10 min read
November 25, 2025
Online Banking Frauds Exposed With Proven Prevention Tips

Key Takeaways










Imagine logging into your bank account only to find thousands missing, an all-too-common reality in today’s digital landscape. Online banking frauds cost consumers over $12.5 billion in 2024, a staggering 25% jump from the previous year.
For businesses, the fallout extends far beyond financial loss, damaged trust, customer churn, and long-term reputational harm; it is just the beginning. In this blog, you’ll find the latest tactics fraudsters use, explore real-world prevention strategies, and learn how to safeguard your money and business from digital deception.
Key Takeaways
- Online banking fraud is accelerating, fueled by real-time payments, AI-driven deception, and credential reuse, making detection windows shorter than ever.
- Fraud follows a predictable workflow: reconnaissance → credential theft → session hijack → cash-out. Intercepting any single stage can stop full-scale loss.
- Human behavior remains the weakest link; urgency, fear, and overtrust enable APP scams more than technical flaws.
- Prevention must be layered and adaptive, combine device fingerprinting, behavioral biometrics, and risk-based MFA for true real-time protection.
- AiPrise unifies KYC, fraud detection, and payment intelligence, enabling businesses to cut ATO and APP losses without adding friction for legitimate users.
What Is Online Banking Fraud?
Online banking fraud refers to any unauthorized access, manipulation, or deception through digital banking platforms—whether web portals, mobile apps, or APIs, used to steal funds, harvest data, or impersonate account holders.
It’s not limited to stolen passwords; today’s attackers combine social engineering, malware, and payment manipulation to exploit both human and system weaknesses.
However, don’t confuse it with card fraud. In comparison, card fraud targets your payment instrument (like credit or debit cards), and online banking fraud attacks the account itself, often leveraging your authorization. This makes recovery harder since transactions may appear “approved” by the account holder.
Suggested Read: Common Types of Business and Financial Fraud
You now understand what online banking fraud is and how it operates. But to protect your business effectively, you must first understand the scale and direction of the threat.
The Current Landscape of Online Banking Frauds
Online banking fraud has reached record levels worldwide, fueled by instant payment systems, AI-powered scams, and human error. Let’s examine the numbers, patterns, and trends that define this modern financial battlefield.
Fraud is no longer an isolated issue; it’s a global crisis with measurable economic damage. Such as:
- U.S. consumers lost over $12.5 billion to fraud in 2024, marking a 25% year-over-year increase, according to the Federal Trade Commission.
- The FBI’s Internet Crime Complaint Center (IC3) reported total internet-crime losses exceeding $16 billion in 2024, even as the number of reports slightly declined, signaling fewer but more severe attacks.
- In the UK, it recorded £1.2 billion in total fraud losses in 2023, with Authorized Push Payment (APP) scams alone accounting for £450 million in 2024.

Now that you know how and why fraud happens, it’s time to examine the specific schemes you’ll face and how they break down in detail.
Common Types of Online Banking Frauds
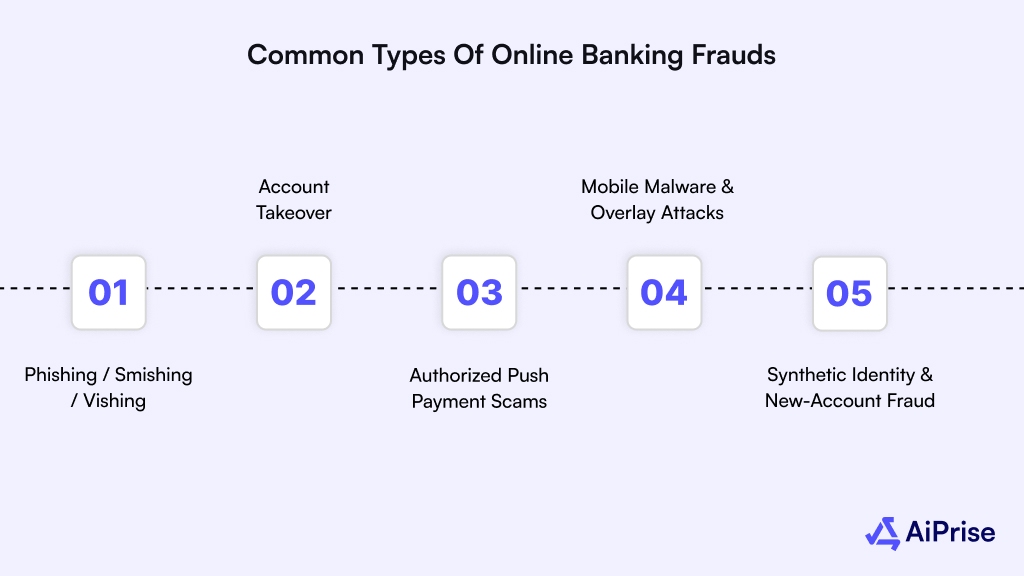
Here’s a targeted overview of the most prevalent fraud methods, followed by highly-specific breakdowns you can use to spot and defend against them.
Phishing / Smishing / Vishing
Phishing (email), smishing (SMS), and vishing (voice calls) remain the most common gateways for online banking fraud. Criminals impersonate legitimate banks, payment providers, or regulators to deceive you into revealing login credentials, OTPs, or personal details.
These attacks are becoming harder to spot, often using AI-generated messages and cloned brand assets.
Key indicators:
- Unexpected message claiming “account locked" or "suspicious login”, urging urgent action.
- The link directs you to a domain resembling your bank but slightly altered.
- Messages that create urgency, such as “Act now or your account will be frozen.”
- URLs with slight spelling variations, added characters, or shortened links.
- Call uses a spoofed bank number and requests you share OTP or approve a session.
- SMS messages that redirect to non-secure domains (HTTP instead of HTTPS).
Account Takeover (ATO)
Account Takeover (ATO) occurs when cybercriminals gain unauthorized access to a user’s online banking account using stolen credentials, malware, or bot-driven attacks. Once inside, they move money, change credentials, and sometimes lock out the rightful owner.
Spotting early signs of ATO can prevent irreversible losses:
- Logins from unrecognized devices or geolocations (especially foreign IPs).
- Unusual activity sequences, such as password resets followed immediately by high-value transfers.
- Rapid creation of new beneficiaries or payees who have never used it before.
- Disabled notifications or changes in communication preferences within the account.
Authorized Push Payment (APP) Scams
In Authorized Push Payment (APP) scams, victims are manipulated into willingly transferring funds to fraudulent accounts. The twist? The payment appears legitimate because you authorize it yourself, making reimbursement complex and often disputed.
Be alert for the subtle clues that signal an APP scam in motion:
- Unexpected payment requests claiming urgency or confidentiality.
- Invoice or payee detail changes sent by a “supplier” or “colleague.”
- Pressure to bypass standard approval processes or use a different payment channel.
- Bank calls or emails urging you to move funds for “security reasons.”
Mobile Malware & Overlay Attacks
Mobile malware and overlay attacks are among the fastest-growing forms of online banking fraud. Here, fraudsters infect smartphones with malicious apps or hidden overlays that capture banking credentials, intercept OTPs, and hijack live sessions without your knowledge.
Recognizing these early signs can prevent deep device compromise:
- Apps requesting unusual permissions like screen overlays, SMS access, or device administrator control.
- Banking apps or payment portals prompting you for login credentials outside official channels.
- Rapid battery drain or high data usage often signals background malware activity.
- Missing SMS messages or unexpected session terminations while using banking apps.
Synthetic Identity & New-Account Fraud
Synthetic identity fraud is one of the most complex and rapidly growing threats in digital banking. Fraudsters combine real personal data (like Social Security numbers or phone numbers) with fabricated information to create entirely new, believable identities that pass initial verification.
Spotting synthetic identities early requires monitoring subtle inconsistencies:
- Mismatched identity elements, such as addresses or contact details that don’t align with credit or utility databases.
- Multiple new accounts linked to the same device, IP address, or email pattern.
- High volume of failed onboarding attempts from similar data points before one succeeds.
- Unusual customer profiles showing no history but immediate financial activity post-approval.
With AiPrise’s Fraud and Risk Scoring solution, you can instantly detect synthetic identities by analyzing cross-device signals, behavioral patterns, and non-bureau data, flagging hidden risks before onboarding completes.
You’ve now seen the many forms of digital deception, but the real power lies in understanding how each attack unfolds from start to finish. This section dissects every stage of a fraud operation so you can identify and disrupt attacks before the money moves.
Attack Mechanisms and Workflows in Online Banking Frauds
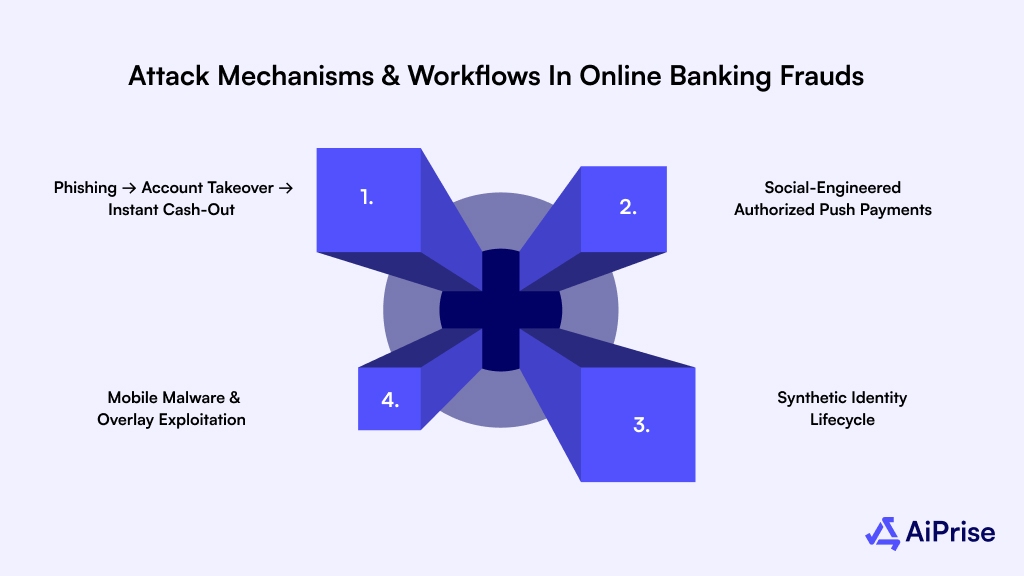
Online banking fraud doesn't occur randomly. They follow structured attack workflows, where criminals progress through predictable, measurable stages, from initial targeting to laundering. Recognizing these stages allows you to build controls that intercept fraud at the earliest possible point.
Attack Path 1: Phishing → Account Takeover → Instant Cash-Out
This is the most common and damaging sequence across global banks.
- The victim receives a phishing email or call mimicking their bank.
- Credentials and OTPs are captured, allowing attackers to log in from new devices.
- Money is transferred to mule accounts within minutes via real-time rails.
Detection Strategy:
- Use FIDO2/WebAuthn-based login to eliminate OTP interception.
- Monitor device ID anomalies and terminate suspicious sessions instantly.
- Implement CoP checks for first-time beneficiaries.
Attack Path 2: Social-Engineered Authorized Push Payments (APP Scams)
APP scams exploit trust and urgency, convincing users to make transfers themselves.
- Victim receives a call or an invoice from a “bank investigator” or a “vendor.”
- Payment is made to a fraudulent account using genuine credentials.
- Funds are immediately dispersed to multiple accounts or crypto wallets.
Detection Strategy:
- Display risk banners for new payees or cross-border transactions.
- Introduce time delays for high-value or first-time payments.
- Enforce dual authorization for business accounts.
Attack Path 3: Mobile Malware & Overlay Exploitation
Fraudsters hijack smartphones to execute invisible transactions.
- The victim downloads a malicious app or sideloads an APK.
- Malware captures credentials, intercepts SMS OTPs, or overlays fake screens.
- The attacker controls the session remotely to initiate payments.
Detection Strategy:
- Block sideloaded APKs and require verified app-store downloads.
- Detect overlay permissions and RAT behavior in real time.
- Replace SMS OTPs with app-based or hardware-based MFA.
Attack Path 4: Synthetic Identity Lifecycle
Synthetic identities operate over months to evade detection.
- A fraudster creates a new persona by blending real and fake credentials.
- Opens low-risk accounts, slowly builds “trust,” then executes a “bust-out.”
- Drains credit lines or channels funds through newly created accounts.
Detection Strategy:
- Use biometric KYC and identity proofing to connect shared devices and data points.
- Flag velocity anomalies in onboarding attempts.
- Link related identities using behavioral and non-bureau data.

Also Read: 17 Tips For Identity Theft Protection And Prevention
You’ve mapped how fraudsters operate. The next step is to understand why their attacks succeed so often, and where both businesses and consumers leave open doors.
Why Businesses and Consumers Are Vulnerable
Online banking fraud succeeds because of three converging weaknesses, human behavior, broken processes, and outdated technology. Each vulnerability on its own seems minor; together, they create systemic exposure.
Human Vulnerabilities
Attackers manipulate psychology, not just systems. Most online banking scams succeed because people respond emotionally before thinking logically. Attackers create urgency, authority, or fear to push victims into quick, unverified actions.
They mimic trusted institutions using spoofed domains, familiar logos, and fake caller IDs, making even cautious users lower their guard.
Fix Fast:
- Adopt number-matching or biometric MFA to prevent blind approvals.
- Send fewer, context-aware alerts that clearly explain what action is being verified.
- Train users to pause before acting, question urgency, verify requests, and confirm sender identity independently.
Process Gaps
Even the strongest security systems fail when internal processes don’t align with fraud controls. Many businesses still prioritize speed and convenience over verification, giving attackers the window they need.
Common gaps include single-approver payments, which make fake vendor or invoice scams easy to execute. Attackers also exploit unverified profile edits, changing phone numbers or 2FA methods right after logging in.
Fix Fast:
- Enforce dual authorization for all first-time or high-value transfers.
- Require step-up verification before approving any contact or MFA change.
- Integrate fraud ops with customer support for instant session termination and account freeze when suspicious activity is reported.
Technical Weaknesses
Outdated authentication and monitoring tools create silent entry points that fraudsters exploit. Reliance on SMS OTPs leaves customers vulnerable to SIM swaps and malware interception.
Attackers also exploit session reuse, logging in with stolen credentials from unrecognized devices that go unchecked.
Fix Fast:
- Replace SMS OTPs with app-based or hardware-based authentication to prevent interception.
- Bind sessions to verified devices and flag anomalies in IP, location, or behavior.
- Implement cooling-off periods for first-time beneficiaries or cross-border transactions to delay fraudulent fund movement.
Also Read: How Banks Utilize Machine Learning For Fraud Detection
You’ve identified where your defenses fail, now it’s time to see how AiPrise turns those vulnerabilities into measurable control points that strengthen your fraud prevention framework.
How AiPrise Helps You Prevent Online Banking Frauds Effectively

AiPrise unifies identity verification, behavioral intelligence, and transaction risk scoring into a single orchestration layer. This allows you to stop Account Takeover (ATO), Authorized Push Payment (APP), and synthetic identity fraud in real time, without adding unnecessary friction for legitimate users.
By using AiPrise, you gain:
- Fraud & Risk Scoring: Use 100+ data sources, including email, phone, device, documents, credit, and judicial records, to assess risk during onboarding and beyond.
- Device & Session Intelligence: Track device fingerprints and browser anomalies, detect remote access tools (RATs), and automatically kill risky sessions.
- Behavioral Analytics: Monitor keystroke patterns, navigation speed, and mouse dynamics to flag atypical user behavior in real time.
- Transaction Risk Controls: Support Confirmation of Payee (CoP), beneficiary reputation screening, velocity limits, and cooling-off timers for high-risk transfers.
- Flexible Rule Engine: Customize risk scoring rules and automation workflows that reflect your internal risk-tolerance and regulatory obligations.
AiPrise gives you visibility, control, and adaptability, everything traditional fraud stacks lack. It helps you prevent fraud before it hits your ledger, without slowing down trusted users.
Book a Demo to see how AiPrise can strengthen your fraud defenses end-to-end.
Summing Up,
Online banking fraud is no longer a distant threat; it’s a daily, evolving risk driven by instant payments, AI-powered deception, and human vulnerability. The key to staying ahead isn’t adding more tools; it’s building an integrated defense that connects identity verification, behavioral analytics, and transaction monitoring in real time.
By understanding each fraud type, tightening your controls, and applying risk-based friction intelligently, you can safeguard both customer trust and business continuity.
Stay proactive, not reactive, and strengthen your fraud defenses before the next attack hits.
Talk to us today to see how unified, intelligent fraud prevention can protect your business end-to-end.
FAQs
1. What is the most common entry point for online banking fraud today?
Phishing and smishing remain the top entry vectors, with attackers using AI-generated messages and spoofed domains to harvest credentials or MFA tokens before takeover attempts.
2. How do fraudsters use AI in banking scams?
Fraudsters deploy AI to craft realistic phishing content, clone voices for vishing calls, and automate credential-stuffing bots that mimic human login behavior across banking platforms.
3. Can real-time payments be made safer without slowing transactions?
Yes, using Confirmation of Payee (CoP), beneficiary risk scoring, and short cooling-off windows prevents most APP scams while keeping transfers nearly instant.
4. Why are small businesses more at risk than large banks?
They often lack dual-authorization controls and fraud-detection infrastructure, making them prime targets for invoice scams and social-engineered transfers.
5. How can consumers quickly verify a genuine bank communication?
Always contact the bank through official numbers listed on their website or app, never via links or phone numbers shared in emails, texts, or unsolicited calls.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.













.png)






.png)












.png)

.png)
.png)









