AiPrise
10 min read
September 23, 2025
Two-Step Verification for Social Accounts: A Complete Guide

Key Takeaways










According to recent data, over 65.7% of the world's population actively uses social media platforms. Your social media accounts contain valuable professional connections, business communications, and reputation-critical content. One compromised password can give attackers access to everything you've built across these platforms.
Two-step verification acts as a digital security checkpoint for your accounts. Even if someone gets your password, they still can't get in without your second form of authentication. This security layer stops most account takeover attempts before they succeed.
In this guide, we break down exactly how two-step verification protects your social networking accounts, why you need it, and how to implement it properly.
Key Takeaways:
- Two-step verification blocks automated attacks by requiring a second authentication factor beyond passwords.
- The two-step verification setup process takes only a few minutes on most major social media platforms.
- Multiple authentication methods are available, including SMS codes, authenticator apps, hardware tokens, and biometric verification.
- Recovery codes prevent lockouts when your primary authentication device isn't available.
- Regular security audits ensure continued protection as threats evolve and platforms update their features.
What Is Two-Step Verification?
Two-step verification is a security process that requires two different forms of authentication to access your account. The first step requires your password, and the second step involves your phone.
This security method works on a simple principle: even if cybercriminals steal your password through phishing emails, data breaches, or brute force attacks, they still can't access your account without your second authentication factor.
For example, if someone gets your password but doesn't have access to your registered phone, they can't complete the login process.
Social media accounts face constant security threats. Learning how two-step verification provides that crucial second security layer helps you make informed decisions about protecting your digital presence.
How Does Two-Step Verification Work?
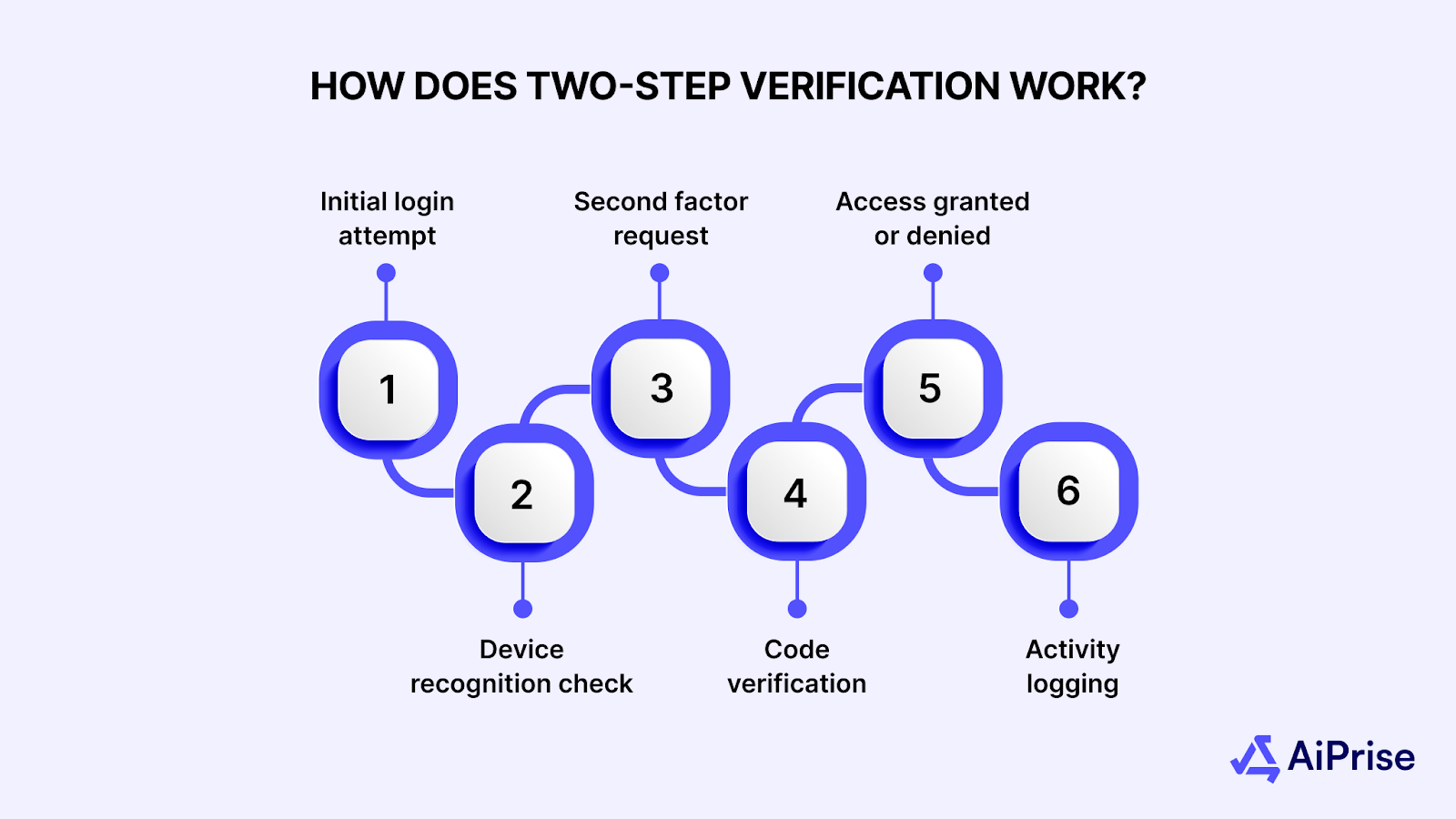
Two-step verification creates multiple security checkpoints that attackers must overcome to access your accounts. The process activates when you attempt to log into your social media account from an unrecognized device or location.
Here's how the verification process protects your accounts:
- Initial login attempt: You enter your username and password as usual, which triggers the platform's security system to evaluate the login request.
- Device recognition check: The system determines whether the login attempt comes from a trusted device or a new location, then decides if additional verification is required.
- Second factor request: The platform sends a verification request to your registered device or authentication method, such as a six-digit code via SMS or a push notification to your authenticator app.
- Code verification: You must enter the correct verification code within the time limit to gain access, typically within 2-5 minutes before the code expires.
- Access granted or denied: The system grants access only after successful completion of both authentication steps. Otherwise, the login attempt fails completely.
- Activity logging: The platform records all verification attempts, creating an audit trail that helps you monitor who tried to access your account and when.
The verification system also sends notifications about failed login attempts, helping you identify potential security threats before they succeed. This real-time monitoring gives you immediate visibility into account security events.
Let’s take a look at the top advantages of two-step verification for your social networking accounts.
What Are the Benefits of Two-Step Verification for Social Media?
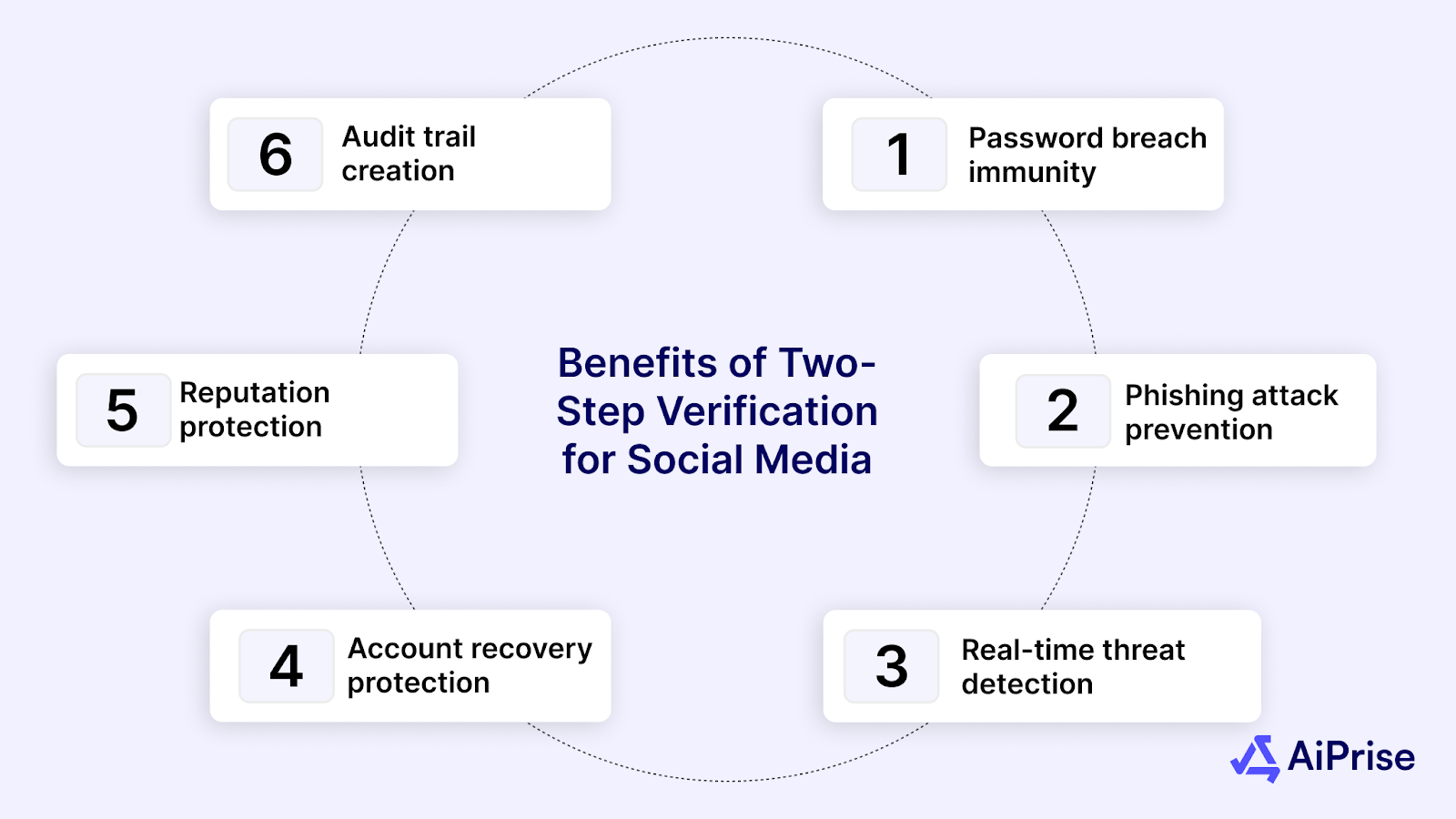
Two-step verification provides multiple layers of protection that work together to secure your social networking accounts against various cyber threats. Here are the key benefits you gain from implementing two-step verification:
- Password breach immunity: When major websites get hacked and passwords are stolen, your accounts remain secure because attackers still need your second authentication factor.
- Phishing attack prevention: Even if you accidentally enter your password on fraudulent sites, attackers can't complete the login process without your authentication device.
- Real-time threat detection: Receive instant notifications when someone tries to access accounts from unfamiliar locations, allowing you to respond before damage occurs.
- Account recovery protection: Hackers can't reset your social media passwords through compromised email accounts because they still need your verification device.
- Professional reputation safeguarding: Prevent unauthorized posts or messages that could damage your professional standing or business relationships.
- Audit trail creation: Maintain detailed logs of all login attempts and verification activities for security analysis and compliance purposes.
These benefits cover the main protection you get, but choosing the right two-step verification method makes all the difference in how well your security actually works.
Types of Two-Step Verification Methods
Different verification methods offer varying levels of security and convenience. Choosing the right approach depends on your security requirements and daily workflow needs.
Here's how the main verification methods compare:
Let’s look at these common verification methods in detail:
- SMS text message verification: It sends codes directly to your mobile phone. This method is widely available and easy to use, making it popular for most accounts. However, SMS can be vulnerable to SIM swapping attacks, where cybercriminals transfer your phone number to their device.
- Authenticator apps: Apps like Google Authenticator or Microsoft Authenticator generate time-based codes on your smartphone. These apps work offline and provide better security than SMS because they're tied to your specific device rather than your phone number. Most social media platforms support major authenticator apps.
- Hardware security keys: They offer the highest level of protection by requiring a physical device to complete authentication. These USB or Bluetooth devices must be present during login attempts. While more secure, hardware keys require careful management and may be inconvenient for daily use.
- Push notifications: They send approval requests directly to your registered device. You can approve or deny login attempts with a single tap. This method is user-friendly and secure, but requires an internet connection on your verification device.
- Biometric verification: This method uses fingerprints, facial recognition, or voice patterns for authentication. Many mobile apps now support biometric verification as a second factor. This method is convenient and secure, but requires compatible devices.
- Backup codes: These serve as emergency authentication methods when your primary verification isn't available. Social media platforms typically provide 8-10 single-use codes that should be stored securely offline. These codes ensure account access even if you lose your phone or authentication device.
Each method has trade-offs between security and convenience. Using multiple verification methods for critical accounts provides the best protection.
Now, let’s see how you can set up the two-step verification for your social networking accounts.
How to Enable Two-Step Verification?
Setting up two-step verification follows similar patterns across different social media platforms. Most accounts can implement this security measure quickly using these standard steps.
The setup process requires access to both your social media account and your chosen verification device. Here's how to enable two-step verification:
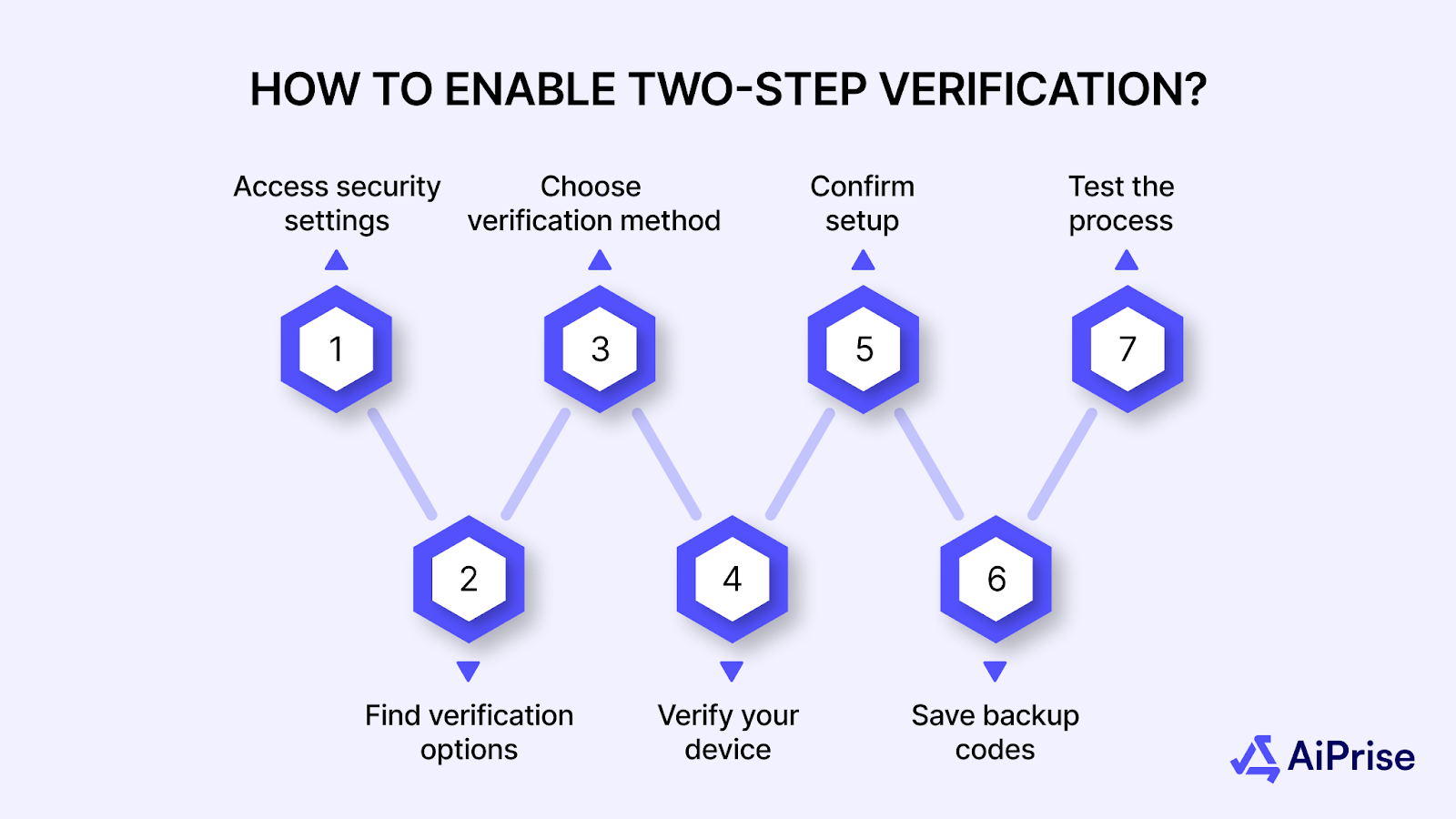
- Access security settings: Log into your social media account and locate the security or privacy settings section, typically found in account settings or profile menus.
- Find verification options: Look for "Two-factor authentication," "Two-step verification," or "Login verification" in the security settings menu.
- Choose verification method: Select your preferred authentication method from available options such as SMS, authenticator app, or hardware key.
- Verify your device: Enter your phone number for SMS codes or scan QR codes for authenticator apps to link your verification device to the account.
- Confirm setup: Complete a test verification by entering a code or confirming a push notification to ensure the system works correctly.
- Save backup codes: Download and securely store backup recovery codes provided by the platform for emergency account access.
- Test the process: Log out and back in from a new device to confirm that two-step verification activates properly and you can complete the authentication process.
Most platforms require you to confirm your phone number or email address before enabling two-step verification. Keep your contact information updated to ensure verification messages reach you reliably.
But setting up verification is just the first step. There are some challenges you need to know, so that you can solve them easily.
Common Challenges and How to Overcome Them
Two-step verification also has some obstacles. Here are some of the common challenges you might face and effective solutions for each:
- Lost or broken devices: Set up multiple verification methods during initial setup and store backup codes in secure locations separate from your primary device to maintain account access.
- Changed phone numbers: Update verification settings immediately before switching phone numbers, and keep platform support contact information ready with identity verification documents for emergency recovery.
- App reinstallation issues: Back up authenticator app settings and document backup codes when first setting up verification to prevent lockouts during device changes.
- Travel complications: Use authenticator apps as primary verification since they work globally without cellular network dependency, and prepare backup codes when traveling internationally.
- Unreliable SMS delivery: Switch to app-based verification as your primary method if SMS delivery is inconsistent in your location or region.
- Account management complexity: Establish clear verification procedures with secure backup code storage and recovery processes to maintain access across all your accounts.
Knowing these challenges helps you maintain your social media account security. But using verification correctly and following some best practices from day one prevents most problems before they start.
Two-Step Verification Best Practices for Maximum Protection
To implement two-step verification effectively, it is important to follow proper security measures that maximize protection while maintaining account usability. Here are some of the best practices you need to know:
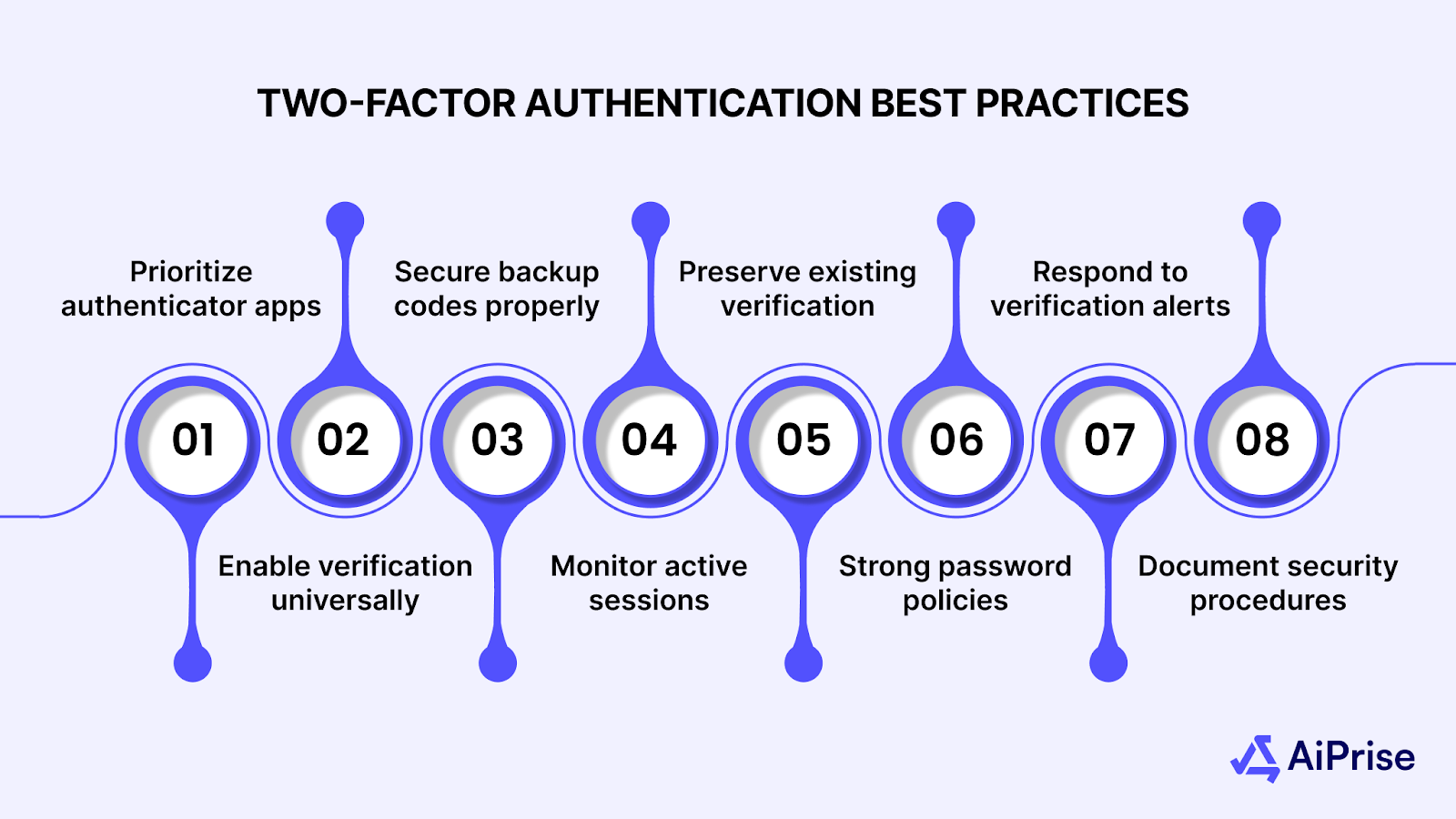
- Prioritize authenticator apps: Use authenticator apps over SMS whenever possible since apps provide better security by generating codes locally on your device rather than sending them through cellular networks.
- Enable verification universally: Activate verification on all your social media accounts, not just the most important ones, since attackers often target lesser accounts to gather information for attacking primary accounts.
- Secure backup codes properly: Store backup codes offline in multiple secure locations, such as with trusted contacts, or in a password manager separate from your devices.
- Monitor active sessions: Review active sessions regularly to identify unauthorized access attempts, and log out suspicious sessions immediately while changing passwords if needed.
- Maintain current verification methods: Keep verification information updated when you change phones, phone numbers, or email addresses to prevent account lockouts during security emergencies.
- Implement strong password policies: Use unique, strong passwords in combination with two-step verification, since weak passwords make accounts easier targets even with verification enabled.
- Respond to verification alerts: Monitor verification notifications closely for any codes you didn't request, as unsolicited verification codes often indicate someone is attempting to access your accounts.
- Document security procedures: Create clear records for verification management, including backup code access procedures and emergency account recovery processes.
Following these practices creates multiple security layers that work together to protect your social media presence comprehensively.
Regular security reviews ensure all verification methods remain current and effective. Fraud detection and prevention become more effective when combined with proper authentication technology.
Secure Your Digital Infrastructure with AiPrise
Two-step verification provides strong protection for individual social media accounts, but modern companies in regulated industries require automated, enterprise-grade verification solutions that protect against advanced threats while meeting strict compliance standards.
AiPrise delivers advanced verification technology that goes beyond basic two-step authentication. Here’s how AiPrise can help you ensure complete security and compliance for your organization:
- User Verification: Complete identity validation with document verification, face liveness checks, and AML screening to ensure only legitimate users access your systems.
- Fraud & Risk Scoring: Advanced AI algorithms analyze user behavior patterns and device insights to detect suspicious activities before they compromise your platforms.
- Government Verifications: Cross-check user information against official government databases from 100+ sources globally for enhanced identity confidence and regulatory compliance.
- Watchlist Screening: Automated screening against 5000+ global sanction lists and PEP databases to identify high-risk individuals and prevent financial crimes.
- Case Management: Centralized platform to track, escalate, and manage verification cases with complete audit trails for compliance reporting and risk oversight.
With AiPrise, you can build customer trust while protecting against emerging financial and regulatory violations.
Final Thoughts
Two-step verification is your first line of protection against social media account takeovers. But it's just the beginning of comprehensive digital security for professionals in regulated industries.
While this basic protection stops most common attacks, financial institutions and payment providers face sophisticated threats that require advanced verification solutions.
The investment in proper verification prevents breaches, maintains professional reputation, and ensures regulatory compliance. As cyber threats continue evolving and regulations become stricter, staying ahead requires both foundational security practices and enterprise-grade verification technology.
AiPrise provides the advanced verification solutions that businesses need to protect their digital infrastructure comprehensively while meeting regulatory requirements.
Book A Demo today to see how our verification platform can secure your business while meeting your compliance needs.
FAQs
1. Does two-step verification significantly slow down the login process?
The additional step adds 10-15 seconds to login time, but authenticator apps and push notifications make the process faster than waiting for SMS codes while providing much better security.
2. Should I use different verification methods for different accounts?
Using varied methods for different accounts provides better security coverage. If one method is compromised or unavailable, your other accounts remain protected and accessible.
3. Can employers require two-step verification on work-related social accounts?
Yes, most social media platforms support policies that require two-step verification. This is considered a reasonable security requirement for professional accounts, and it is often required for compliance.
4. What's the difference between two-step and multi-factor authentication?
Two-step refers to any two authentication steps, while multi-factor specifically requires different factor types (knowledge, possession, inherence). Multi-factor provides stronger security for high-risk profiles.
5. How often should I review and update my verification security settings?
Review verification settings quarterly and update immediately when changing devices, phone numbers, or when new security threats emerge. Regular audits ensure your protection remains effective against current threats.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.










.png)







.png)






.png)

















.png)

.png)
.png)











