes that verify business legitimacy, identify beneficial owners, and detect potential risks without slowing down legitimate operations.
Whether you're a financial institution onboarding new corporate clients or a payment provider expanding your merchant network, a well-designed KYB workflow can mean the difference between secure growth and costly compliance failures.
Key Takeaways
- KYB is essential for verifying business legitimacy and ensuring compliance with regulatory standards, especially in sectors like finance and fintech.
- Streamlining KYB workflows through automation reduces errors, speeds up verification, and enhances operational efficiency.
- Aiprise offers a comprehensive solution to optimize KYB processes, providing AI-driven verification, global risk screening, and scalable solutions for businesses of all sizes.
- Key components of a KYB workflow include data collection, verification, risk assessment, and ongoing monitoring to maintain compliance over time.
- Regular reviews and automation are crucial for adapting to evolving regulations and ensuring a seamless, secure business onboarding process.
What Are KYB Workflows?
KYB workflows are systematic processes that businesses use to verify the identity, legitimacy, and risk profile of other businesses before establishing relationships. These workflows combine document collection, data verification, screening procedures, and ongoing monitoring to ensure compliance with anti-money laundering (AML) regulations and other legal requirements.
Unlike KYC processes that focus on individual verification, KYB workflows must navigate additional layers of complexity. They need to verify corporate structures, identify ultimate beneficial owners (UBOs), assess business legitimacy, and monitor for changes in ownership or risk status over time.
Suggested read: Comprehensive Guide to AML Compliance in FinTech
The Evolution of Business Verification
Business verification has evolved significantly over the past few decades. In the early days of B2B relationships, companies relied primarily on manual document review and reference checks. This process was time-consuming, inconsistent, and vulnerable to fraudulent documentation.
The introduction of digital business registries in the 1990s and early 2000s marked the first major shift toward more efficient verification. Companies could now cross-reference business claims against official government databases, though this still required significant manual effort.
The 2008 financial crisis accelerated regulatory requirements globally. The United States strengthened its Bank Secrecy Act (BSA) enforcement, while the European Union implemented stricter Anti-Money Laundering Directives. These regulations mandated more thorough due diligence on business clients, particularly regarding beneficial ownership transparency.
Today, artificial intelligence and machine learning technologies are transforming KYB workflows once again. Automated systems can now verify business information in real-time, screen against global watchlists instantly, and continuously monitor ongoing risk indicators.
Why Building Strong KYB Workflows Matters
Strong Know Your Business (KYB) workflows are essential because they serve as your primary defense against major risks like regulatory fines, fraud, and reputational harm. These workflows don't just help you comply with rules; they also create strategic advantages, as mentioned below:

Regulatory Compliance Protection
Regulatory bodies worldwide have intensified their focus on business verification. The Financial Crimes Enforcement Network (FinCEN) in the United States requires financial institutions to identify and verify beneficial owners of legal entity customers. The EU's 5th and 6th Anti-Money Laundering Directives impose similar requirements with substantial penalties for non-compliance.
According to recent data, GDPR violations alone resulted in €1.2 billion in fines during 2024, bringing the total to €5.88 billion since 2018. Inadequate KYB processes expose organizations to similar regulatory risks across multiple jurisdictions.
Fraud Prevention and Risk Mitigation
Effective KYB workflows serve as a critical defense against various forms of business fraud. Shell companies, fraudulent documentation, and concealed beneficial owners are common tactics used by bad actors to infiltrate legitimate business networks.
With fraud losses continuing to rise—including $789 million from government imposter scams alone in 2024—robust verification workflows are no longer optional. They provide the first line of defense in identifying suspicious entities before they can cause harm.
Operational Efficiency
Well-designed KYB workflows strike a balance between thoroughness and efficiency. Manual verification processes can take days or weeks, creating friction in business relationships and potentially leading to the loss of valuable clients to competitors with faster onboarding.
Automated workflows reduce verification time from days to hours or even minutes, improving customer experience while maintaining compliance standards. This efficiency translates directly to competitive advantage in fast-moving industries like fintech and cryptocurrency.
Reputational Protection
Association with fraudulent or sanctioned entities can devastate a company's reputation. News of businesses unknowingly facilitating money laundering or terrorist financing can result in lost customer trust, damaged partnerships, and long-term brand harm. This damage far exceeds any immediate financial penalties.
To achieve these essential benefits, a KYB workflow must be built on a reliable foundation.
Also read: AI-Powered KYB Solutions for Streamlined Business Verification
Core Components of Effective KYB Workflows
The core components of an effective Know Your Business (KYB) workflow are the steps necessary to verify a business entity's identity, ownership structure, and risk profile for compliance and fraud prevention.
The key elements can be categorized into four main phases:
- Business Verification: Confirming the company's legal identity and legitimacy by checking official registration documents and public registries.
- UBO Identification: Tracing the corporate structure to identify and verify the identities of all Ultimate Beneficial Owners (UBOs).
- Risk Screening: Checking the business and its owners against sanctions lists, PEPs (Politically Exposed Persons), and adverse media to assess risk.
- Ongoing Monitoring: Continuously screening the entity to quickly detect any changes in ownership, status, or risk profile.
To operationalize these four phases effectively, organizations should follow a structured approach. Below is the step-by-step process for developing seamless KYB workflows.
Step-by-Step Guide to Build KYB Workflows
Building an effective KYB workflow is a crucial part of Anti-Money Laundering and Counter-Financing of Terrorism (CFT) compliance. It is a structured process to verify the identity, legitimacy, and risk of a corporate customer.
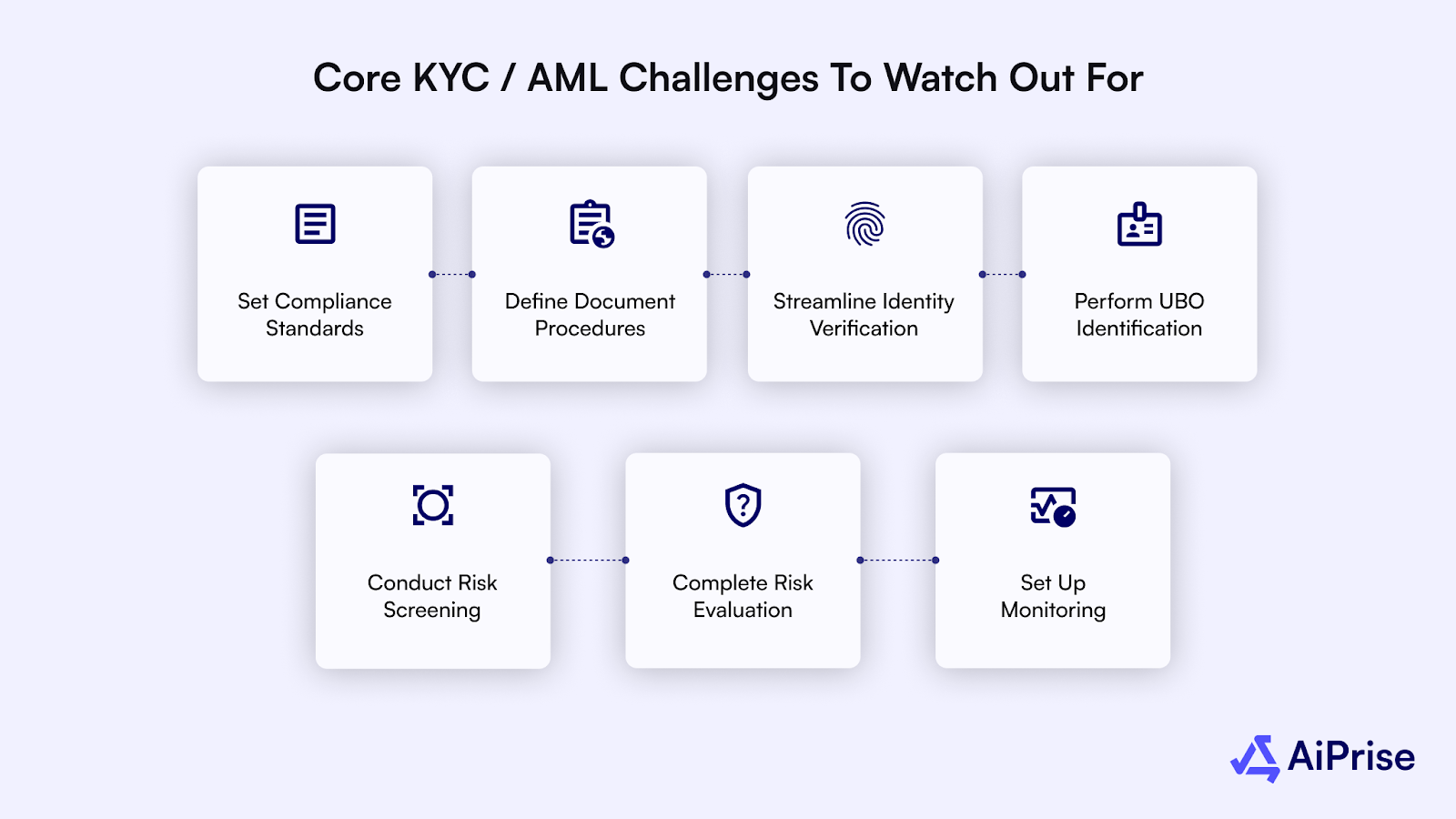
Here is a step-by-step guide to building an effective KYB workflow:
Step 1: Define Your Compliance Requirements
Before designing workflows, thoroughly understand applicable regulations in your operating jurisdictions. Requirements vary significantly between industries and regions.
Key Regulatory Frameworks
- Bank Secrecy Act (BSA) and Customer Due Diligence (CDD) Final Rule in the United States.
- European Union's 5th and 6th Anti-Money Laundering Directives (AMLD5, AMLD6).
- Financial Action Task Force (FATF) recommendations.
- Industry-specific regulations (payment services, cryptocurrency, securities).
Document your compliance obligations clearly.
Step 2: Establish Document Collection Protocols
Standardization is crucial for consistent, defensible verification. Create clear documentation requirements for different business types.
Step 3: Automate Identity and Registration Verification
This step involves using technology to quickly and accurately confirm the business's legal existence and the legitimacy of its documentation.
- Registry Checks: Integrate with official government registries and commercial data sources globally (e.g., U.S. Secretary of State filings, UK Companies House) via API. This allows you to verify details in real-time.
- Document Verification: Implement AI-powered document analysis to automatically check the authenticity of submitted files (e.g., Certificates of Incorporation).
- Cross-Referencing: Ensure the business data provided by the customer aligns with the data found in public registries. Discrepancies are a major red flag and should trigger an automatic manual review (escalation).
Step 4: Execute UBO and Control Person Identification (UBO/CP)
The most critical part of KYB is piercing the corporate veil to find the actual individuals who own or control the company.
- Beneficial Ownership Tracing: Systematically trace the ownership structure through multiple layers of corporate entities (subsidiaries, holding companies) until the ultimate individuals who own a set percentage (e.g., 25% or more) or exert control (e.g., senior management, directors) are identified.
- Source of Data: Use corporate filing documents, shareholder registers, and official regulatory filings for tracing.
- Individual KYC: Once identified, run a full Know Your Customer (KYC) check on every UBO and Control Person, including identity verification (biometrics/liveness checks if remote) and proof of address.
Step 5: Implement Comprehensive Risk Screening
Screening assesses the financial crime risk associated with the business and its associated individuals.
- Sanctions Screening: Screen the business, all UBOs, directors, and senior management against global Sanctions Lists.
- Watchlist and PEP Screening: Check all relevant individuals against Politically Exposed Persons (PEPs) lists and other government or law enforcement watchlists.
- Adverse Media Screening: Use structured data and NLP to search global news and web sources for negative information (adverse media) related to financial crime, fraud, bankruptcy, or regulatory action.
Step 6: Finalize Risk Assessment and Decisioning
This step consolidates all previous checks into a final, auditable business decision.
- Risk Scoring Model: Implement a dynamic scoring model that aggregates risk factors (e.g., high-risk jurisdiction, complex structure, adverse media hits) into a single, tiered risk score (Low, Medium, High).
- Decision Logic: Based on the final risk score and your defined risk appetite:
- Low/Medium Risk: Automatic Approval (or review by a junior analyst).
- High Risk: Mandatory Enhanced Due Diligence (EDD) and escalation to a senior compliance officer for final approval.
- Prohibitive Risk: Immediate Rejection.
- Documentation: Record the final risk score, the reasoning for the decision, and the date.
Step 7: Establish Ongoing Monitoring and Auditing
KYB is a continuous, not one-time, process to maintain compliance and detect emerging risks.
- Event-Based Monitoring: Configure triggers to run a full re-verification when key events occur (e.g., a change in sanctions lists, a company files a significant ownership change with a registry, a key executive is flagged in adverse media).
- Periodic Reviews: Schedule automatic internal alerts to conduct full, periodic re-reviews of client files based on their risk level.
- Audit Trail Maintenance: Ensure your KYB system generates a time-stamped, unalterable log of every action, check, and decision taken.
By building trust with partners and accelerating the onboarding of legitimate businesses, effective KYB systems protect your organization from costly incidents while ensuring both security and operational excellence.
Common Mistakes to Avoid in Building KYB Workflows
While building an effective KYB workflow is critical for compliance, there are several common mistakes that businesses should avoid to ensure the process is efficient and effective:
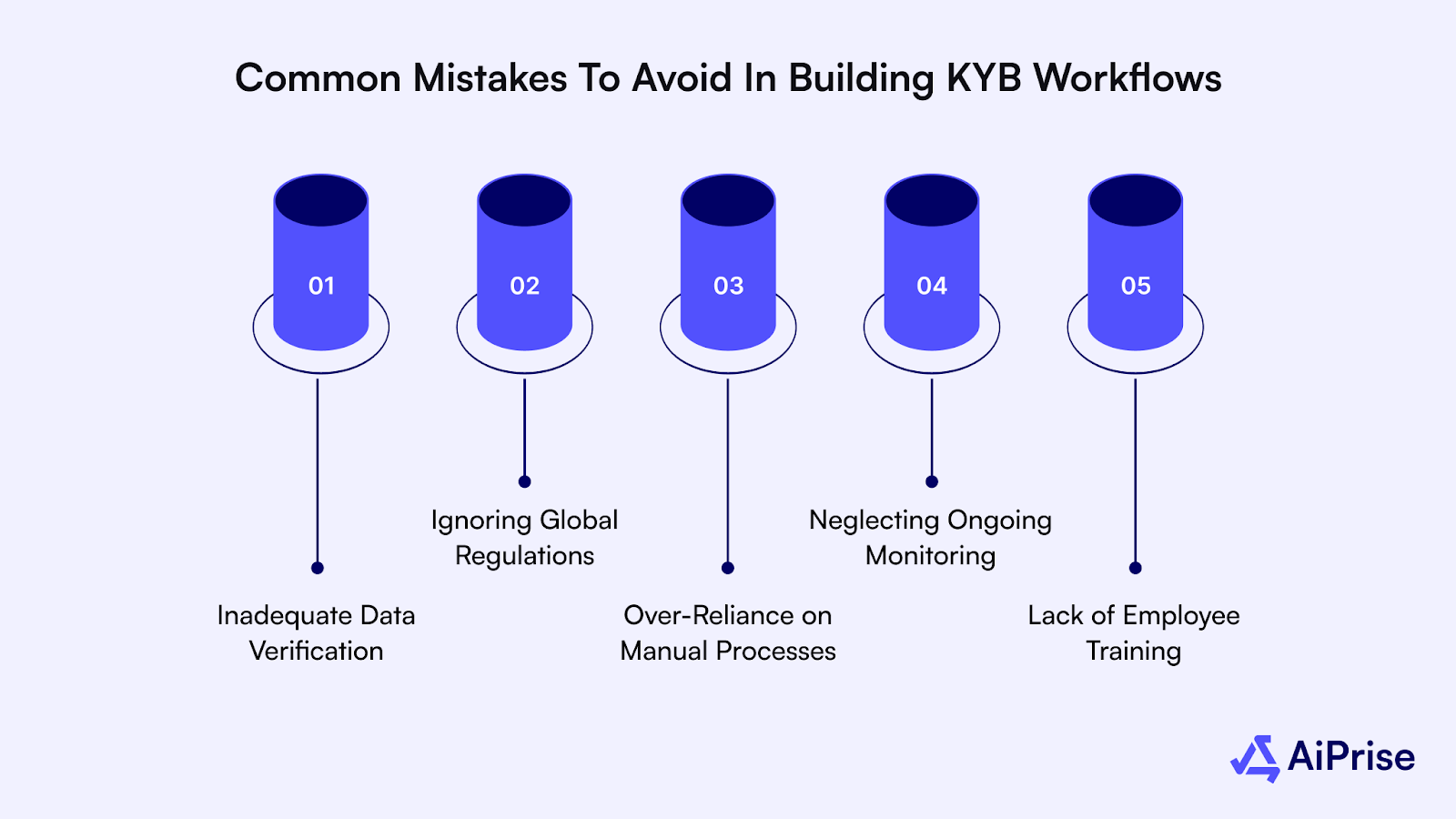
- Inadequate Data Verification: Relying on outdated or inaccurate data can lead to onboarding fraudulent businesses. Always use trusted, up-to-date sources.
- Ignoring Global Regulations: Regulations vary by region. Ensure your workflow complies with local, regional, and global requirements.
- Over-Reliance on Manual Processes: Manual checks are time-consuming and prone to error. Automate wherever possible to improve speed and accuracy.
- Neglecting Ongoing Monitoring: KYB is a continuous process. Regularly update business records and monitor for any changes that could impact compliance.
- Lack of Employee Training: Ensure your team is trained on the latest compliance requirements and workflow tools to avoid overlooking crucial checks.
Turning challenges into opportunities requires smart strategies. The following best practices will guide you in creating seamless KYB workflows.
Best Practices for Building Seamless KYB Workflows
Building an efficient and scalable KYB workflow requires careful planning and implementation. To ensure it is both effective and adaptable, consider the following best practices:
- Use Automation: Automate data collection, verification, and risk assessments to reduce human error and speed up the process.
- Ensure Scalability: Design workflows that can scale as your business grows or enters new markets, accommodating more data and additional compliance checks.
- Maintain Transparency: Ensure all steps are clearly documented and auditable, making it easier to comply with regulatory audits and internal reviews.
- Regular Reviews and Audits: Continuously assess the workflow’s effectiveness and adapt to changing regulations or business needs.
- Integrate Seamlessly: Use tools and systems that integrate smoothly with your existing infrastructure to avoid disruptions and ensure smooth operations.
The common thread across all these best practices is the strategic use of technology for optimization. This is where Aiprise steps in, helping you streamline KYB workflows for maximum efficiency.
Aiprise Helping You Streamline KYB Workflows for Maximum Efficiency
Aiprise is a powerful platform designed to optimize and automate the KYB process, making it easier for businesses to stay compliant and efficiently verify their business partners. Here’s how Aiprise can enhance your KYB workflows:
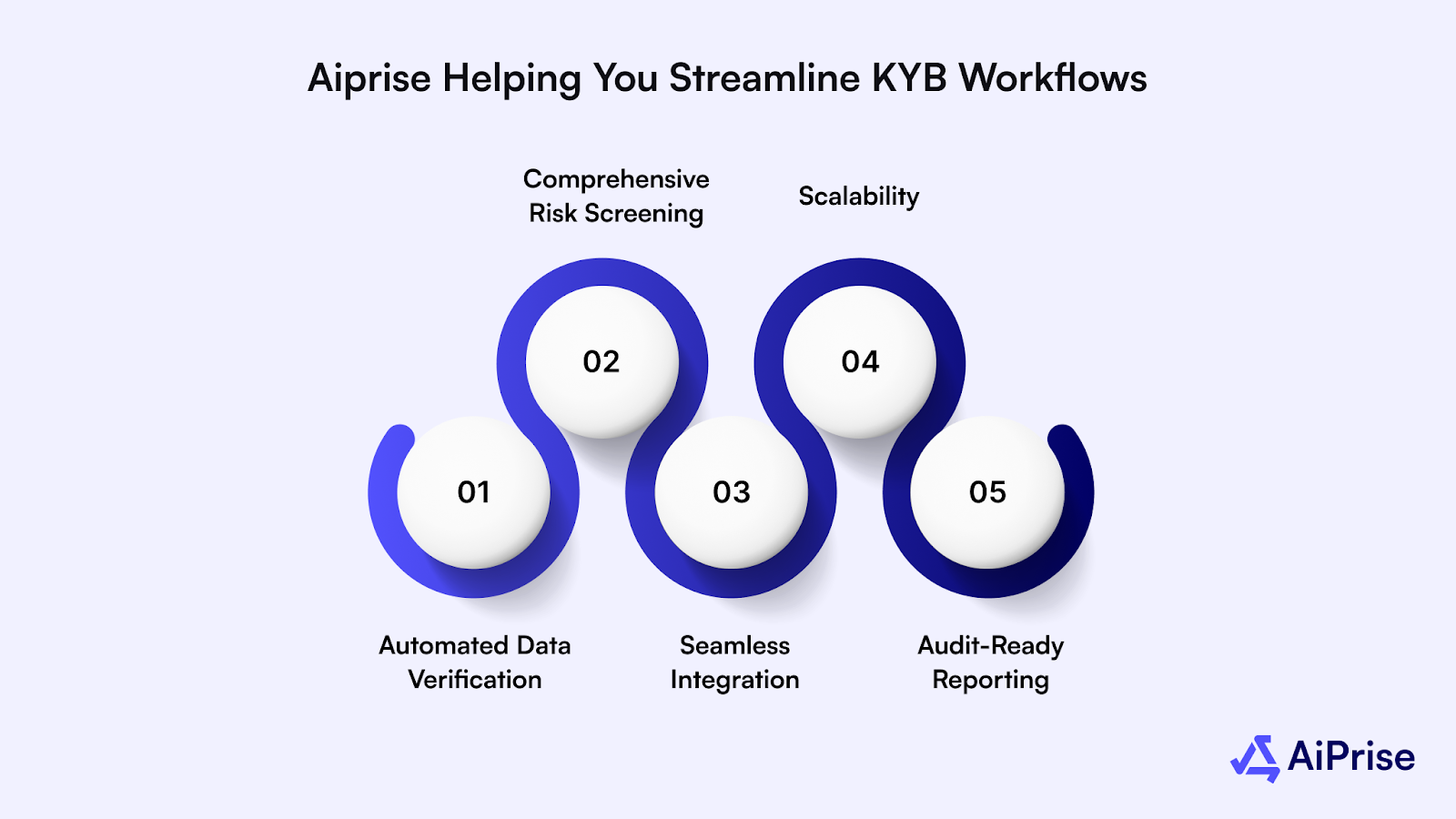
- Automated Data Verification: Aiprise leverages AI-driven technology to automatically verify business credentials, reducing the chances of human error and ensuring fast, accurate results.
- Comprehensive Risk Screening: The platform integrates with global risk databases, including sanctions lists, PEPs, and adverse media, to assess the risk profile of businesses in real-time.
- Seamless Integration: Aiprise can be easily integrated with your existing systems, ensuring a smooth transition and minimal disruption to your workflow.
- Scalability: Whether you're a startup or a large enterprise, Aiprise scales with your business needs, providing tailored solutions that grow with your company.
- Audit-Ready Reporting: Aiprise automatically generates transparent and auditable reports, helping businesses stay prepared for regulatory audits and internal reviews.
Using Aiprise, businesses can automate their KYB processes, enhance compliance, and improve operational efficiency, all while minimizing the risk of fraud or legal issues.
Conclusion
Building an effective KYB workflow is essential for ensuring compliance, reducing risks, and boosting efficiency. Automating the verification process and using advanced tools like Aiprise can help streamline operations, reduce errors, and enhance security, ensuring your business meets regulatory requirements and stays protected against fraud.
As regulations evolve, it’s crucial to adapt your KYB processes to stay ahead. Ready to optimize your workflow?
Book a Demo today and discover how Aiprise can help!
Frequently Asked Questions(FAQs)
1. What is KYB and why is it important?
KYB (Know Your Business) is the process of verifying the identity and legitimacy of a business. It’s essential for preventing fraud, money laundering, and ensuring compliance with regulations.
2. How does Aiprise help with KYB workflows?
Aiprise automates the KYB process, ensuring fast, accurate verification and seamless integration with existing systems, reducing errors and improving efficiency.
3. What are the key components of a KYB workflow?
Key components include data collection, verification, risk assessment, and ongoing monitoring to ensure continued compliance and mitigate risks.
4. How can automation improve my KYB process?
Automation speeds up verification, reduces human error, and ensures compliance checks are completed accurately and on time, improving efficiency.
5. Is Aiprise suitable for businesses of all sizes?
Yes, Aiprise is scalable and customizable, making it suitable for businesses of all sizes, from startups to large enterprises.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.










.jpg)







%20Can%20Improve%20Your%20Compliance%20Strategy.png)