AiPrise
11 min read
September 26, 2025
Understanding Digital Identity and How It Works

Key Takeaways










In 2024, the digital landscape experienced a significant 3,205+ data breaches, exposing the personal information of over 1.7 billion individuals, a 312% increase from the previous year. These breaches predominantly targeted sensitive personal data, including emails, phone numbers, and home addresses.
This surge laid bare the vulnerability of our digital identities. As we rely on online platforms for daily activities, the integrity of our digital identities becomes very important.
Understanding how digital identities function and the measures to protect them is essential. This guide delves into what a digital identity is, its components, and actionable strategies to safeguard against cyber threats.
Key Takeaways
- A digital identity is a representation of an individual online, made up of personal information, behaviors, and data associated with your online presence.
- The primary function of a digital identity is to authenticate and verify who you are, granting you access to various services and ensuring security.
- Strong digital identity protection requires the use of secure authentication methods like passwords, biometric data, and two-factor authentication (2FA).
- Continuous monitoring is required to maintain the integrity and security of your digital identity in an ever-evolving online environment.
- Protecting your digital identity goes beyond just passwords; ensuring encryption, managing privacy settings, and being cautious about what you share online are also essential.
What is a Digital Identity?
A digital identity is the representation of an individual or entity in the online world. It encompasses the various pieces of personal information, behaviors, and data associated with a person’s or organization’s online presence. Your digital identity is made up of the data you provide when you interact with online platforms, websites, and services. This can include everything from personal details like your name and address to your online behaviors, such as your shopping habits, preferences, and social media activity.
Simply put, your digital identity is the sum of all the data that uniquely identifies you on the internet. It’s used for a variety of purposes, including authentication, access control, and personalization of services. Just like your physical identity, your digital identity is critical in ensuring that you can engage with the world securely, confidently, and authentically in the digital realm.
The key components of a digital identity can include:
- Personal Identifiers: These are fundamental pieces of information that uniquely identify an individual. They include:
- Full Name: The individual's legal name.
- Date of Birth: Used to verify age and identity.
- Government-Issued Numbers: Such as Social Security numbers or national ID numbers.
- Contact Information: Comprises of email addresses and phone numbers.
- Authentication Credentials: These elements are used to verify identity and grant access to digital services:
- Usernames and Passwords: Basic forms of authentication.
- PINs and Security Questions: Additional layers of security.
- Two-Factor Authentication (2FA): Combines something you know (password) with what you have (a code sent to your phone).
- Biometric Data: Unique physical characteristics that provide a high level of security:
- Fingerprint Scans: Commonly used in smartphones and security systems.
- Facial Recognition: Utilized in various devices and applications.
- Voice Recognition: Employed in virtual assistants and security systems.
- Behavioral Data: Patterns in how individuals interact with digital platforms:
- Keystroke Dynamics: The rhythm and pattern of typing.
- Mouse Movements and Click Patterns: Unique to each user.
- Browsing Habits: Websites visited, time spent, and navigation patterns.
- Digital Footprints: Traces left behind through online activities:
- Social Media Profiles: Information shared on platforms like Facebook, LinkedIn, and Twitter.
- Online Purchases: Transaction histories and preferences.
- Search Histories: Queries made on search engines.
- Device and Location Information: Data related to the devices and locations used to access digital services:
- IP Addresses: Indicate the geographical location of the user.
- Device IDs: Unique identifiers for smartphones, tablets, and computers.
- Geolocation Data: GPS data from mobile devices.
In the digital world, your identity helps you prove who you are, access services, and interact with otherswhether you’re logging into a social media account, making an online purchase, or applying for a loan. Because so much of your personal information is stored online, it's crucial to ensure that it is protected, preventing misuse and fraud.
Now that we have an understanding of digital identity, let's look at how it functions in the digital world and what makes it so essential.
How Does Digital Identity Work?
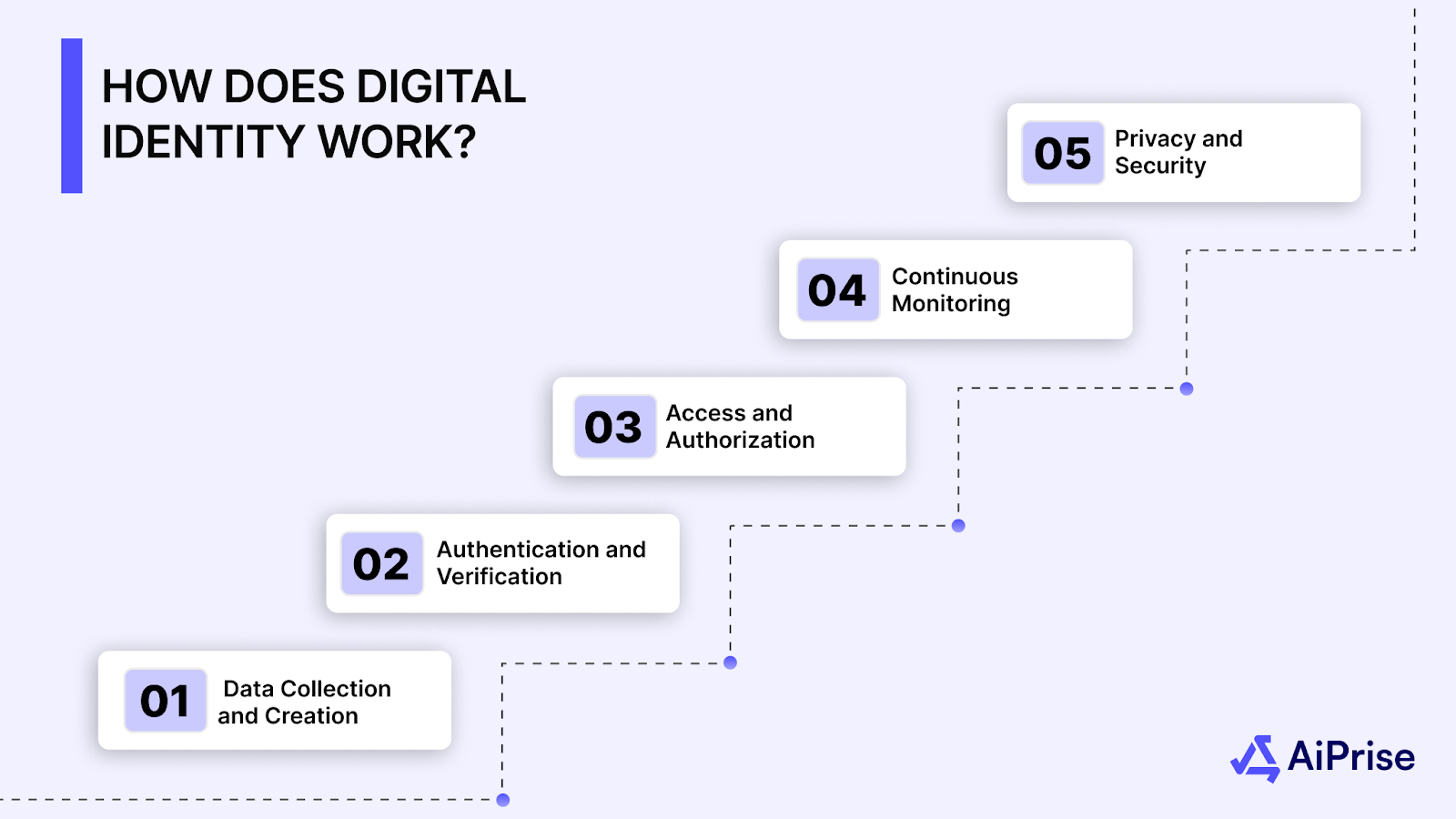
A digital identity functions as a digital passport for individuals, organizations, and devices, enabling secure access to services and facilitating online interactions. It works by verifying who you are and controlling access to the systems and services you need, such as online banking, e-commerce, or social media accounts. Here's a breakdown of how digital identity works:
1. Data Collection and Creation
The foundation of a digital identity begins when an individual or entity provides their personal information, name, address, and contact details when signing up for a service. Over time, this information is supplemented with additional data points such as login credentials, biometric data, and behavioral information. All of these data points form a digital profile that represents your presence in the digital world.
2. Authentication and Verification
To access online platforms and services, your digital identity must be authenticated. The verification check process involves confirming that you are who you claim to be. Typically, this involves:
- Usernames and passwords are used to initiate the authentication.
- Biometric recognition, like facial or fingerprint scans, is used for higher security.
- Two-factor authentication (2FA) adds more layers of protection by requiring something the user has (like a mobile device or token) along with something they know (like a password).
This process ensures that only the legitimate owner of the identity can access the associated services and information.
3. Access and Authorization
Once authenticated, your digital identity grants you access to various digital services and platforms. However, the level of access you’re granted depends on the authorization tied to your identity. For example, a user might have permission to view their personal account but may need additional authorization to access more sensitive data, such as financial records or personal files. The scope of access is controlled through:
- User roles and permissions: These define what data or features a person can access based on their identity.
- Access tokens: Unique identifiers that allow users to interact with certain parts of a platform or service.
4. Continuous Monitoring and Updates
A digital identity is not static. It evolves as you interact with digital platforms, make purchases, or engage in online activities. Ongoing monitoring helps ensure that your identity remains secure and accurate. Any changes to your information, such as updating contact details, changing passwords, or adding new devices, need to be verified to maintain the integrity of your digital identity.
Additionally, many services monitor suspicious activity tied to your identity, flagging potentially fraudulent actions and ensuring that your identity isn’t misused.
5. Privacy and Security
With the wealth of personal information tied to a digital identity, strong data protection and privacy management are critical components. Personal data needs to be:
- Encrypted during transmission to prevent unauthorized access.
- Stored securely to protect against data breaches.
- Compliant with privacy regulations like GDPR, ensuring users’ personal information is used responsibly and with consent.
Ensuring the safety of digital identity is essential for maintaining trust and preventing identity theft, fraud, and data misuse.
Services that store your identity data must ensure that it is encrypted, stored securely, and only shared with your consent. This protection ensures that your personal data isn’t misused or exploited.
With this understanding of how digital identities operate, it's crucial to explore the steps you can take to safeguard your identity and prevent misuse.
How to Protect Your Digital Identity
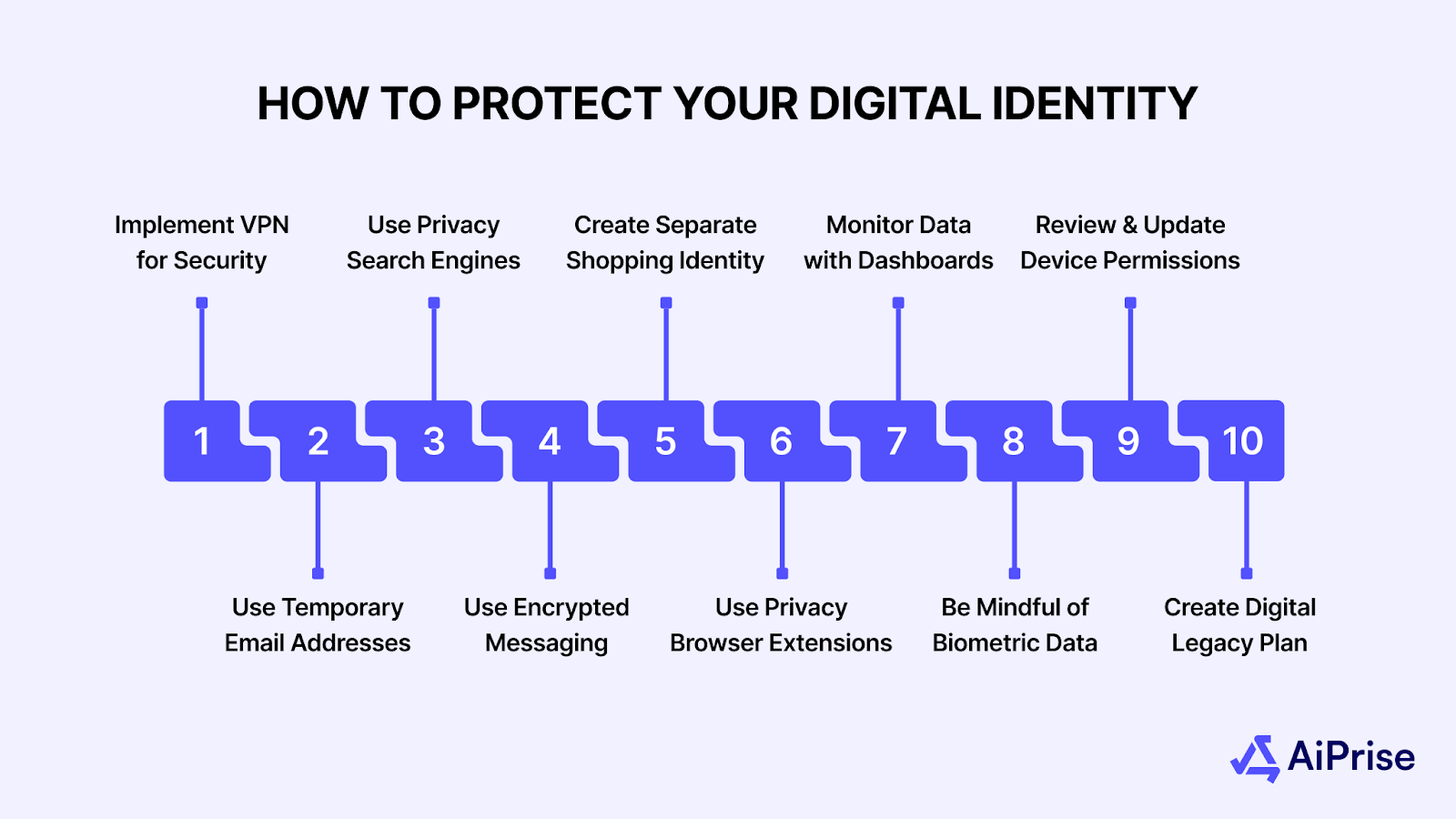
Your digital identity extends across everything you do online, from signing into email and social accounts to completing financial transactions. With growing risks of fraud, misuse, and data breaches, taking steps to secure your information has become an essential part of modern life. Below are ten measures that can help you safeguard your online presence.
1. Secure Your Connection with a VPN
A Virtual Private Network (VPN) creates an encrypted pathway between your device and the internet, making it far more difficult for outsiders to intercept your activity. While many associate VPNs with public Wi-Fi in airports or cafés, they are equally valuable at home. Internet providers and other entities can track browsing patterns if traffic is unprotected. Keeping a VPN active ensures that sensitive activities such as banking or shopping remain private.
2. Use Disposable Emails for Low-Risk Registrations
Providing your primary email address for every online sign-up increases your exposure to spam and phishing attempts. A safer approach is to use disposable or alias addresses for non-essential accounts, keeping your main inbox reserved for critical communication.
- Create one alias for shopping and another for newsletters so you can trace where unwanted emails are coming from.
- Use temporary addresses that expire after a set time to reduce long-term exposure.
- Keep your personal inbox strictly for banking, healthcare, or official correspondence.
3. Choose Privacy-Focused Search Engines
Mainstream search engines often track and profile user behavior. Privacy-oriented alternatives offer similar functionality without extensive data collection. Making one of these your default search engine is a straightforward way to limit the amount of personal information being stored and shared.
4. Use Encrypted Messaging Applications
Standard SMS and some messaging platforms lack end-to-end encryption, leaving conversations vulnerable to interception. Choosing applications that provide strong encryption ensures that only the sender and recipient can view the content. For sensitive personal or professional communication, encrypted messaging is the more secure option.
5. Maintain a Separate Identity for Online Purchases
Using the same email and payment details across all online platforms increases the risk of exposure if a breach occurs. Establishing a separate digital identity for shopping, including a distinct email address and virtual or wallet-based payment methods, helps reduce this risk and prevents any potential compromise.
6. Strengthen Browsers with Privacy Extensions
Websites track user activity across multiple pages and platforms, often without consent. Browser extensions that block trackers, enforce HTTPS, and filter ads give you more control over what data is being collected.
- Install trusted extensions that block cookies and third-party trackers.
- Enable HTTPS-only mode to avoid insecure connections.
- Review your extension list regularly to remove outdated or unnecessary add-ons.
7. Review and Manage Shared Data
Large platforms often collect more information than users realize, including location history and browsing behavior. Privacy dashboards allow you to monitor, manage, and delete stored data. Conducting regular audits ensures that unnecessary or sensitive information is not left exposed.
8. Use Biometric Data Selectively
Biometric authentication provides convenience, but it comes with limitations. Unlike passwords, fingerprints or facial scans cannot be changed once compromised. It is advisable to reserve biometric logins for high-security accounts and pair them with multi-factor authentication. For routine access, strong and unique passwords remain the safer option.
9. Audit Application Permissions
Applications frequently request permissions beyond what is necessary for their function. Reviewing and restricting access to features such as location, microphone, or camera reduces unnecessary exposure. Permissions should be granted only where essential, and revoked when no longer required.
10. Plan for Digital Legacy Management
Few people consider what happens to their online accounts after they are no longer able to manage them. Setting up a digital will or using tools like AiPrise ensures that accounts, data, and subscriptions are handled appropriately. This not only protects your privacy but also reduces challenges for family members.
Securing your digital identity requires consistent attention rather than one-time measures. Each of these practices adds a layer of protection, making it more difficult for malicious actors to exploit your information. By combining them, you create a stronger defense against fraud, data theft, and misuse.
Protect Your Digital Identity Today with AiPrise
Today, safeguarding your digital identity is essential. At AiPrise, we offer advanced solutions that help you monitor, protect, and manage your digital presence. Whether you're concerned about data breaches, fraud, or just want to maintain a secure online footprint, AiPrise provides the tools and expertise you need to stay one step ahead
- Global Coverage: Verify users from over 200 countries using various ID types, including passports, national IDs, and driver's licenses.
- One-Click KYC: Enable instant user verification with just an ID number and a selfie, streamlining the onboarding process.
- AI-Powered Document Verification: Utilize machine learning to detect forged or altered documents, enhancing security.
- Liveness Detection: Implement biometric verification with facial recognition to confirm the user's presence during the verification process.
- Automated KYC/KYB Workflows: Streamline Know Your Customer (KYC) and Know Your Business (KYB) processes with automated workflows, reducing manual intervention.
- Watchlist Screening: Regularly screen users against global sanctions and Politically Exposed Persons (PEP) lists to ensure compliance.
- Flexible API and SDK: Integrate AiPrise's solutions seamlessly into your existing systems with developer-friendly APIs and SDKs.
- Customizable Onboarding Flows: Design tailored verification processes to meet specific business needs and risk profiles.
- Comprehensive Risk Assessment: Evaluate multiple data points, including email, phone, device, and credit history, to assess user risk.
- Ongoing Monitoring: Conduct automated checks at regular intervals to provide continuous protection and minimize potential losses.
By leveraging these features, AiPrise empowers businesses to protect digital identities effectively, ensuring secure and compliant operations across various industries.
Conclusion
Your digital identity is the connection between you and your online life, and protecting it is essential to ensuring your privacy, security, and personal safety in the digital realm. As digital identity threats become more sophisticated, proactive measures like continuous monitoring and encryption are essential in staying ahead of cybercriminals.
To safeguard your business and customers’ digital identities, partner with AiPrise. Our AI-powered KYC, KYB, and AML solutions provide comprehensive identity verification and fraud prevention tools to help businesses stay compliant and protected. Book A Demo with AiPrise today and take the first step toward strengthening your security and protecting your digital assets.
FAQs
1. Can my digital identity be stolen?
Yes, your digital identity can be stolen if sensitive data such as passwords, personal details, or biometric data is accessed by unauthorized individuals or hackers.
2. How do I know if my digital identity has been compromised?
Signs of a compromised digital identity include unusual activity on your accounts, receiving notifications of login attempts from unfamiliar locations, or a sudden change in your personal details on platforms you use.
3. Is a digital identity the same as an online profile?
While an online profile is part of your digital identity, your digital identity is more comprehensive, encompassing personal identifiers, authentication methods, behavioral data, and more.
4. How does digital identity affect privacy?
Your digital identity includes data that can reveal a lot about you, and if not properly managed, it can lead to privacy breaches or unauthorized access to personal information.
5. How can businesses safeguard the digital identities of their customers?
Businesses can safeguard digital identities by implementing strong security measures like data encryption and using reliable identity verification solutions.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.

















.png)


