AiPrise
12 min read
January 6, 2026
Liveness Detection Framework Guide for Secure Identity Verification

Key Takeaways










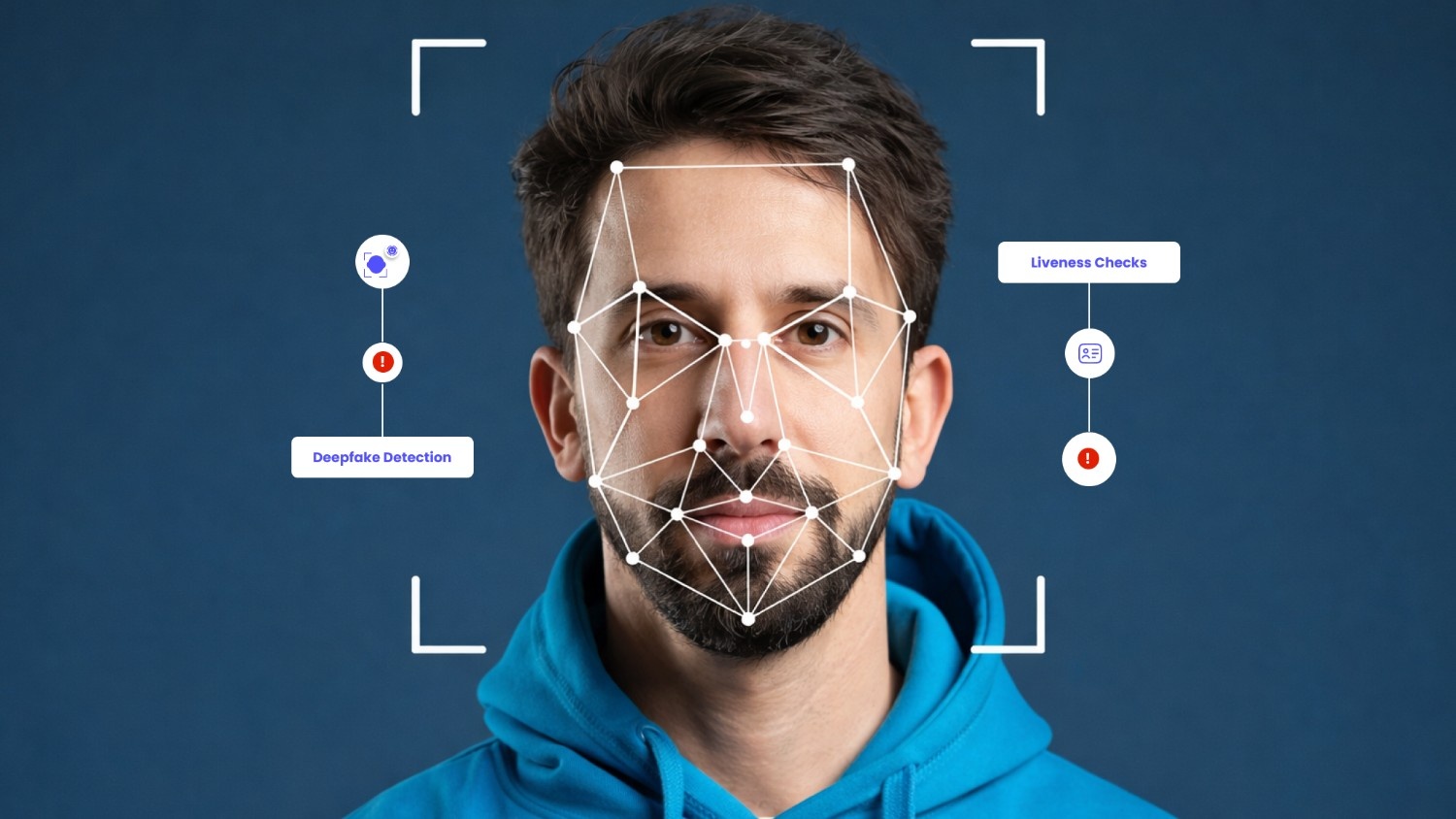
Fraud no longer relies on stolen documents alone. You now face deepfakes, replay attacks, and AI-generated identities that can bypass basic identity checks in seconds. This shift has made liveness detection a critical layer in modern identity verification, especially for regulated businesses operating at scale.
A liveness detection framework helps you confirm that a real person is present during verification, not a spoofed image, video, or automated script. For financial institutions, fintech platforms, and payment providers in the United States, this framework plays a direct role in reducing onboarding fraud, meeting regulatory expectations, and maintaining trust without slowing legitimate users.
In this guide, you’ll know how liveness detection frameworks work, key liveness detection types, and their benefits for secure verification in the United States.
Key Takeaways
- A liveness detection framework confirms real user presence during identity verification, helping block spoofing methods such as photos, videos, masks, and AI-generated media that basic checks may miss.
- Liveness detection is most effective when combined with government ID verification, 1:1 face match, and 1:N face match, rather than used as a standalone control.
- Many liveness detection frameworks rely on cloud-based, serverless architectures to support real-time user interaction while maintaining centralized verification and audit readiness.
- In U.S. KYC workflows, applying liveness detection helps reduce onboarding fraud, limit manual reviews, and meet expectations for verifying real user presence during remote checks.
What Is a Liveness Detection Framework?
A liveness detection framework is the structured approach you use to confirm that a real human is present during an identity verification check. It is designed to detect and block spoofing attempts, such as photos, videos, masks, or synthetic media, before they can bypass verification controls.
As identity verification has moved to remote and digital channels, fraud tactics have evolved beyond stolen documents. Attackers now rely on replay attacks and AI-generated identities that can pass basic document and face-matching checks. A liveness detection framework addresses this gap by providing direct evidence of human presence at the time of verification.
This framework does not replace document verification or biometric matching. Instead, it supports them by strengthening confidence in verification outcomes, reducing uncertainty for review teams, and improving the reliability of onboarding and high-risk actions.
Without a defined liveness detection framework, you may face:
- Higher exposure to onboarding fraud and account misuse
- Increased manual reviews due to unclear verification results
- Weaker audit trails that raise compliance concerns
- Greater risk of synthetic identities entering your system
For regulated businesses in the United States, a liveness detection framework has become a foundational control for secure identity verification, balancing fraud prevention, regulatory expectations, and user trust.
Once you understand what a liveness detection framework is and why it matters, the next step is to look at the different liveness detection types used in modern verification and how they address varying risk and user experience needs.
Also Read: How to Detect Financial Services Fraud: A Practical Guide for Businesses

Key Types of Liveness Detection in Modern Verification
.png)
Liveness detection frameworks rely on different detection approaches depending on risk, user experience requirements, and operational scale. These approaches are commonly grouped into three types: active, passive, and hybrid liveness detection. Each type serves a specific purpose and comes with trade-offs that you should understand before choosing one.
1. Active Liveness Detection
Active liveness detection requires the user to perform a deliberate action during verification to prove they are physically present. These actions are designed to be difficult to replicate using static images, pre-recorded videos, or simple replay attacks.
Active liveness detection is commonly associated with:
- Guided user prompts that require real-time response
- Verification flows where higher fraud risk is expected
- Scenarios where strong proof of presence outweighs speed
This type of liveness detection is effective against basic spoofing attempts, but it introduces more user friction. Some users may fail challenges due to accessibility limitations, device issues, or misunderstanding instructions, which can increase drop-offs.
2. Passive Liveness Detection
Passive liveness detection works without requiring explicit user actions. Instead, it analyzes visual and contextual signals from a short capture to determine whether the input represents a live person or a spoof.
Passive liveness detection is typically used when:
- High-volume onboarding requires minimal friction
- User experience and completion rates are a priority
- Verification must run quickly across diverse devices
This approach reduces user effort and improves flow completion, but it relies heavily on model accuracy and capture quality. A well-designed framework usually pairs passive liveness with quality checks and fallback logic to manage uncertainty.
3. Hybrid Liveness Detection
Hybrid liveness detection combines passive and active methods within a single framework. It starts with passive checks and introduces light interaction only when risk signals or uncertainty exceed defined thresholds.
Hybrid liveness detection is useful when:
- Risk varies across users or transactions
- You want to avoid unnecessary friction for low-risk sessions
- Stronger proof of presence is required only in specific cases
This approach allows teams to balance fraud prevention with usability by escalating verification only when needed. It also helps reduce manual reviews by resolving borderline cases through controlled interaction.
Once the main liveness detection types are clear, the next step is understanding how they come together within a liveness detection framework.
How a Liveness Detection Framework Works
A liveness detection framework is the step in your identity verification flow that checks one thing: is a real person present right now, or is this a spoof? In standards language, this sits under Presentation Attack Detection (PAD), which focuses on detecting “presentation attacks” aimed at fooling a biometric system.
To keep results consistent across products, teams, and channels, a framework usually defines what gets captured, what gets checked, how outcomes are decided, and what gets logged for audit and investigation.
.png)
Step 1: Capture quality gating (before liveness even runs)
A detailed framework does not treat every capture as valid. It first checks if the input is usable, because poor capture quality can cause false rejects or false accepts.
Typical quality gates include:
- Face present and centered
- Sufficient lighting and exposure
- Limited blur and motion
- No heavy occlusion across critical face regions
- Stable framing for the required duration
If quality fails, the framework does not “guess.” It either asks for a retake or routes the session to review.
Step 2: Presentation attack detection (PAD) to spot spoof attempts
This is the core of liveness detection. PAD is the automated determination of a presentation attack, as defined in ISO/IEC 30107.
A strong framework checks for signals that commonly appear in spoof media, such as:
- Screen replay patterns, glare, moiré artifacts, or pixel grid cues
- Print artifacts, flatness cues, and unnatural texture behavior
- Mask-like artifacts and inconsistent skin detail
- Synthetic media cues that do not match natural capture behavior
This stage is designed to catch the most common “presentation attack instruments,” which ISO defines as objects used to carry out a presentation attack.
Step 3: Active, passive, or hybrid decisioning
Your framework typically selects one of these liveness modes based on your risk and UX needs.
Passive liveness checks
- The user does not perform explicit actions
- The system analyzes a short capture for natural indicators of a live presence
- Commonly used in high-volume onboarding because it reduces user friction
Active liveness checks
- The user completes prompts designed to prove presence
- Examples include a controlled movement or guided interaction
- Often used when risk is higher or when passive signals look uncertain
Hybrid liveness checks
- Starts with passive checks
- Escalates to a light interaction only when risk signals demand it
- Helps balance completion rates with stronger spoof resistance
A detailed framework makes this choice explicit instead of leaving it to ad-hoc product decisions.
Step 4: Risk scoring and outcome handling
A liveness detection framework rarely uses a single yes/no output in isolation. It usually maps results into outcomes that your ops team can run consistently.
Common outcomes include:
- Pass
- Accept the session and proceed in the verification flow
- Fail
- Block the session if spoof signals are strong
- Inconclusive
- Trigger a retake, add an active step, or route to manual review
This is where many teams reduce operational noise. Instead of sending every imperfect capture to review, the framework defines clear fallback rules.
Step 5: Audit logging and explainability
Because identity verification is high-stakes, the framework defines what evidence gets stored and how you can explain decisions later.
A well-defined logging layer typically includes:
- The final decision and confidence band
- Which checks failed at a category level, such as “capture quality” or “presentation attack indicators”
- Session metadata needed for investigations
- Retake history, if the user needed multiple attempts
This supports internal audits and improves consistency across reviewers.
With the verification process established, the underlying system design shows how liveness detection operates in production environments.
Also read: Deepfake Selfie Verification in Identity Checks
Example Architecture for Cloud-Based Liveness Detection
A liveness detection framework is often implemented using a cloud-native architecture that can validate user presence securely while supporting real-time interaction on user devices. To achieve this balance, many teams adopt a serverless design that separates capture, verification, and storage responsibilities across managed services.
In this type of setup, liveness challenges can be evaluated both on the user’s device and in the cloud. Local execution helps guide the user during capture, while cloud verification ensures consistent decision-making, security controls, and audit readiness.
The architecture typically consists of the following components:
- Client application, which collects images or video frames from the device camera, applies the liveness challenge logic locally, and sends verification data to backend services
- API management layer, which exposes secure endpoints that allow the client to communicate with backend verification services
- Cloud-based execution layer, where verification logic runs in response to client requests and evaluates whether the liveness criteria are satisfied
- Challenge data store, which maintains challenge configurations, session references, and related metadata
- Object storage, which securely holds captured images or frames required for analysis and investigation
- Facial analysis service, which evaluates facial attributes and visual signals to determine whether the captured data reflects live user behavior
- Secrets management service, which protects sensitive credentials and signing keys used during request validation and token generation
Once the system architecture is in place, the next step is understanding the real-world attack methods that a liveness detection framework is designed to identify and block.
Common Attacks a Liveness Framework Should Stop
A liveness detection framework is built to protect identity verification systems from presentation attacks. These attacks attempt to pass off non-live inputs as real users, exploiting gaps in basic document or face-matching checks.
.png)
The most common attack types a liveness framework should stop include:
- Printed photo attacks: In this attack, a fraudster presents a printed photograph of a real person to the camera. While simple, this method can bypass basic face matching systems that only compare facial features. A liveness framework is expected to identify the lack of natural depth, texture variation, and facial movement that indicate a flat, non-live surface.
- Screen replay attacks: Screen replay attacks involve displaying an image or video of a legitimate user on a phone, tablet, or monitor and recording it during verification. These attacks are common in remote onboarding scenarios because they are easy to execute and difficult to detect without dedicated liveness checks. A liveness framework should recognize visual artifacts, reflections, or motion inconsistencies associated with filming a digital display.
- Video replay attacks: In video replay attacks, a pre-recorded video of a real person is used to simulate live behavior. These videos may include natural movements such as blinking or head turns, making them harder to detect than static images. A liveness detection framework must identify timing mismatches, repeated motion patterns, or interaction inconsistencies that indicate the absence of a real-time response.
- 3D mask and prop attacks: This attack uses physical masks, silicone molds, or facial props designed to mimic real facial structure. These attacks are more complex and costly but can target high-value accounts. A liveness framework should detect abnormal surface textures, unnatural facial rigidity, or inconsistencies in depth and facial dynamics that differ from live human skin and muscle movement.
- Synthetic or AI-generated media attacks: Synthetic media attacks rely on AI-generated or manipulated images and videos to imitate a real person’s appearance. As generative tools improve, these attacks have become more realistic and accessible. A liveness detection framework should be able to identify non-natural visual patterns, frame inconsistencies, or signals that suggest the content was generated or altered rather than captured live.
If these attack types are not effectively blocked, they can allow fraudulent users to pass onboarding, increase downstream investigation costs, and weaken compliance and audit confidence.
Once the required IDs and inputs are clear, the next step is understanding how these verification elements are applied within a structured identity verification platform.

How AiPrise Supports Liveness-Based Identity Verification
AiPrise provides a set of identity verification features that incorporate liveness checks within KYC and fraud risk workflows. The following capabilities are directly relevant when implementing liveness-based identity verification.
AiPrise performs liveness-based identity verification by applying specific verification methods within its KYC workflows. These methods are used to confirm user presence, validate identity data, and reduce spoofing risk during remote verification.
AiPrise performs identity verification using the following approaches:
- Liveness Detection: AiPrise uses liveness detection to confirm that a real person is physically present during the verification session, rather than a photo, video, or synthetic representation.
- 1:1 Face Match: AiPrise uses 1:1 face matching to compare a live facial capture against the photo extracted from a government-issued identity document.
- 1:N Face Match: AiPrise uses 1:N face matching to compare a live facial capture against an existing identity database to identify potential duplicates or previously verified identities.
- Government ID Verification: AiPrise uses government-issued identity document verification, including passports, driver’s licenses, and state-issued ID cards, as part of its KYC process.
- Document Authenticity Checks: AiPrise uses document authenticity checks to identify signs of tampering, alteration, or forgery in submitted identity documents.
- Configurable Verification Logic: AiPrise uses configurable verification logic to determine when liveness checks are applied within onboarding and identity verification flows.
- Audit and Review Logs: AiPrise uses audit and review logs to retain verification inputs, outcomes, and review actions for compliance and investigation purposes.
- Global Identity Coverage: AiPrise uses global identity coverage to support identity verification across multiple countries while maintaining consistent verification processes.
These capabilities allow AiPrise to apply liveness detection as part of structured identity verification workflows while maintaining traceability and compliance alignment.
Wrapping Up
A liveness detection framework is a critical component of modern identity verification, helping confirm real user presence and reduce exposure to spoofing, replay, and synthetic identity attacks. By understanding liveness detection types, common attack methods, required inputs, and architectural considerations, you can design verification flows that are more reliable, consistent, and audit-ready.
AiPrise incorporates liveness detection within its KYC and identity verification workflows, alongside document verification and facial matching, to support secure remote onboarding and verification.
Book A Demo to understand how AiPrise applies liveness checks within its verification platform.
FAQs
1. How accurate is liveness detection in real-world onboarding?
Liveness detection accuracy depends on capture quality, attack sophistication, and how it is combined with other verification checks. In real-world onboarding, accuracy improves when liveness detection is used alongside document verification, face matching, and quality controls rather than as a standalone check.
2. What causes liveness detection to fail for genuine users?
Liveness detection can fail for genuine users due to poor lighting, low camera quality, unstable internet connections, or accessibility limitations. These failures are why many frameworks include retakes, fallback checks, or manual review paths to reduce false rejections.
3. Is passive liveness detection enough to stop fraud?
Passive liveness detection can stop many basic spoofing attempts, especially in high-volume onboarding. However, for higher-risk scenarios, teams often combine passive liveness with additional checks or step-up verification to handle more advanced replay or synthetic media attacks.
4. Where should liveness detection sit in a KYC verification flow?
Liveness detection is commonly placed after identity document capture and before final face matching decisions. This placement helps ensure that the person presenting the document is physically present at the time of verification, reducing impersonation risk early in the flow.
5. How do teams review and audit failed liveness checks?
Failed liveness checks are typically reviewed using stored verification data, such as capture quality indicators, decision outcomes, and session context. Clear logging and structured results make it easier for review teams to understand why a session failed and support compliance audits.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.













.png)





.png)













.png)

.png)
.png)









