AiPrise
10 min read
September 17, 2025
Online Identity Verification Methods: 7 Different Types

Key Takeaways










Recent data shows that authorities received over 1.1 million identity theft reports, highlighting the massive scale of fraud targeting businesses and consumers. This widespread activity creates significant challenges for any organization handling customer data or financial transactions.
Organizations face increasing issues with verifying customer identities quickly and accurately while maintaining regulatory compliance. The challenge involves selecting the right verification methods that balance security, user experience, and operational efficiency.
In this guide, we cover the essential online identity verification methods available to businesses, helping you choose which approaches work best for different uses and risk profiles.
Key Takeaways:
- Online identity verification methods replace manual processes with digital solutions that verify customer identities fast, while reducing fraud risk.
- Businesses need identity verification to prevent fraud losses, meet regulatory requirements, and build customer trust in digital transactions.
- Different verification types exist, including document verification, biometric authentication, database checks, knowledge-based questions, address validation, behavioral analysis, and phone verification.
- Biometric verification with liveness detection stops synthetic identity fraud that document-only methods miss.
- Combining multiple verification methods reduces false positives while catching more fraudulent attempts than single-method approaches.
What Are Online Identity Verification Methods?
Online identity verification methods are digital processes that confirm a person's identity using various data points and technologies. These methods replace traditional in-person verification by analyzing documents, biometric data, behavioral patterns, and database records to establish trust in remote transactions.
For example, when you open a bank account online, the institution might ask you to photograph your driver's license, take a selfie, and provide your Social Security number. The system then verifies your document's authenticity, matches your selfie to the license photo, and cross-checks your information against government databases.
Financial institutions use these methods to comply with Know Your Customer (KYC) regulations, while e-commerce platforms rely on them to prevent fraudulent account creation and protect legitimate users from identity theft.
Identity verification has become essential as businesses recognize the limitations of single-method approaches and adopt multi-layered verification strategies.
Why Identity Verification Is Essential for Your Business?

Implementing effective identity verification protects your organization from multiple risks while enabling growth opportunities you might not have considered. Here’s why identify verification is important for your business:
- Fraud prevention: Advanced verification methods can reduce fraudulent account creation significantly, protecting both your business and legitimate customers.
- Risk mitigation: Proper identity verification helps identify high-risk customers early, allowing you to adjust monitoring and transaction limits appropriately.
- Customer trust: Visible security measures increase customer confidence in your platform, leading to higher conversion rates and customer retention.
- Operational efficiency: Automated verification reduces manual review costs while processing customers faster than traditional methods.
- Global expansion: Wide verification capabilities enable you to enter new markets while maintaining consistent security standards.
Knowing about the importance is good, but it’s also essential to know about the different verification methods so that you can select the right one for your needs.
Top 7 Types of Online Identity Verification Methods
Different verification methods serve specific purposes and offer different levels of security. The key is selecting the right combination based on your risk tolerance and regulatory requirements.

Let's explore each method in detail so that you can make informed decisions about implementation.
1. Document Verification
Document verification analyzes government-issued identification documents to confirm authenticity and extract customer information. Modern systems can process a wide range of document types from different countries, making this the most universally applicable verification method.
Here’s how the document verification process works:
- Image capture: System captures high-quality photos of the front and back of identity documents.
- OCR extraction: Optical character recognition technology extracts text data from document images automatically.
- Template matching: Documents are compared against known authentic templates to identify potential forgeries.
- Security feature analysis: System checks for holograms, watermarks, and special fonts that indicate document authenticity.
- Data validation: Extracted information is cross-referenced for consistency between different document fields.
Best For: Primary identity verification for financial services, cryptocurrency exchanges, and any business requiring government-issued ID confirmation. This method works particularly well for international customer bases where multiple document types need support. Document verification using AI has improved accuracy rates while reducing processing times significantly.
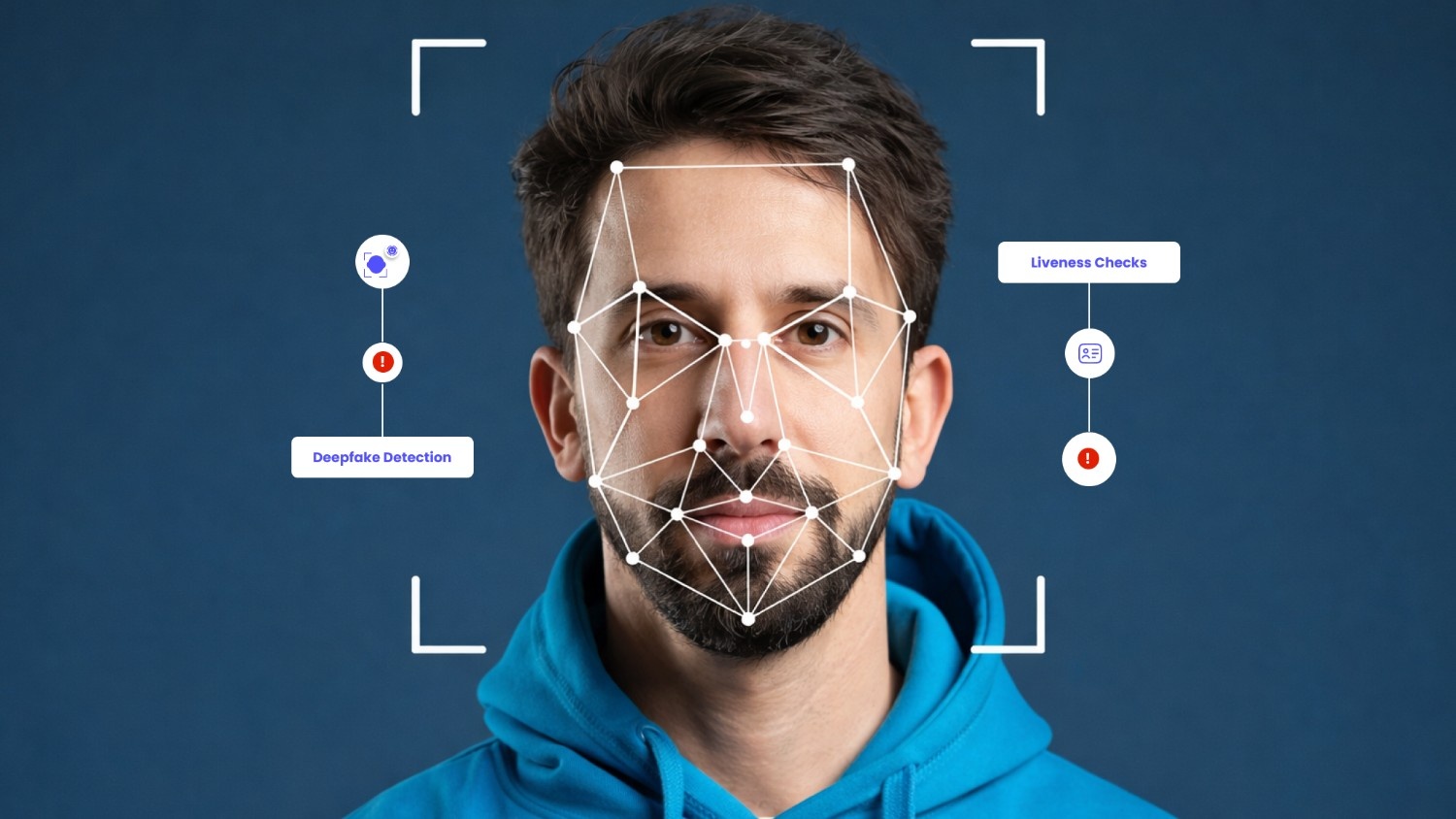
2. Biometric Verification
Biometric verification uses unique physical characteristics like facial features, fingerprints, or voice patterns to confirm identity. This method provides strong protection against synthetic identity fraud and account takeovers since biometric data is extremely difficult to replicate.
Here's how the process works:
- Capture biometric sample: Customer provides a selfie, fingerprint, or voice recording through their device.
- Feature extraction: The system identifies unique biometric markers that distinguish individuals.
- Liveness detection: Advanced checks ensure the person is physically present rather than using photos or recordings.
- Template comparison: Biometric data is compared against reference samples from identity documents or previous sessions.
- Match scoring: The system generates confidence scores indicating the likelihood of a successful identity match.
Best For: High-security applications like banking, healthcare, and cryptocurrency platforms where preventing impersonation attacks is critical. Liveness detection makes this method particularly effective against sophisticated fraud attempts using deepfakes or stolen photos.
3. Database Verification
Database verification cross-checks customer information against authoritative data sources, including government records, credit bureaus, and telecommunications databases. This method provides instant validation of identity details without requiring document uploads or biometric capture.
The verification process includes:
- Data submission: Customer provides basic identity information like name, date of birth, and ID number.
- Database queries: System queries multiple authoritative databases simultaneously for matching records.
- Record matching: Algorithms compare submitted information against database records for consistency.
- Confidence scoring: The system generates match scores based on data consistency across multiple sources.
- Real-time results: Verification results are returned within seconds for immediate decision-making.
Best For: Quick identity confirmation for low-friction onboarding, account recovery, and step-up authentication. Database verifications work particularly well in countries with digital identity systems where real-time database access is available.
4. Knowledge-Based Authentication
Knowledge-based authentication verifies identity by asking questions that only the legitimate person should know, typically derived from credit history, public records, or previous transactions. This method works well for step-up verification when additional security is needed.
The authentication process involves:
- Question generation: The system creates questions from credit reports, public records, or transaction history.
- Multi-choice format: Questions are presented with multiple answer choices to prevent guessing.
- Time limits: Responses must be provided within specific timeframes to prevent research attempts.
- Scoring algorithm: Correct answers are weighted based on question difficulty and data sensitivity.
- Pass/fail determination: Overall scores determine whether verification succeeds or requires alternative methods.
Best For: Step-up authentication for existing customers, account recovery processes, and situations where document or biometric verification isn't practical. Works best when combined with other verification methods rather than as a standalone solution.
5. Address Verification
Address verification confirms that customers live at the addresses they provide, supporting both compliance requirements and fraud prevention efforts. This process typically involves validating addresses against postal databases and requiring proof of residence documents.
The verification process includes:
- Address standardization: System formats addresses according to postal service standards for consistency.
- Database validation: Addresses are checked against official postal databases to confirm existence.
- Proof document analysis: Utility bills, bank statements, or government letters are analyzed for authenticity.
- Document matching: Address details are compared between submitted documents and customer-provided information.
- Utility data checks: Active utility connections are verified to confirm the current residence.
Best For: Financial institutions with regulatory requirements for proof of residence, international money transfer services, and businesses operating in multiple jurisdictions. Proof of address verification becomes particularly important for tax reporting and anti-money laundering compliance.
6. Behavioral Analysis
Behavioral analysis monitors user actions and device characteristics to identify suspicious patterns that might indicate fraudulent activity. This method provides ongoing protection beyond the initial verification process.
Key components include:
- Device fingerprinting: Analysis of browser characteristics, screen resolution, and installed software creates unique device identifiers.
- Behavioral biometrics: Typing patterns, mouse movements, and touchscreen interactions are analyzed for user identification.
- Session monitoring: User actions during verification sessions are tracked for consistency with expected behavior.
- Anomaly detection: Machine learning algorithms identify deviations from normal user behavior patterns.
- Risk scoring: Behavioral data is converted into risk scores that trigger additional security measures when needed.
Best For: Continuous monitoring applications, account takeover prevention, and situations where ongoing identity validation is required. Particularly effective for protecting high-value accounts and detecting credential theft after successful account creation.
7. Phone Verification
Phone verification confirms that customers have access to the phone numbers they provide by sending codes via SMS or voice calls. This method validates contact information while providing a basic identity signal.
The verification process works through:
- Number validation: Phone numbers are checked for proper formatting and carrier assignment.
- Code generation: Unique verification codes are created and sent to the provided number.
- Delivery confirmation: System tracks whether codes are successfully delivered to the target number.
- Code entry: Customers enter received codes within specified time limits to complete verification.
- Carrier intelligence: Additional data about phone carriers and number types can indicate risk levels.
Best For: Contact information validation, two-factor authentication, and low-friction verification scenarios. Phone number verification works well as a supporting method in multi-factor authentication schemes.
With so many different methods, it’s easy to get overwhelmed about which option will work best for your needs. Let’s find out how you can select the best option for your needs.
How to Choose the Right Identity Verification Methods?

Selecting appropriate verification methods requires analyzing your specific business requirements, risk tolerance, and customer expectations. The right combination varies significantly between industries and use cases.
Start by evaluating these key factors:
- Risk assessment: Determine acceptable fraud levels and regulatory requirements for your industry and customer segments.
- Customer demographics: Consider your target audience's technical comfort level and document availability across different markets.
- Transaction values: Higher-value transactions justify more thorough verification processes and associated costs.
- Regulatory environment: Different jurisdictions require specific verification approaches and documentation standards.
- Integration capabilities: Assess your technical team's ability to implement and maintain different verification technologies.
- Budget constraints: Balance verification costs against potential fraud losses and operational efficiency gains.
- Performance requirements: Define acceptable processing times and accuracy standards for your customer experience.
- Scalability needs: Ensure selected methods can handle projected volume growth without degrading performance.
Many organizations benefit from starting with basic methods and gradually adding more sophisticated verification as volumes and risks increase. But having the right technology can make a big difference in the online identity verification process.
Verify Identities and Scale Globally with AiPrise

Managing multiple verification methods across different markets becomes complex without the right technology platform. AiPrise provides a complete solution that combines all verification approaches into a single, configurable workflow that adapts to your specific requirements.
Here are some of the different ways AiPrise can help you:
- Document verification coverage: Verify ID documents from any country with automated data extraction and tamper detection that catches forged documents instantly.
- Address validation tools: Verify customer locations using utility data and document analysis that meets regulatory compliance requirements.
- Risk-based fraud scoring: Apply appropriate verification levels based on customer risk profiles, transaction amounts, and behavioral patterns.
- Complete case management: Track verification performance and manage review queues through a unified dashboard with complete audit trails.
- One-click verification: Verify customers using just ID numbers and selfies for markets where government database access is available.
AiPrise helps you reduce verification complexity while maintaining high security standards across all markets and customer segments.
Final Thoughts
Online identity verification methods continue evolving as fraudsters develop new attack vectors and regulations become more stringent. The most successful organizations adopt flexible, multi-layered approaches that can adapt to changing threats while maintaining excellent user experiences.
Document verification, biometric authentication, and database checks form the foundation of modern identity verification, but the specific combination you choose should align with your risk tolerance, regulatory requirements, and customer expectations. Consider starting with a platform like AiPrise that provides access to multiple verification methods through a single integration.
The investment in effective identity verification can help you significantly through reduced fraud losses, improved regulatory compliance, and enhanced customer trust. Book A Demo to explore how advanced verification technology can improve your customer onboarding process while protecting your business from evolving threats.
FAQs
1. What is the most secure online identity verification method?
Biometric verification combined with document authentication provides the highest security level. This approach verifies both document authenticity and confirms the person presenting the document is the legitimate owner.
2. How long does online identity verification typically take?
Most automated verification methods complete within 30-60 seconds. Document verification takes 30-60 seconds, while biometric and database checks process in 10-30 seconds for immediate results.
3. Can identity verification methods work for international customers?
Yes, modern verification platforms support documents from different countries and can verify identities globally. Database verification availability varies by country, depending on government data access.
4. What happens if a customer fails identity verification?
Failed verifications typically trigger manual review processes or alternative verification methods. Customers may need to provide additional documentation or complete enhanced due diligence procedures.
5. Are automated identity verification systems accurate?
Yes, leading verification systems achieve high accuracy rates when combining multiple methods. Single-method approaches typically achieve good accuracy depending on the verification type and data quality.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.





Speed Up Your Compliance by 10x
Automate your compliance processes with AiPrise and focus on growing your business.








.png)






.png)












.png)

.png)
.png)











