AiPrise
13 min read
December 18, 2025
10 AML Typologies Every Bank Needs to Know in 2026

Key Takeaways










Money launderers are constantly evolving, using increasingly sophisticated methods to move illicit funds through the financial system. AML typologies, the common patterns and techniques used in money laundering, help financial institutions and regulators recognize these schemes before they escalate into major financial crimes.
For example, a typology might involve a series of small, structured deposits across multiple accounts to avoid reporting thresholds, known as smurfing. By identifying this pattern early, banks can flag suspicious activity, investigate potential risks, and prevent illegal funds from circulating.
In this guide, we explore the most common AML typologies, their significance, and how institutions can use this knowledge to detect and prevent money laundering effectively.
Key Takeaways
- Money launderers use multi-channel smurfing, crypto, and shell companies to hide illicit funds in 2026.
- Trade-based laundering and real estate schemes remain hard-to-detect channels for cross-border illicit flows.
- Identity fraud, synthetic accounts, and underground banking amplify AML risks for banks and fintechs.
- Incorporating typologies into risk scoring, behavioral analytics, and transaction monitoring strengthens AML.
- AiPrise enhances compliance by detecting typology patterns, scoring risk, and monitoring suspicious activity in real time.
What Is the Relevance of AML Typologies in 2026?
In 2026, AML typologies play a critical role in helping banks, fintechs, and payment processors detect emerging financial crime earlier and strengthen their risk controls.
Instead of relying on basic rule-based monitoring, institutions now use typologies to understand how laundering schemes actually work, what red flags they generate, and how these behaviors evolve across digital payments, crypto, cross-border transfers, and embedded finance.
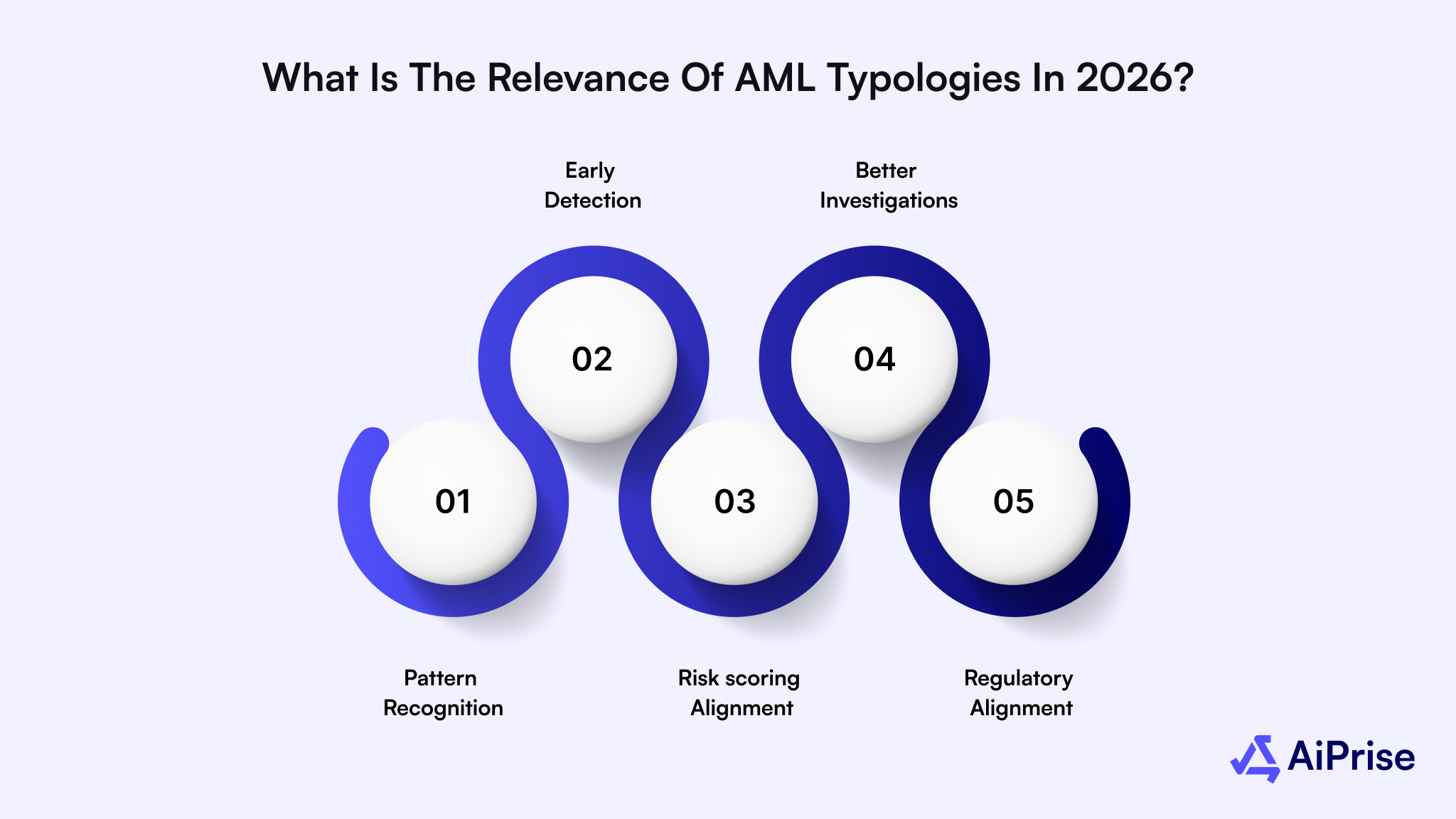
Here are some of the key capabilities AML typologies enable:
- Pattern recognition: Institutions can identify behaviors associated with known laundering methods like structuring, mule networks, trade-based laundering, layering, crypto mixing, and more.
- Early detection: Typologies help compliance teams detect suspicious activity before it becomes large-scale, e.g., unusual velocity, circular flows, rapid account-to-account movements.
- Risk scoring alignment: Modern AML systems use typology-based risk models to assign higher scores to customers or transactions displaying markers of known laundering activity.
- Better investigations: Typologies guide analysts by showing what behaviors or transaction patterns warrant deeper review or escalation.
- Regulatory alignment: Global regulators, including FATF, FinCEN, and EU AML authorities, publish typologies that institutions must understand and incorporate into their programs.
How it works: A processor notices a new customer receiving dozens of small deposits from unrelated accounts, all quickly forwarded to a foreign exchange platform. This matches a documented mule account typology.
The system flags the pattern, raises the user’s risk score, and triggers enhanced due diligence before further transactions are allowed.
By applying typologies this way, institutions can detect laundering schemes early, respond faster, and build AML programs that adapt to shifting criminal tactics.
In short, AML typologies give financial institutions a structured, intelligence-driven method to detect and prevent money laundering in a rapidly evolving financial ecosystem.
Suggested Read: How to Spot a Fake Identity: A Guide to Combating Synthetic Fraud
Upgrade your AML program with the Fraud and Risk Scoring solution. Discover how AiPrise helps institutions detect typology-linked behaviors faster and reduce false positives with adaptive, real-time scoring.
Top 10 AML Typologies to Watch Out For in 2026
AML risks are evolving quickly as criminals blend traditional methods with digital tools, instant payments, and cross-border platforms. Understanding emerging typologies helps institutions detect unusual behavior, reduce false positives, and meet rising regulatory expectations.

Here are some of the high-risk AML typologies that banks should be aware of in 2026:
Structuring and Smurfing Across Multiple Channels
Structuring (or smurfing) remains one of the most common AML typologies, but today it has become more sophisticated. Instead of limiting activity to bank branches, criminals now spread micro-transactions across multiple channels like cash, digital wallets, prepaid instruments, and cross-border fintech rails, making suspicious patterns harder to detect.
How this is carried out:
- Micro-transactions across mixed channels: Funds are broken into small amounts and routed through ATMs, mobile wallets, payment apps, and branch deposits to avoid triggering automated thresholds.
- Use of mules and synthetic identities: Criminal networks recruit individuals (or create synthetic profiles) to conduct repeated low-value transactions, further obscuring the source of funds.
- Prepaid and offshore-issued cards: Reloadable cards, especially those issued in offshore jurisdictions with weaker controls, are used to distribute and move funds anonymously before consolidation.
Multi-channel smurfing requires institutions to analyze behavior holistically across products and profiles instead of monitoring each channel in isolation. Detecting this typology now depends on recognizing unusual velocity, cross-channel transaction patterns, and coordinated mule activity rather than single red-flag events.
Shell Companies and Hidden Beneficial Ownership
Shell companies and opaque ownership structures remain core to modern layering schemes. Criminals increasingly rely on paper-only entities, nominee arrangements, and offshore jurisdictions to mask true ownership and distance illicit funds from their origin.
How this is carried out:
- Nominee directors and straw owners: Individuals with no real control are listed as directors or shareholders, allowing the true controller to stay hidden while transactions appear legitimate on paper.
- Multi-layered offshore structures: Criminals chain entities across multiple tax havens, each with limited disclosure requirements, making BO (beneficial ownership) tracing slow, fragmented, or impossible.
- Dormant or zero-activity companies: Companies with no real operations are used to move large, irregular payments under the guise of “consulting,” “imports,” or “professional services.”
Hidden beneficial ownership continues to be a major vulnerability, especially for institutions lacking strong KYB and BO verification workflows. Detecting this typology depends on analyzing ownership inconsistencies, unusual transaction behavior, and mismatches between a company’s stated activity and its financial footprint.
Trade-Based Money Laundering (TBML)
Trade-based money laundering (TBML) remains one of the hardest typologies to detect. Over/under-invoicing, fake shipments, and manipulated commodity values continue to rise, especially in high-volume ASEAN trade corridors with limited cross-border data visibility.
How this is carried out:
- Over- or under-invoicing goods: Criminals inflate or deflate invoice values to move value across borders without triggering suspicion, often routing shipments through low-visibility ports.
- Phantom or duplicated shipments: Fake bills of lading or reused documents create the appearance of legitimate trade, allowing large transfers to pass as commercial payments.
- Commodity mispricing and misclassification: Goods are intentionally mispriced or assigned incorrect HS (Harmonized System) codes to justify large value gaps between actual and declared worth.
TBML thrives where trade documentation is fragmented and cross-border systems don’t communicate. Detecting it requires comparing invoice data, shipping documents, partner profiles, and historical pricing patterns, something many institutions still lack. Advanced risk scoring and anomaly detection can significantly reduce blind spots.

Crypto Laundering via Mixers, DEXs, and Privacy Coins
Crypto laundering has become faster and harder to trace as criminals move from mainstream Bitcoin activity into layer-2 networks, decentralized exchanges (DEXs), privacy coins, and cross-chain bridges. These tools provide speed, liquidity, and anonymity, making laundering patterns significantly more complex.
How this is carried out:
- Using mixers and peel-chain techniques: Mixers pool and redistribute funds to break on-chain links, while peel-chains repeatedly split transactions into smaller transfers to obscure the origin.
- Routing funds through DEXs and cross-chain bridges: DEX swaps and bridge transfers quickly shift assets between blockchains, preventing consistent tracking by relying on multiple networks’ lack of shared oversight.
- Moving value through privacy coins and L2 ecosystems: Monero, Zcash, and zero-knowledge layer-2 chains offer built-in obscurity, making transaction tracing far more limited compared with public blockchains.
Crypto laundering no longer relies on a single chain; it uses a web of mixers, DEXs, L2s, and privacy assets to erase transactional footprints. Institutions need blockchain analytics, flow monitoring, and real-time risk scoring to catch anomalies that traditional tools miss.
Real Estate Laundering Using High-Value Property
Real estate remains a preferred laundering channel because high-value property can absorb large sums, mask ownership, and generate clean proceeds through rental income or resale. The use of LLCs, offshore entities, and proxy buyers continues to make real estate transactions a major compliance blind spot.
How this is carried out:
- Purchasing property through opaque ownership structures: Criminals use LLCs, trusts, nominees, or offshore companies to hide the true buyer, making source-of-funds checks difficult.
- Manipulating property values and financing: Undervaluation, inflated appraisals, and mortgage overpayments introduce illicit funds into the system under the guise of legitimate financing.
- Rapid resale to “clean” the funds: Properties are quickly flipped or transferred among related entities, converting illicit cash into seemingly legitimate proceeds.
Real estate laundering exploits weak ownership transparency, inconsistent KYC on buyers, and fragmented property data. Financial institutions and real estate intermediaries need stronger beneficial ownership checks, source-of-funds verification, and anomaly detection to identify suspicious property-related transactions.
Insurance Product Abuse
Insurance products remain attractive for laundering because they allow large cash inflows, flexible withdrawals, and low scrutiny compared with traditional banking. Early surrenders and cross-border payouts continue to be exploited to convert illicit cash into clean claim proceeds.
How this is carried out:
- Purchasing high‑value policies with illicit funds: Criminals fund life, investment-linked, or annuity policies using cash or structured payments that avoid detection.
- Early surrender to convert funds: Policies are cancelled shortly after purchase, allowing criminals to receive most of the premium back as a “legitimate” refund or claim.
- Redirecting payouts to third parties or offshore accounts: Withdrawals or claim payouts are routed to nominees, shell companies, or overseas banks to break the audit trail.
Insurance abuse thrives where premium funding checks, beneficiary verification, and surrender patterns aren’t monitored closely. Strengthening risk scoring, beneficiary screening, and anomaly detection is essential to spot unusual funding, rapid cancellations, and suspicious payout behavior.
Cash-Intensive Businesses and Mingling
Cash‑heavy businesses remain a popular laundering channel because they let criminals blend illicit funds with genuine daily revenue. Regulators report rising misuse of restaurants, retail outlets, casinos, and convenience stores to disguise large cash inflows as normal business activity.
How this is carried out:
- Mixing illegal cash with legitimate sales: Criminals inflate daily receipts, record fake transactions, or overstate foot traffic to justify unexplained cash deposits.
- Using shell or proxy‑owned businesses: Front businesses, often with weak bookkeeping, are acquired or set up solely to absorb illicit funds under the guise of normal operations.
- Frequent withdrawals and off‑book payments: Funds are rapidly withdrawn, paid to suppliers that don’t exist, or funneled to related entities to complete the laundering cycle.
Mingling thrives in environments with poor cash‑flow visibility and limited controls. Monitoring for irregular spikes in revenue, inconsistent sales patterns, and rapid cash movements is crucial for identifying high‑risk businesses and preventing illicit funds from being legitimized.
Underground Banking/Hawala-Type Transfers
Underground banking and informal value transfer systems like hawala, hundi, and fei ch’ien remain key channels for moving illicit funds without formal banking records. Regulators note increased use of unregistered remitters and mule networks to transfer money across borders anonymously.
How this is carried out:
- Cross-border cash transfers: Funds are deposited domestically and then disbursed abroad through trusted intermediaries, bypassing formal banking systems.
- Use of unregistered or informal remitters: Criminals exploit non-compliant agents to convert cash into foreign currencies, avoiding reporting obligations.
- Mule networks and layered transactions: Multiple individuals are used to move small amounts repeatedly, obscuring the source and trail of illicit funds.
These underground systems exploit gaps in regulation and enforcement. Monitoring for repeated small transfers, unusual remitter activity, and cross-border cash flows is essential to detect and prevent laundering via informal channels.
Money Laundering Through Online Gambling & Gaming Platforms
Online gambling and gaming platforms are increasingly exploited for money laundering. Criminals use casinos and digital games to convert illicit funds into seemingly legitimate winnings, taking advantage of high-volume transactions and complex in-game mechanisms.
How this is carried out:
- Chip or in-game asset purchases with minimal play: Funds are converted into chips or digital items, then cashed out or sold, masking the source.
- Buying “winning” tickets or pre-arranged outcomes: Criminals manipulate bets or purchase tickets to create a record of legitimate winnings.
- High-volume micro-bets and rapid cash-outs: Multiple small transactions obscure fund origins while quickly moving money through the system.
Monitoring unusual betting patterns, rapid cash-outs, and suspicious in-game transactions is crucial. Effective AML controls on gaming platforms can prevent these schemes from funneling illicit funds into the financial system.
Identity Fraud and Synthetic Identities
Identity fraud and synthetic identities remain a major AML risk in 2026. Criminals use fake or stolen identities to open accounts, move funds quickly, and exploit gaps in KYC processes, including on crypto platforms.
How this is carried out:
- Creating synthetic identities: Fraudsters combine real and fabricated personal data to form accounts that pass initial verification checks.
- Using stolen or fake documents: Fake IDs, passports, or utility bills help launder funds through legitimate banking channels.
- Accessing high-risk platforms: Synthetic IDs enable rapid fund transfers, mule accounts, and transactions on crypto or digital finance platforms with weak KYC.
Detecting unusual account activity, validating beneficial ownership, and applying robust KYC/AML controls are essential to mitigate risks from identity fraud and synthetic accounts.
Robust KYC checks, real-time monitoring, and advanced analytics are critical to detect and prevent illicit activity, safeguard assets, and maintain regulatory compliance across traditional and digital finance channels.
Also Read: How AI is Transforming AML Compliance
With a clear understanding of AML typologies, let’s look at how financial institutions can incorporate them into their AML strategies.
Incorporating AML Typologies into Bank Compliance Strategies
Understanding AML typologies is only the first step. Financial institutions must actively integrate this knowledge into their security and compliance frameworks. By doing so, banks can strengthen detection, streamline reporting, and reduce exposure to financial crime.
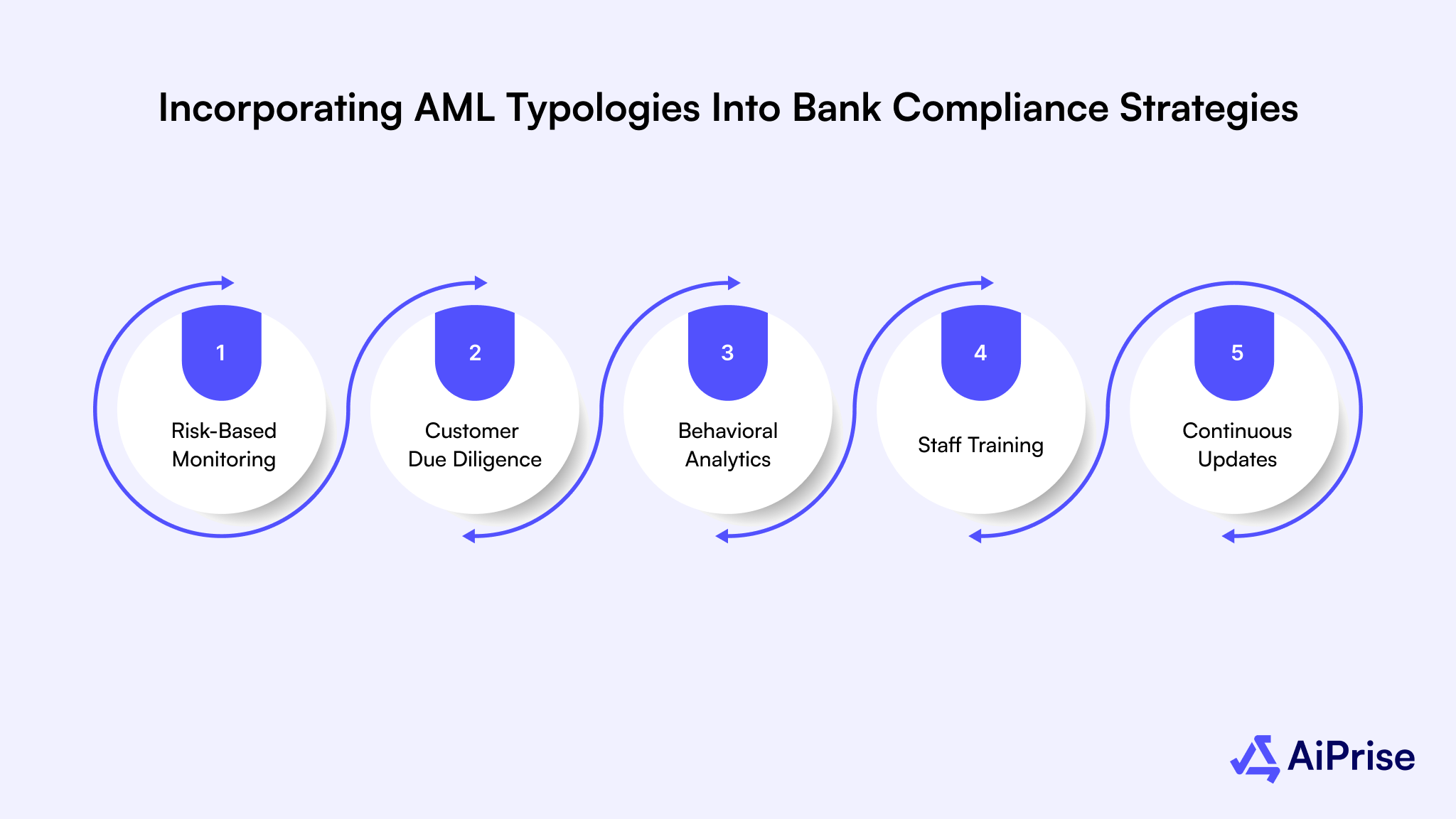
How Banks Can Apply AML Typologies:
- Risk-Based Monitoring: Align transaction monitoring rules with known typologies, flagging suspicious patterns like smurfing, trade misinvoicing, or crypto layering.
- Enhanced Customer Due Diligence: Use typology insights to focus KYC/CDD efforts on higher-risk customers, sectors, or geographies.
- Behavioral Analytics: Combine typology knowledge with AI-driven behavioral analytics to detect anomalies indicative of money laundering.
- Staff Training: Educate compliance teams on emerging typologies to improve red-flag recognition and decision-making.
- Continuous Updates: Incorporate typology reports from regulatory bodies and internal investigations into monitoring systems to stay ahead of evolving methods.
By embedding AML typologies into operational processes, banks can proactively detect illicit activity, strengthen internal controls, and maintain regulatory compliance in an ever-evolving financial crime landscape.
Also Read: How Banks Utilize Machine Learning For Fraud Detection
Financial institutions, fintechs, and payment platforms need tools to spot suspicious activity, monitor high-risk transactions, and act on typology patterns in real time.
How AiPrise Supports AML Typology Detection and Risk Management
Financial institutions, fintechs, and payment platforms need tools to detect suspicious activity, monitor high-risk transactions, and respond proactively to evolving money laundering methods. While typologies provide insights into common laundering patterns, institutions require actionable analytics to operationalize this knowledge.
AiPrise complements AML efforts by integrating behavioral analytics, risk scoring, and real-time monitoring into a unified compliance layer. Key capabilities include:
- Fraud & Risk Scoring: Evaluate customers, entities, and transactions using 100+ signals, including transaction patterns, device data, and adverse media, to flag high-risk clients and synthetic identities early.
- Behavioral & Transaction Analytics: Monitor interactions and transaction flows to detect anomalies, smurfing, layering, or other typology-related activity across accounts and channels.
- Device & Session Intelligence: Identify suspicious device usage, VPNs, emulators, or other attempts to bypass AML controls.
- Flexible Rule Engine: Configure automated alerts and workflows based on typology patterns, internal thresholds, and regulatory requirements, without disrupting legitimate activity.
By combining typology insights with advanced risk scoring and monitoring, AiPrise helps financial institutions stay ahead of money laundering schemes, detect emerging threats, and strengthen AML compliance.
Book a Demo to see how AiPrise enables proactive monitoring of AML typologies, reduces financial crime risk, and enhances operational resilience.

Wrapping Up
As money laundering techniques evolve, financial institutions face increasing complexity in detecting suspicious activity and staying compliant. Understanding and applying AML typologies is essential to identifying risk patterns and preventing illicit transactions.
AiPrise supports these efforts by combining real-time risk scoring, behavioral analytics, and transaction monitoring into a unified platform. By surfacing typology-based risk signals instantly, it helps institutions strengthen AML compliance, reduce exposure, and act decisively against emerging money laundering threats.
Talk to Us Today to see how AiPrise can enhance your AML defenses and operational confidence.
FAQs
1. How often should financial institutions update their AML typology monitoring?
AML typologies evolve rapidly, especially with digital currencies and cross-border trade. Institutions should review and update monitoring systems at least annually, or more frequently when regulators release new guidance or emerging threats are detected.
2. Can AI detect new AML typologies that haven’t been formally documented?
Yes. Advanced AI and machine learning systems can analyze transaction patterns, customer behavior, and network relationships to flag unusual activity, helping detect emerging typologies even before they’re documented in regulatory reports.
3. How do regulators assess an institution’s use of AML typologies in compliance programs?
Regulators evaluate whether institutions incorporate typology insights into risk assessments, transaction monitoring, suspicious activity reporting, and employee training. Demonstrating proactive use of typologies can improve regulatory confidence and reduce compliance risks.
4. Are AML typologies applicable to non-bank financial services like e-wallets or crypto exchanges?
Absolutely. Any financial service handling transactions can be exploited for money laundering. E-wallets, payment processors, and crypto platforms should integrate typology detection into onboarding, transaction monitoring, and fraud prevention.
5. What role does collaborative intelligence play in applying AML typologies effectively?
Sharing typology insights across institutions, industry groups, or regulators improves the detection of complex laundering schemes. Collaborative intelligence allows institutions to identify emerging trends, correlate suspicious activity, and strengthen overall AML defense.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.





Speed Up Your Compliance by 10x
Automate your compliance processes with AiPrise and focus on growing your business.








.png)





.png)













.png)

.png)
.png)











