AiPrise
8 min read
September 23, 2025
Understanding Identity Proofing and Verification Processes

Key Takeaways










Fraudsters are getting smarter, and your business is on the front lines of defense. Identity theft and fraud can happen in an instant, and the consequences are costly. In fact, the FTC reported more than 1.1 million identity theft cases in 2024 alone, resulting in $12.7 billion in losses.
As a financial institution or payment provider, the risk of fraud is something you can’t afford to ignore. Each fraudulent transaction is not just a loss in dollars but a hit to your reputation and trust with customers. You need solutions that can not only detect fraud but also prevent it before it happens.
In this blog, we’ll explore the crucial difference between identity proofing vs identity verification, how they work together to keep your business secure, and the technologies that can help protect your users and meet compliance standards.
Key Takeaways:
- Identity proofing verifies a person's identity at the start, while identity verification ensures ongoing access security.
- Both processes are essential for preventing fraud, securing sensitive data, and maintaining compliance with regulations like KYC and AML.
- Emerging technologies, including AI, biometrics, and blockchain, are shaping the future of identity verification.
- AiPrise offers advanced tools for efficient identity verification, including government verifications and real-time case management.
- Businesses need both identity proofing and verification to reduce fraud risks and build customer trust.
What Is Identity Proofing and Why Is It Important?
Identity proofing is a critical process where businesses verify that a person is who they claim to be before granting access to services or making transactions. This process involves collecting personal data, validating documents, and sometimes using biometrics to ensure the individual is legitimate.
To understand how identity proofing works, here are the key elements involved:
Key Elements of Identity Proofing
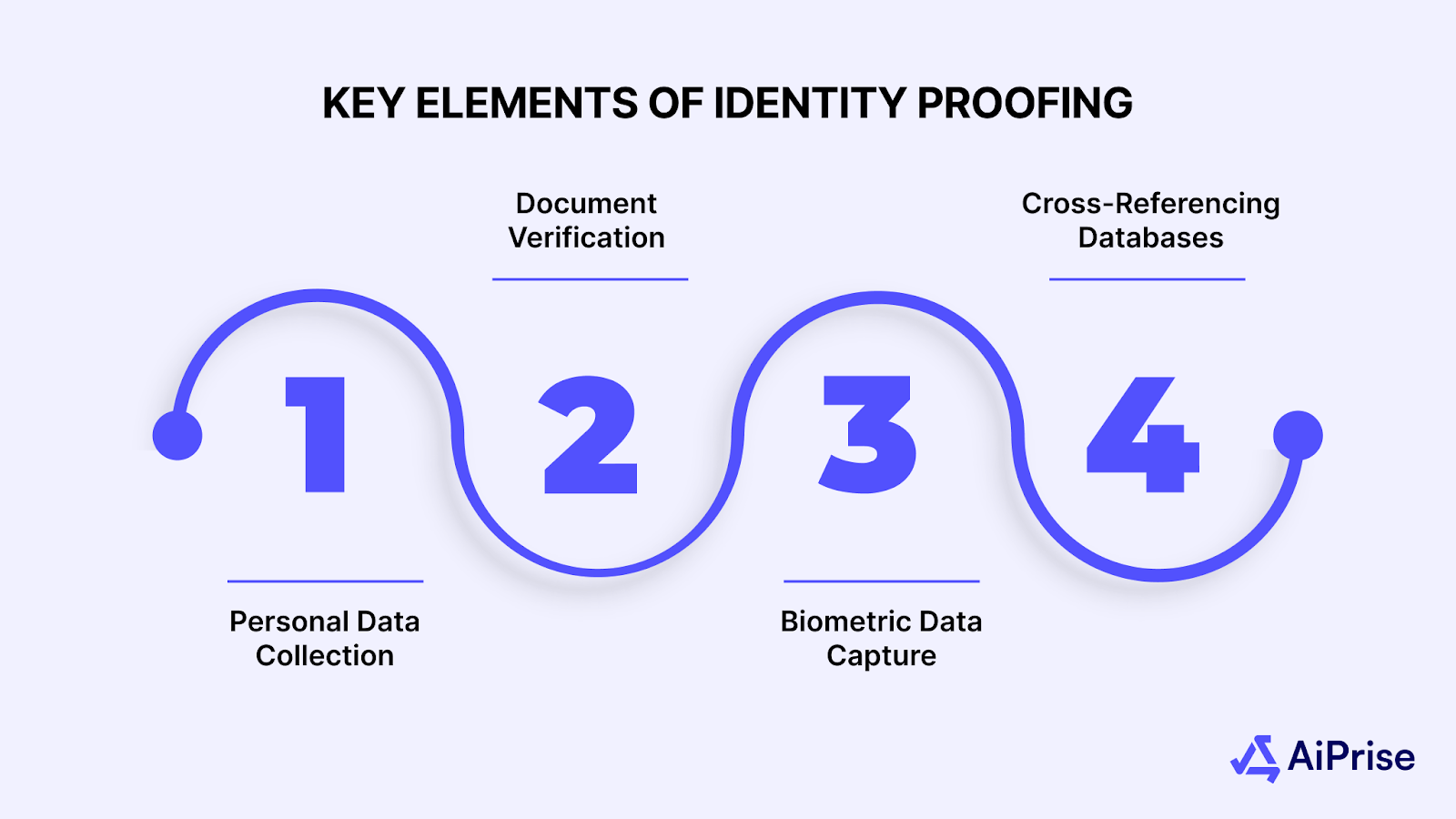
- Personal Data Collection: Gathering details such as full name, date of birth, address, and other identifiers.
- Document Verification: Reviewing official documents such as a passport, driver’s license, or social security number to confirm someone's identity.
- Biometric Data Capture: Using technologies like facial recognition or fingerprints for real-time identity verification.
- Cross-Referencing Databases: Verifying the data against trusted sources such as government databases or credit bureaus to confirm authenticity.
Importance of Identity Proofing
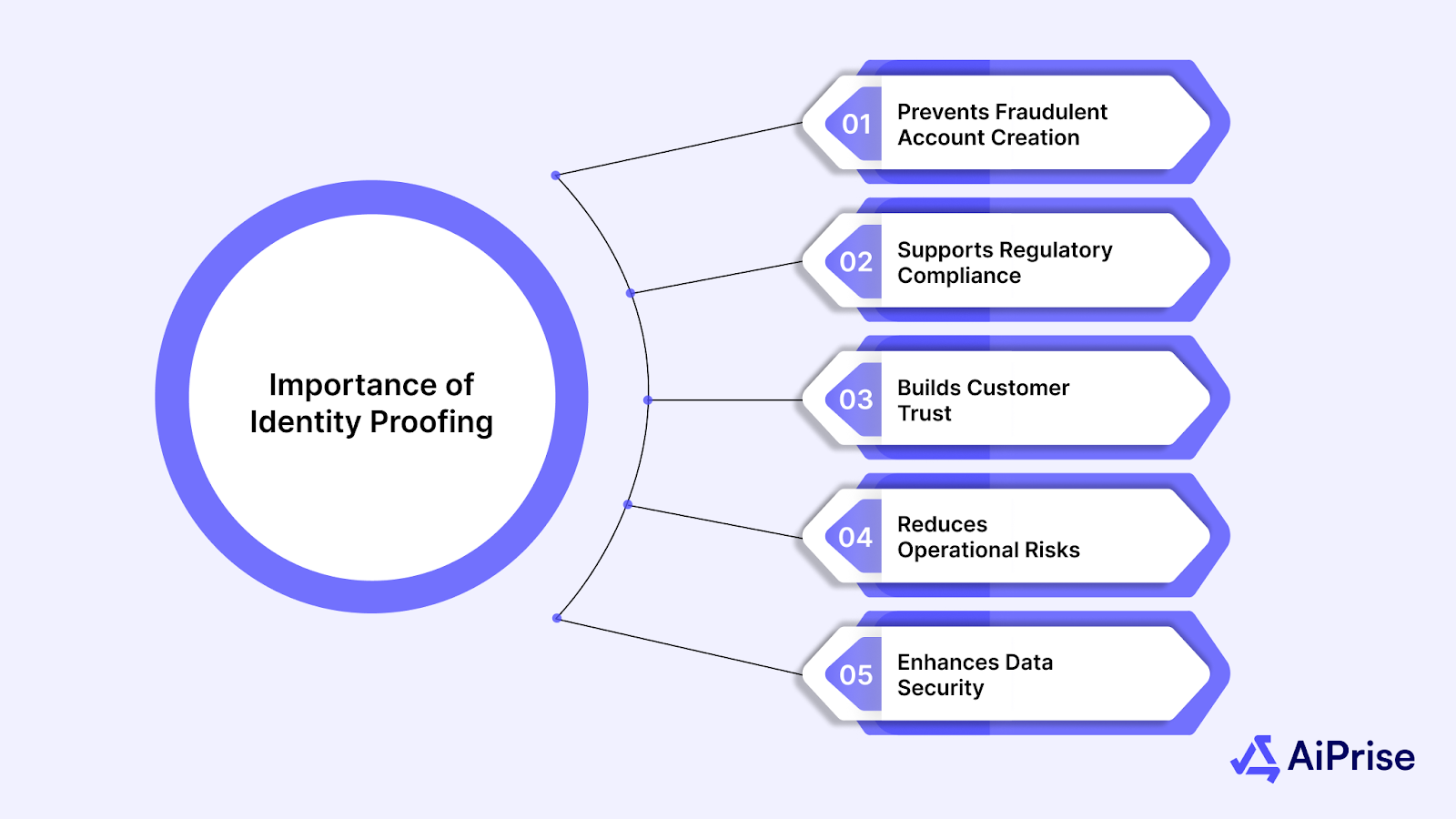
Identity proofing plays a critical role in protecting both your business and customers from fraud. When you verify the identity of a user before granting access, you reduce the chances of malicious actors infiltrating your system.
Here are key reasons why identity proofing is so important:
- Prevents Fraudulent Account Creation: Stops criminals from using stolen or fake identities to access services.
- Supports Regulatory Compliance: Helps businesses comply with KYC (Know Your Customer) and AML (Anti-Money Laundering) regulations, reducing the risk of penalties.
- Builds Customer Trust: Customers are more likely to feel confident in your platform when they know their identity is being verified securely.
- Reduces Operational Risks: Reduces the chances of unauthorized access, helping safeguard your business from data breaches and financial fraud.
- Enhances Data Security: Ensures that sensitive user data is kept safe by confirming the identity of those accessing the system.
Now that you understand how identity proofing establishes user legitimacy, it is equally important to explore how ongoing verification protects access.
Also Read: Understanding What Identity Proofing Is and Why It Matters
What Is Identity Verification and How Does It Work?
Identity verification is the process of confirming that the person claiming an identity is, in fact, the individual they say they are. This step takes place after proofing and helps safeguard against unauthorized access and fraudulent activities.
To understand how identity verification functions, here are the key identity verification methods used:
Key Methods of Identity Verification
- Multi-Factor Authentication (MFA): A process where users confirm their identity by completing several steps, like entering a password and a code sent to their phone.
- Biometric Verification: Involves using facial recognition, fingerprints, or iris scanning to verify identity.
- Behavioral Biometrics: This method analyzes patterns in a person's behavior, like how fast they type or how they move the mouse, to confirm their identity.
- Device and Geolocation Tracking: Verifying the device or location from which the user is accessing services to detect anomalies.
Why Identity Verification Matters?
Identity verification is important to ensure that only the rightful person can access sensitive accounts and services. By verifying users each time they log in or initiate transactions, you reduce the risk of fraud and account takeover. This process also provides an added layer of security and builds customer confidence in your platform.
Here are the main reasons why identity verification is critical:
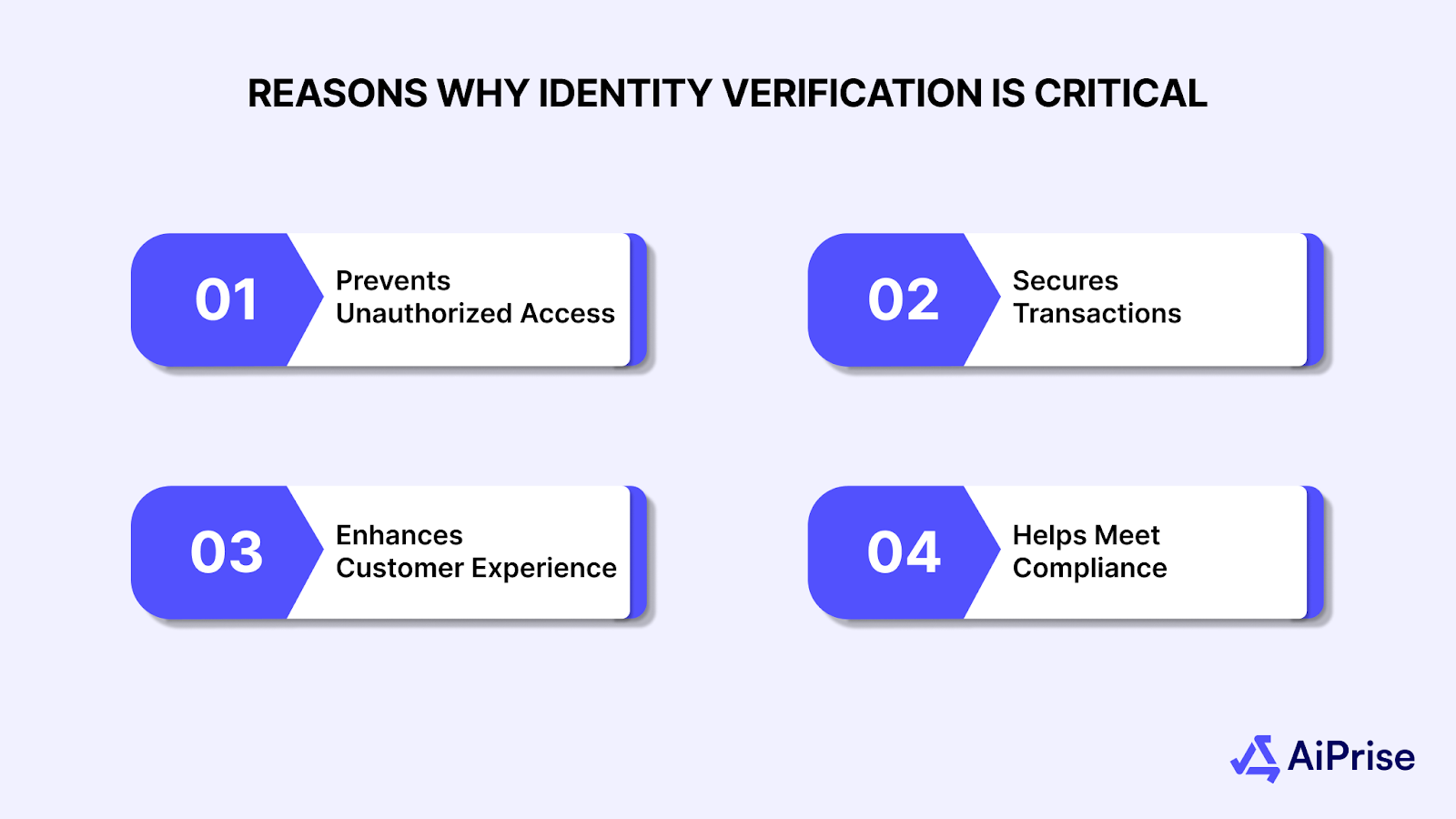
- Prevents Unauthorized Access: Makes sure that only the rightful user can log into their account and complete transactions.
- Secures Transactions: Protects both users and businesses from financial fraud by verifying identity during high-risk actions.
- Enhances Customer Experience: Verification methods, such as biometric authentication, make it easy for users to securely access their accounts.
- Helps Meet Compliance: Verifying identity during interactions is essential for meeting KYC and AML compliance regulations.
To clarify when and why each process is applied, it helps to compare identity proofing vs identity verification side by side.
Also Read: Understanding Identity Verification (IDV) and its Significance
Key Differences Between Identity Proofing vs Identity Verification
While both identity proofing and identity verification are essential for fraud prevention, they serve distinct purposes in the customer journey. Identity proofing ensures that a user’s identity is established and legitimate from the start. In contrast, identity verification works continuously, confirming that the person accessing an account or making a transaction is the same individual over time.
To better understand the differences, here’s a comparison of identity proofing vs identity verification:
Identifying the unique functions of each process prepares businesses to adopt the latest tools that improve identity management.
Also Read: How Identity Verification Enhances KYC Compliance
Trends and Innovations in Identity Management
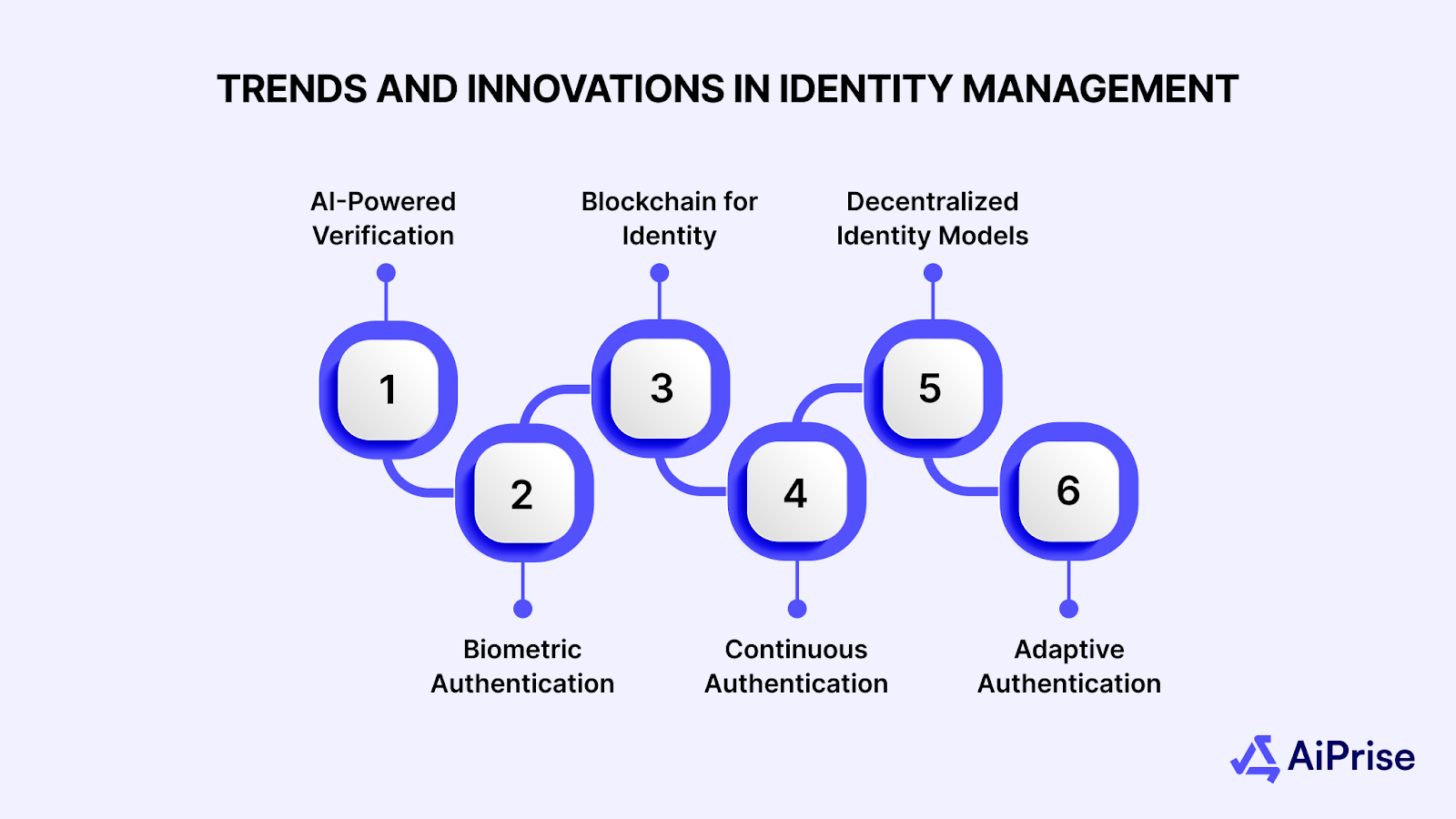
Identity management is rapidly changing as technology advances, providing new ways to protect sensitive data and enhance security. These trends aim to increase both accuracy and convenience, helping businesses and users stay ahead of potential fraud.
Here are some of the latest trends and developments shaping the identity management space:
- AI-Powered Verification: Artificial intelligence is now being used to analyze patterns and detect fraudulent behavior, providing better insights into user authenticity.
- Biometric Authentication: Advancements in facial recognition, voice recognition, and fingerprint scanning are making user verification faster and more secure.
- Blockchain for Identity: Blockchain technology is increasingly being explored for creating tamper-proof digital identities that are more secure and easier to manage.
- Continuous Authentication: This approach verifies identity in real-time throughout the user’s session, monitoring factors like behavior and device location to ensure ongoing security.
- Decentralized Identity Models: Decentralized solutions provide individuals with more control over their data, while enabling businesses to securely verify identities without relying on centralized authorities.
- Adaptive Authentication: This method adjusts security measures based on the level of risk, applying stronger verification processes for higher-risk transactions or situations.
Among the available solutions, AiPrise demonstrates how advanced tools can integrate these trends into practical identity verification workflows.
Also Read: How Compliance Technology Drives Efficiency and Trends
AiPrise: Advanced Solutions for Secure Identity Verification
AiPrise offers a suite of advanced solutions designed to enhance identity verification and fraud prevention processes. With a focus on compliance and security, AiPrise integrates modern technology to provide seamless identity management. Its tools are designed to streamline processes while maintaining high levels of user verification and fraud detection.
Here are the key features of AiPrise that help businesses secure their operations:
- Onboarding SDK: A developer-friendly SDK enables businesses to integrate KYC/KYB processes directly into their applications for streamlined onboarding.
- Government Verifications: AiPrise connects with global databases to authenticate user identities, improving verification accuracy and reducing fraud risks.
- One Click KYC: With just a selfie and ID number, users can complete the identity verification process quickly and securely.
- Reverification: AiPrise supports periodic reverification of user identities, especially during high-risk activities or when changes are detected.
- Document Insights: The platform uses AI to extract and interpret data from documents, helping compliance teams review them efficiently.
- Case Management: The platform offers a centralized dashboard, allowing businesses to track and manage verification cases in real-time.
- Watchlist Screening: AiPrise screens users against global watchlists, including OFAC and SDN lists, to detect potential risks.
- Workflows: AiPrise enables businesses to create customized workflows by selecting the appropriate verification methods and risk checks tailored to user profiles.
AiPrise's advanced solutions provide businesses with comprehensive identity verification capabilities that enhance security, ensure compliance, and improve user experience.
Conclusion
Identity proofing and verification are essential for protecting your business from fraud while ensuring regulatory compliance. By implementing both processes, you can safeguard your customers' sensitive data and provide a secure, trustworthy experience. The combination of proven methods and modern technology can significantly enhance your fraud prevention efforts and help you meet the required standards.
As fraud risks continue to rise, businesses must stay ahead by adopting advanced identity management solutions. AiPrise offers the tools and technology to ensure your business is protected with efficient, accurate identity verification.
If you're ready to improve your identity verification processes and secure your platform, Book A Demo today to learn more about our solutions.
FAQs
1. What Is The Difference Between Identity Proofing And Identity Verification?
Identity proofing establishes a person’s identity through personal data, documents, and biometrics at the start of a relationship. Identity verification, however, confirms that the person accessing services or completing transactions is the legitimate individual, ensuring ongoing security.
2. How Does Biometric Authentication Enhance Security?
Biometric authentication uses unique physical traits like fingerprints or facial recognition to verify a user’s identity, providing a more secure method of validation than traditional passwords, which can be easily compromised.
3. Why Is Identity Proofing Essential For Regulatory Compliance?
Identity proofing helps businesses comply with KYC (Know Your Customer) and AML (Anti-Money Laundering) regulations by ensuring that only legitimate users can open accounts or access services, reducing the risk of fines and penalties.
4. How Can AiPrise Help My Business With Identity Verification?
AiPrise offers a suite of tools that simplify the identity verification process, including government verifications, watchlist screening, and biometric authentication, all designed to ensure secure user access while meeting regulatory standards.
5. What Are The Main Benefits Of Continuous Authentication?
Continuous authentication provides ongoing identity validation throughout a session, detecting and preventing unauthorized access in real time by analyzing behavior and device information. This helps maintain high security without disrupting the user experience.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.

















.png)


