AiPrise
10 min read
December 2, 2025
Deepfake Selfie Verification in Identity Checks

Key Takeaways










A single manipulated pixel can quietly derail even the most sophisticated digital onboarding workflows in minutes.
Rising fraud losses strain operations, while tighter regulations and manual review bottlenecks slow customer acquisition dramatically. In 2025, the Federal Reserve reported deepfake attacks increased twentyfold over the previous three years. High false positives, lengthy manual checks, and costly chargebacks make risk decisions both expensive and operationally draining. By understanding deepfake mechanics, you can design layered defenses that lower false accepts while preserving customer experience.
Key Takeaways
- Deepfake selfie attacks are rising fast, using AI-generated faces to bypass traditional ID and selfie verification systems.
- Layered defenses, like liveness detection, biometric checks, and document validation, help identify real users and block manipulated media.
- High-quality selfie capture, proper lighting, and device intelligence significantly improve verification accuracy and reduce manual reviews.
- Multi-technology verification builds trust across industries, keeping onboarding secure, compliant, and seamless for legitimate customers.
What is Selfie Verification?
A deepfake selfie attack occurs when someone uses AI-generated facial images or videos to trick your verification system. These manipulated selfies can perfectly mirror natural expressions and lighting, slipping past weak or outdated security layers. When paired with stolen or forged IDs, they let impostors move through your onboarding process like real customers. That single lapse can cost you revenue, invite compliance penalties, and weaken the trust your business worked hard to build.
Understanding how deepfake selfie attacks manipulate weak points in this process shows why stronger verification layers are no longer optional.
Why Photo ID Verification Became Essential?
Photo ID verification became essential because manual reviews could no longer keep pace with compliance, fraud, and onboarding demands. As onboarding volumes grew and risks multiplied, stronger digital checks became the foundation of every secure verification process.
Here are the key reasons why photo ID verification became vital for your operations:
- Manual ID checks increased delays and caused costly verification errors that directly impacted onboarding speed and compliance accuracy.
- Paper-based processes created inconsistency across regions, exposing financial institutions to higher audit findings and reputational risks.
- Digital ID verification brought faster, data-backed validation that allowed regulated entities to meet KYC and AML obligations efficiently.
- Electronic verification provided a secure audit trail, giving regulators clear visibility when reviewing your organization’s internal controls.
- Automated selfie verification added a dynamic layer of defense, confirming that each applicant’s face truly matched their official ID.
Yet even the best verification systems can leave blind spots, and that’s exactly where deepfakes find their way in.
Also read: Understanding Identity Verification (IDV) and its Significance
How Can Deepfakes Exploit The Weaknesses of IDV Systems?
Deepfakes take advantage of small gaps in your identity verification process that seem harmless but create big risks.
When different checks don’t work together, fake identities can slip through before your system even notices.
Here’s how these weaknesses show up in your verification flow:
- Selfie checks that don’t confirm real movement make it easy for deepfakes or pre-recorded videos to pass.
- Face-matching tools that only compare photos miss signs of digital editing or AI-generated features.
- Skipping a check on the ID’s authenticity lets fake or stolen documents appear valid.
- Ignoring signals from a user’s device or network means replayed or screen-based attacks go undetected.
Knowing how attackers exploit these gaps makes it easier to grasp the key components of a reliable deepfake detection framework.

Key Components of a Deepfake Detection System
A strong deepfake detection system doesn’t rely on a single check; it combines multiple layers that work together to confirm identity and detect manipulation. Each layer strengthens your verification process, reducing the chance of false approvals and improving fraud prevention accuracy.
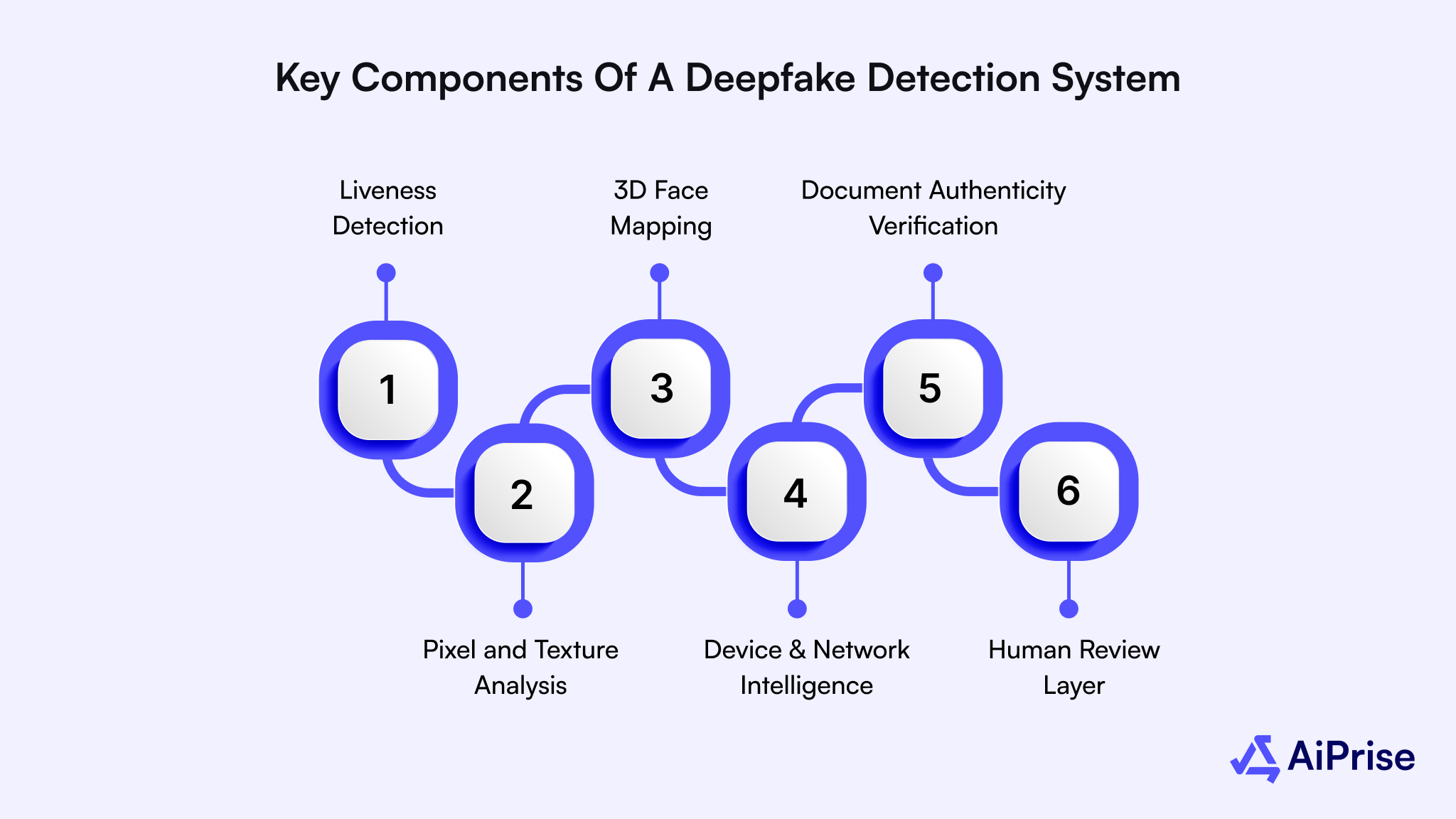
1. Liveness Detection
Liveness detection helps your system confirm that the person in front of the camera is real and not a recorded video. It checks small natural movements like blinking or head turns to prove live presence during verification. This simple yet powerful step blocks deepfakes that use still images or pre-recorded clips.
2. Pixel and Texture Analysis
Advanced AI models study the image’s pixel structure, lighting, and texture to identify even the slightest digital alterations. These detectors look for irregularities in skin tone, shadows, or reflections that AI-generated faces often fail to replicate. By analyzing such patterns, you can spot deepfakes that appear flawless to the human eye.
3. 3D Face Mapping
3D face mapping builds a digital model of facial geometry to verify real depth and shape. It ensures that what’s being captured isn’t a flat image but an actual three-dimensional face. This step prevents synthetic overlays or projected visuals from passing as genuine selfies.
4. Device and Network Intelligence
Your system can detect suspicious activity by analyzing the device and network used during verification. Signals like virtual cameras, remote access tools, or unusual IP addresses reveal possible replay or injection attacks. This extra layer helps you filter out fake sessions before they reach manual review.
5. Document Authenticity Verification
Checking the ID document itself is just as important as verifying the selfie. Using OCR and image analysis, your system can confirm if a document is real, expired, or tampered with. Strong document validation stops attackers from pairing fake selfies with forged IDs to complete fraudulent sign-ups.
6. Human Review Layer
Automated systems handle most checks, but a trained human eye is vital for complex or high-risk cases. Manual reviewers step in when an image looks suspicious or when automated results are uncertain. This balance of AI and expert review ensures accuracy without compromising speed or customer experience.
With these components working together, it becomes clearer how modern selfie verification operates in real-world onboarding environments.
Also read: Understanding Deepfake Legal Implications and Actions
How Selfie Verification Works
Selfie verification follows a series of layered checks that work together to confirm both identity and authenticity. Each layer adds protection, ensuring fraudsters face multiple barriers before gaining access.
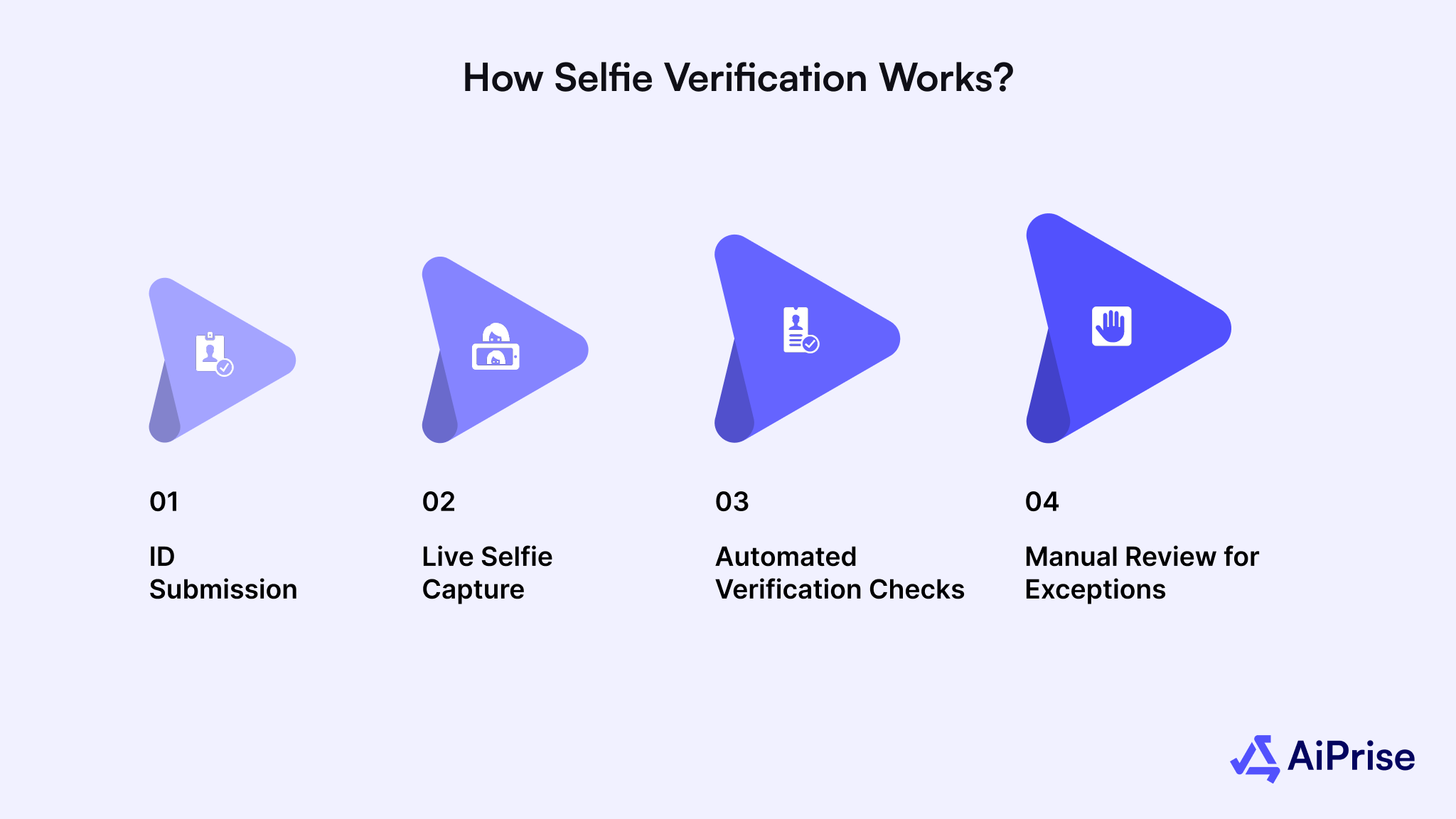
Step 1: ID Submission
- The process begins when a user submits a valid government-issued ID, such as a passport, driver’s license, or national ID.
- Some systems also accept NFC-enabled passports or digital IDs, which provide encrypted data for stronger validation.
Step 2: Live Selfie Capture
- The user is prompted to take a live selfie or short video using a mobile app or webcam.
- This step verifies that the person present matches the face on the submitted ID in real time.
Step 3: Automated Verification Checks
- The system uses OCR to extract and verify ID details against internal and regulatory databases.
- Facial recognition compares the live selfie with the ID photo to confirm identity consistency.
- Liveness and deepfake detection tools analyze facial movements, texture, and depth to ensure authenticity.
- Device intelligence checks network data, browser signals, and camera activity to detect replay or injection attempts.
Step 4: Manual Review for Exceptions
- Any cases flagged by the system for risk or inconsistency are escalated to human reviewers.
- This step ensures that suspicious attempts or unclear images receive expert validation before approval.
Through this layered flow, your verification process balances speed, compliance, and fraud protection without disrupting the onboarding experience.
Once the process is in place, the next challenge is ensuring users capture verification selfies that actually meet system standards.
Best Practices for Collecting Verification Selfies
Clear and guided selfie collection improves verification accuracy and minimizes manual intervention across your onboarding flow. When users know exactly what’s expected, your compliance and risk teams can focus on high-risk cases instead of correcting poor submissions.
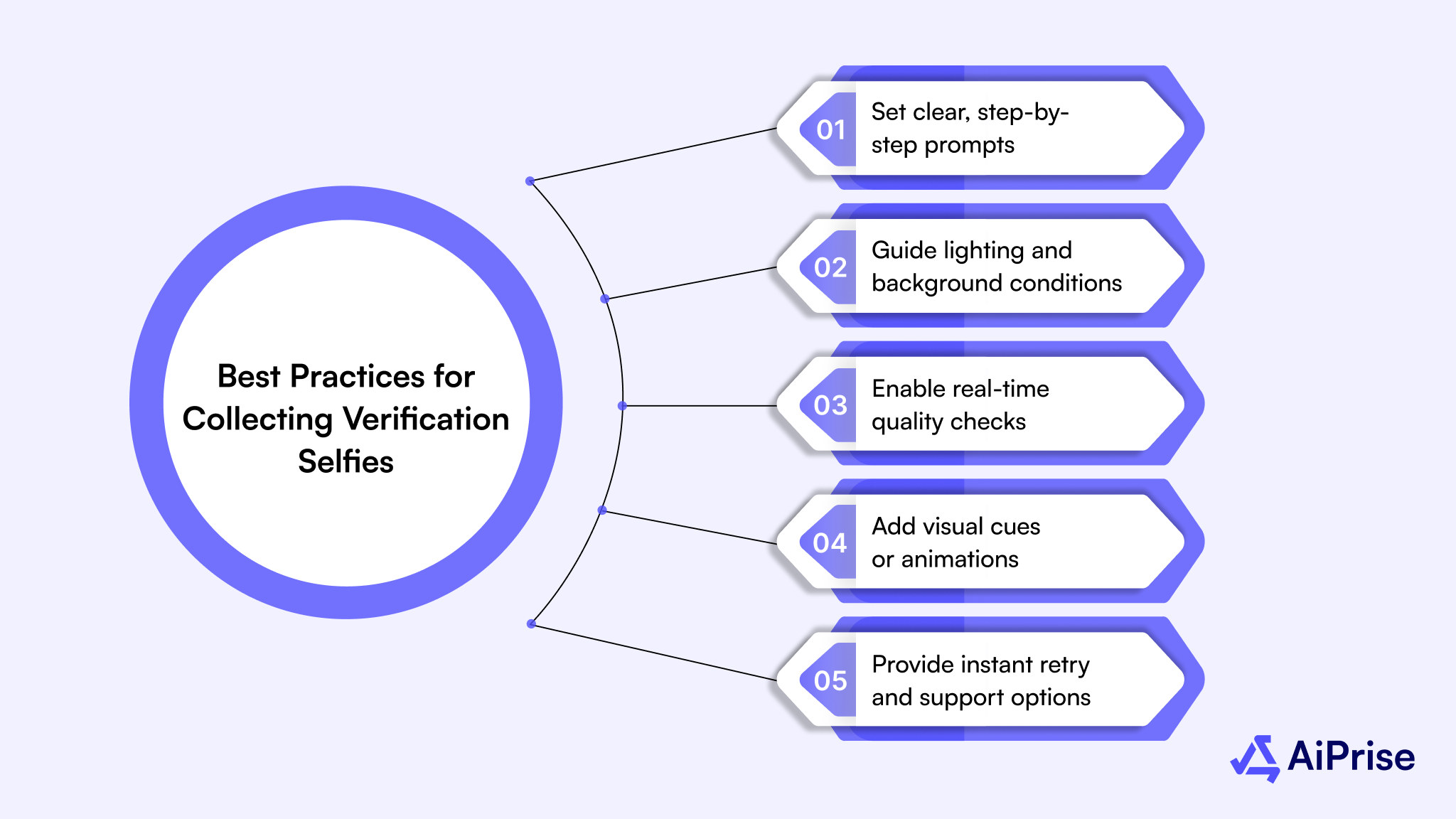
Here are some practical steps you can apply to make the process more effective:
Set clear, step-by-step prompts
- Display short, on-screen instructions showing how to position the face and ID correctly.
- Use progress indicators to reassure users and reduce incomplete submissions.
Guide lighting and background conditions
- Provide visual examples of good versus poor lighting to prevent glare or shadows.
- Suggest neutral backgrounds to ensure the user’s face and ID stay in focus.
Enable real-time quality checks
- Integrate automatic feedback that flags blurry or cropped selfies before upload.
- Offer instant retake options so users can fix errors immediately.
Add visual cues or animations
- Include on-screen outlines to guide users in aligning their face and ID within the frame.
- Use simple animations to prompt natural head movements or blinking for liveness detection.
Provide instant retry and support options
- Allow quick reattempts instead of sending poor images for manual review.
- Offer in-app support or chat prompts for troubleshooting during the capture process.
When the capture quality is high, the underlying technologies take over, powering every layer of identity and deepfake verification.
Key Technologies Behind Selfie Verification
Understanding the technology behind selfie verification is essential for evaluating how well your system detects and prevents deepfake attacks. Below is a table showing key technologies, their purposes, and how they help fight deepfake attacks in your verification flow.
Each of these technologies plays a vital role across different industries, and the benefits vary depending on how verification is applied.
Benefits of Verification Selfies for Different Industries
Verification selfies deliver measurable value across industries that depend on secure and compliant customer onboarding. By combining automation, AI-driven checks, and human review, each sector gains a balance of security, compliance, and customer experience.

1. Financial Institutions
Banks and lending organizations benefit from faster account openings and reduced dependency on manual document reviews. Automated selfie verification minimizes onboarding fraud, supports AML compliance, and provides verifiable audit trails for regulators. Real-time facial matching also lowers the risk of account takeovers and fraudulent loan applications.
2. Payment Providers
Payment processors and digital wallets can validate user identities instantly without disrupting transactions. Selfie verification prevents unauthorized account creation and limits chargeback-related losses. Stronger identity checks also boost merchant and consumer confidence in the platform’s security.
3. Cryptocurrency Platforms
Crypto exchanges and wallet providers use selfie verification to meet strict KYC and AML requirements. AI-powered face matching helps confirm user legitimacy and block synthetic or duplicate accounts. This layer of security improves trust among investors while protecting against regulatory violations.
4. E-commerce Companies
Online retailers and marketplaces use verification selfies to detect fraudulent buyer or seller accounts. Automated checks reduce payment disputes and enhance customer trust during high-value transactions. Verification also helps prevent identity abuse during refunds or loyalty program enrollments.
5. Government and Public Services
Digital ID programs, licensing authorities, and benefit portals use selfie verification to confirm legitimate access. Real-time checks help prevent identity misuse and ensure only eligible individuals receive services. The secure audit trail simplifies compliance with federal data protection and identity assurance standards.
Even with these advantages, security remains a common concern, which raises an important question about the reliability of selfie verification itself.
Also read: Crypto exchanges and identity verification

Is Selfie Verification Secure?
Selfie verification is secure when it combines multiple safeguards instead of relying on a single check. AI-driven liveness detection, deepfake analysis, and biometric authentication work together to confirm a user’s real presence and identity. Encrypted data storage and compliance with privacy laws like GDPR and CCPA further protect personal information from misuse. When supported by regular model updates and human oversight, selfie verification remains a trusted and compliant defense against evolving fraud risks.
To maintain that level of trust and accuracy, many organizations now turn to platforms built specifically to detect deepfakes and automate identity checks.
How AiPrise Protects Your System from Deepfake Selfie Fraud?
AiPrise brings together document checks, biometric liveness, and deepfake detection so that manipulated selfies fail before they reach manual review.
Here’s how AiPrise applies those capabilities specifically to deepfake and selfie verification:
- Real-time deepfake detection and image forensics: Models inspect texture, temporal patterns, and motion to flag synthetic or tampered selfies early in the flow.
- Biometrics with active and passive liveness: Face and biometric checks confirm presence through micro-movements and passive signals, blocking replay and screen-injection attempts.
- Document + selfie cross-verification: OCR extracts ID data and compares it with the live selfie, validating document integrity and identity together.
- Single-endpoint API and SDKs for quick integration: A unified API or SDK runs KYC, biometric, AML, and fraud checks without stitching multiple vendors together.
- Configurable workflows and case management: Custom rules route high-risk or ambiguous cases to human reviewers to avoid false accepts and reduce unnecessary reviews.
- Continuous monitoring and global data coverage: Post-onboarding screening and watchlist checks help spot emerging deepfake-linked behavior or sanctions hits.
- Developer tooling and performance metrics: SDK playgrounds, country-level templates, and warning codes provide visibility into error types, decision times, and escalation triggers.
Wrapping Up
Deepfake selfie attacks are quickly becoming one of the most serious threats to digital identity verification worldwide. Strengthening your verification process with multi-layered checks helps reduce fraud exposure and maintain regulatory confidence across every onboarding flow. Combining advanced AI tools with simple, user-friendly verification steps ensures security never comes at the cost of customer experience.
AiPrise helps you build this balance through real-time deepfake detection, biometric authentication, and continuous compliance monitoring. Its AI-powered platform verifies identities faster, flags manipulated selfies instantly, and maintains global accuracy for KYC and AML checks.
Book A Demo today to see how AiPrise can protect your verification system and secure every digital interaction.
FAQ
1. What exactly is selfie verification, and how does it work in KYC?
Selfie verification requires a live selfie to be captured and compared with a government-issued ID photo, thereby proving both identity and presence.
2. Why are deepfakes such a threat to remote identity verification?
Deepfakes use AI to generate realistic images or videos that impersonate legitimate users and can bypass traditional selfie/ID checks lacking anti-spoof controls.
3. Can multi-layer checks really stop deepfake selfie attacks?
Yes, combining liveness detection, document authenticity, device intelligence, and behavioral signals creates multiple hurdles fraudsters must overcome.
4. What types of IDs are typically required for selfie verification?
Most systems require a government-issued photo ID, such as a passport or driver’s license, sometimes enhanced by an NFC chip or certificate when supported.
5. Does selfie verification add friction for legitimate customers?
If designed well with progressive risk flows and good UX prompts, selfie verification can boost conversion while strengthening security, but poorly designed flows risk drop-off.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.

















.png)


