AiPrise
10 min read
December 2, 2025
Secure Digital KYC: How to Store and Share ID Documents Safely

Key Takeaways










Trust snaps fastest when sensitive ID data moves between systems you don't fully control during routine onboarding and reviews. You need airtight storage, partner-safe sharing, selective disclosure, verifiable logs, and strict retention without slowing onboarding or operations. By May 2025, CISA reported the FBI was aware of about 900 Play ransomware victims across organizations in investigations. It shows your document repositories and share-flows are prime ransomware targets, amplifying regulatory exposure and customer-trust fallout. When you align storage and sharing controls to that risk, you protect customers, satisfy auditors, and accelerate onboarding without friction.
Quick Overview
- When onboarding volumes rise, your document exposure increases; implement encrypted storage and access controls to lower risk.
- Adopt tokenized links or reusable credentials so your minimal PII moves between partners, keeping audits straightforward and clear.
- Maintain immutable audit logs and retention policies so your compliance team can prove chain-of-custody during regulator reviews.
- Track onboarding times and reuse rates while your team applies Kyzo KYC: securely store and share identity documents for measurable ROI.
What is Digital KYC?
Digital KYC verifies customers remotely using government IDs, biometrics, and database checks, then binds results to your systems. It covers secure capture, encrypted storage, and partner-safe sharing of identity documents with evidence your auditors trust. Built for regulated teams, the process minimizes collected data, enforces retention, and limits access through role or attribute controls. Done well, it aligns with SOC 2 and ISO 27001 while strengthening AML screening and your fraud defenses.
Once the basics are clear, the next step is defining what turns an ordinary digital KYC process into one that’s actually secure from misuse or leaks.
What Does “Secure Digital KYC” Actually Mean?
Secure digital KYC hardens every capture, transfer, and verification step across your stack against misuse and unauthorized reuse. Controls include client-side encryption, segregated keys, selective disclosure, and one-time shares that expire, watermark, and log evidence. Governance enforces least-privilege access, consented processing, residency boundaries, and immutable audits that satisfy regulators and your internal reviewers. Operational readiness adds rotation playbooks, break-glass controls, partner due diligence, and deletion schedules that reduce your blast radius.
Knowing what security truly looks like sets the foundation, but execution depends on what you collect and how you manage those documents daily. That begins with the kinds of IDs your system accepts and how you validate them safely.
Also read: 3 Essential Components of KYC
IDs Accepted for Secure Digital KYC
This list covers accepted ID types for secure digital KYC using Kyzo KYC: securely store and share identity documents.
Here are the documents you should collect, verify, and store securely using compliant, auditable processes today.
- Government passports with MRZ or chips provide strong assurance when you validate data, capture images, and archive evidence.
- National ID cards, where permitted, require front and back capture so you can confirm legibility and detect tampering consistently.
- Driver’s licenses issued by authorities should be scanned, parsed, and matched to the applicant details your teams already hold.
- Residence permits for immigrants and expats are acceptable when regulations allow, provided you verify validity dates and jurisdiction.
- Tax identification documents should be collected only when necessary, while you mask numbers and apply field-level encryption.
- Recent utility bills or bank statements may confirm addresses if rules permit, and you follow jurisdictional recency woindows.
- Photo IDs should pair with liveness checks during onboarding so you can confirm the applicant matches the document holder.
- Alternate government documents can be accepted when listed by regulators, and you document allowances within updated playbooks.
With the right document types established, the focus shifts to how those files stay protected after capture, because acceptance without secure handling can undo your compliance efforts entirely.

Essential Controls to Secure KYC Data
These controls keep your KYC documents safe, shareable, and audit-ready across regulated, high-risk financial environments today. Here are the must-have steps to secure storage and controlled sharing within your onboarding and partner exchanges.
- Implement KYC: securely store and share identity documents with encryption at rest and in transit for your data. Think ID images and PDFs encrypted end-to-end during uploads, transfers, and storage across your cloud regions.
- Apply least-privilege, role-based access with just-in-time elevation to restrict sensitive KYC document exposure across your teams and vendors. Picture reviewers getting time-boxed access to a single case, while admins use phishing-resistant MFA at every login within your workflow.
- Centralize cryptographic keys using HSMs and automated rotation to prevent misuse and simplify audits across your environments. Keys stay isolated in hardware modules, while services request short-lived tokens for your decryption tasks during processing windows.
- Capture immutable audit logs for every access, share, edit, and admin action on your KYC records across environments. Logs should show viewer identity, purpose, IP, and timestamp, supporting your regulator reviews and incident forensics without gaps.
- Minimize collected PII, tokenize identifiers, and redact unnecessary fields to shrink your breach and misuse risk significantly today. Store birthdates as tokens and mask ID numbers, while your workflows reveal clear values only when required.
- Enforce retention schedules and automated deletion that align with your legal bases, contracts, and operational needs across jurisdictions. Cases older than policy limits get purged or archived, while legal holds pause deletion within your investigations.
- Control partner sharing with policy approvals, expiring encrypted links, and watermarking to maintain your document traceability end-to-end. Vendors receive single-use links tied to cases, while revocation instantly blocks downloads and previews from your dashboard.
- Monitor continuously for anomalies and exfiltration, and test backups and disaster recovery to ensure your continuity during incidents. Alerts flag large downloads or unusual hours, while recovery drills prove restoration of your encrypted archives within targets.
Once your foundational controls are in place, the next challenge is sharing verified KYC data safely with auditors, partners, and vendors, without losing control or visibility.
Also read: Understanding KYC Verification Safety and Prevention Steps
Share KYC Safely: Four Practical Workflows
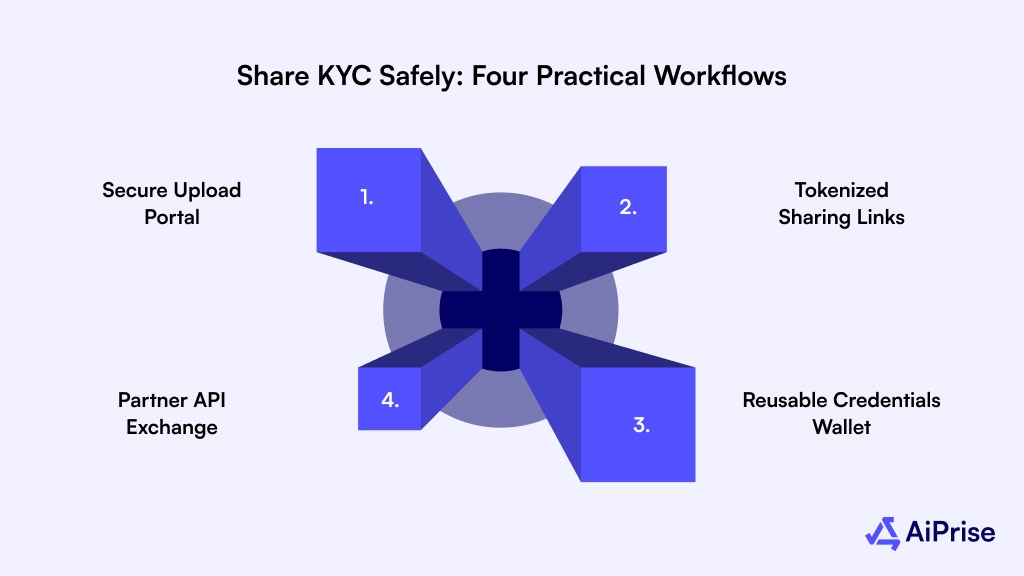
Securely sharing verified identity data demands methods that maintain privacy, meet compliance, and prevent data misuse. Here are four practical workflows aligned with kyzo kyc: securely store share identity documents that achieve these goals.
1. Secure Upload Portal
Use a secure upload portal that encrypts documents in transit and at rest before storage. Require multi-factor authentication and role-based access so only your authorized staff can view sensitive files. Log every access and export action to build regulator-ready evidence and reduce your breach response time.
2. Tokenized Sharing Links
Issue short-lived tokenized links that grant limited access without transferring raw files across insecure channels. Design tokens to expire automatically and to revoke access promptly when suspicious activity triggers alerts. Monitor token usage and record metadata so your audit trail proves who accessed which documents and when.
3. Reusable Credentials Wallet
Offer a user-controlled wallet that stores verified credentials locally or with encrypted keys you manage. Enable selective disclosure so customers share only required attributes, minimizing your data storage and exposure. Integrate liveness checks and periodic revalidation to keep credibility strong and to lower fraud rates.
4. Partner API Exchange
Exchange verification results with partners via signed APIs to avoid sending raw documents over email. Enforce strict contract terms, mutual security testing, and continuous validation so integrations meet your compliance standards. Implement rate limits and anomaly detection to protect shared endpoints and to reduce potential abuse.
Safe sharing only works if the underlying storage supports it. The next section breaks down where and how your organization can store KYC data while staying compliant and audit-ready.
Storage Models for Secure KYC Data
Different storage models define how securely your organization stores and manages sensitive identity documents.
Here’s a simplified view of how each model aligns with kyzo kyc: securely store share identity documents for compliance and operational needs.
Different storage models give you different balances of control, security, and compliance oversight. To make those models work in real operations, teams need a clear checklist of actions that keep systems aligned and auditable.
Also read: Optimizing KYC Verification with Blockchain Technology
KYC Security Implementation Checklist
Protecting verified identities goes beyond encryption; it’s about building trust, audit readiness, and long-term data resilience. Here’s a simple checklist that helps your compliance and security teams align with KYC: securely store and share identity documents according to standards.
- Encrypt every file containing customer IDs, and manage your encryption keys within secure, access-controlled environments.
- Require multi-factor authentication for your staff and partners who access KYC systems, reducing insider and credential risks.
- Replace file-based document sharing with tokenized data exchange or reusable credentials that keep raw data off the network.
- Set clear data retention timelines that match regulatory expectations and automatically delete records once they expire.
- Maintain a detailed audit trail that records every document view, change, and share to support regulator-ready evidence.
- Run periodic penetration tests and system audits to confirm your KYC storage remains resilient against new attack patterns.
- Educate teams on consent management, secure document handling, and how to flag unusual access behavior early.
- Automate real-time alerts for expired IDs, failed verification attempts, or suspicious downloads to stay proactive.
- Minimize what’s stored by keeping only the verified data points required for compliance and risk analysis.
- Evaluate third-party vendors and APIs to ensure their security posture matches your internal KYC and AML controls.
With every control mapped out, it becomes easier to see how purpose-built technology can tie these efforts together, automating verification, storage, and compliance with less manual load on your teams.

How AiPrise Strengthens Secure Digital KYC?
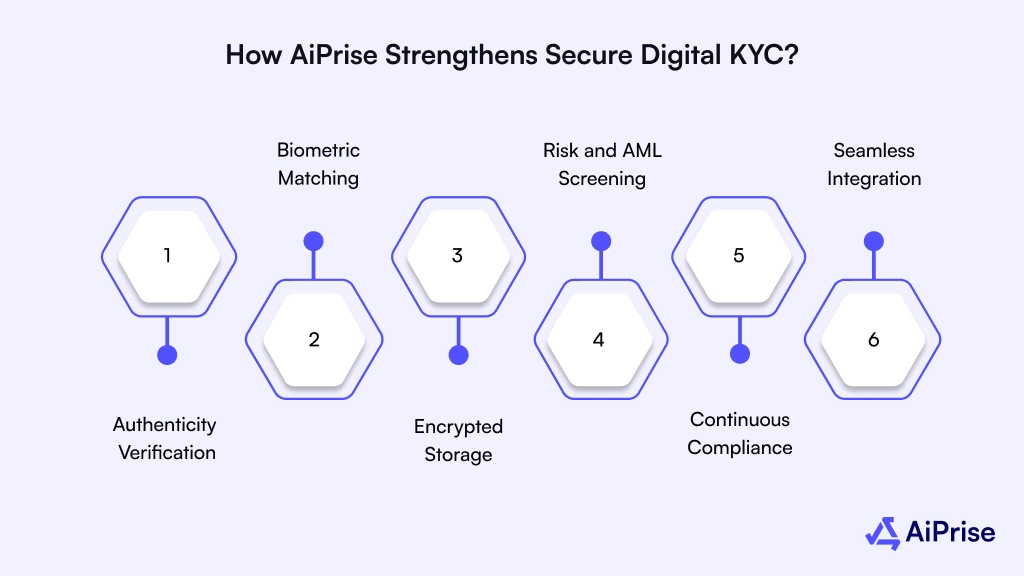
Protecting identity documents demands tools that combine precision, automation, and regulatory awareness.
AiPrise helps your compliance and risk teams secure every stage of KYC, from document verification to ongoing monitoring, without adding operational strain.
- Authenticity Verification: Uses advanced OCR and AI to validate IDs like passports, licenses, and corporate documents for tampering or forgery.
- Biometric Matching: Confirms the right person is submitting the right ID through facial and fingerprint recognition, reducing impersonation and account takeover risks.
- Encrypted Storage: Applies bank-grade encryption and tokenization to protect ID images and PDFs at rest and during transmission.
- Risk and AML Screening: Analyzes over 100 global data sources to flag suspicious identities, ensuring compliant and trustworthy onboarding.
- Continuous Compliance: Monitors document expirations and sanctions lists automatically so your records stay accurate and audit-ready.
- Seamless Integration: Embeds into your existing onboarding or verification systems with SDKs and APIs to automate checks and remove manual errors.
Wrapping Up
Strong KYC security depends on how effectively verified identities are stored, shared, and monitored across your systems. Maintaining encrypted storage, strict access controls, and auditable sharing ensures compliance and protects customer trust. Every improvement in how identity data is handled directly reduces fraud risk, regulatory pressure, and data exposure incidents.
AiPrise gives your organization the tools to meet these standards with speed, accuracy, and global regulatory alignment. Its AI-driven verification and continuous monitoring systems protect sensitive documents through encryption, biometrics, and real-time risk detection. Choosing AiPrise means safeguarding every customer identity while keeping your business compliant, efficient, and audit-ready.
Ready to simplify compliance while safeguarding every identity document? Book A Demo with AiPrise to see secure, compliant digital KYC in action.
FAQ
1. Which ID documents qualify for secure digital KYC?
Passports, driver’s licenses, and national identity cards remain widely accepted, with address proofs used where required. Local regulators may list specific documents, so your policy should mirror those published lists and updates.
2. How long should you retain KYC records?
Most U.S. institutions must retain CIP and related identification records for five years, starting after account closure. Other verification records are also five years, so document your retention timers and automate deletion accordingly.
3. Can you share or rely on a partner’s KYC?
Reliance is allowed under the CIP “reliance provision” if conditions are met, including contracts and AML supervision. Maintain logs, define scopes, and test controls before sharing to keep auditors satisfied.
4. Should you store raw ID images or only extracted fields?
Store only what your policy and laws require, then minimize PII to reduce breach impact and scope. Keep necessary identifiers for retention rules, and tokenize or redact everything else.
5. What security controls are mandatory when storing and sharing KYC?
Encrypt data in transit and at rest, enforce phishing-resistant MFA, and log every access and share. Follow kyzo kyc: securely store share identity documents principles plus NIST guidance for authentication and session protections.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.











.jpeg)


.jpg)















.jpeg)










.png)














.png)




















