AiPrise
9 min read
September 19, 2025
Strategies to Detect Forged Identification Documents
Key Takeaways










Forgery of identification documents is a serious issue across various sectors, from banking and finance to hospitality and retail. Fraudulent identification documents, whether used for accessing age-restricted venues, committing financial crimes, or impersonating others, pose significant risks to businesses and individuals alike.
This blog explores various strategies and technologies for detecting forged identification documents, from manual checks to advanced biometric and digital solutions, ensuring that you can protect your organization against identity fraud.
Quick Glance:
- Forged IDs pose significant security risks across various industries.
- There are several types of document forgery, including complete, alteration, and counterfeit forgeries.
- KYC (Know Your Customer) and KYB (Know Your Business) procedures help verify authenticity and reduce fraud.
- Checking security features such as holograms, microprinting, and UV-reactive inks is essential for detecting fake IDs.
- Technological tools like UV light, magnifiers, and fraud detection software provide effective methods for verification.
- Advanced solutions like biometric verification, QR codes, and blockchain technology further enhance identity checks.
Understanding Identity Document Forgery
Forgery refers to the act of creating, altering, or using fake identification documents to deceive others. This fraudulent practice allows individuals to impersonate someone else or falsify their identity for malicious purposes, such as gaining unauthorized access to services, financial resources, or government benefits.
Types of Forgery
Complete Forgery
This type of forgery involves creating a fake document from scratch, mimicking the format, features, and information of a genuine document. These documents may look convincing but fail to meet legal and security standards.
Alteration Forgery
Alteration forgery occurs when a genuine document is tampered with to change personal details, such as names, dates of birth, or photos, to suit the forger's needs. This is often harder to detect but still poses a significant risk.
Counterfeit Documents
Counterfeit documents are fraudulent replicas of original documents, such as fake passports or driver’s licenses, created using high-quality materials and methods.
Understanding the different types of forgery alone is not enough. It is time to dig deeper into the details.
Recognizing Different Types of Forged Documents
It is important to understand the various types of documents that are commonly forged, as each one presents its own set of challenges and risks.
Government-Issued IDs
Passports, National ID Cards, and Driving Licenses: These are the most commonly forged documents. Counterfeit versions often attempt to replicate state-issued features such as holograms, barcodes, and UV-reactive inks. A close inspection of security features and comparison with known genuine IDs is critical.
Educational Certificates
Fake Diplomas or Degrees: Educational institutions have been targets of counterfeiters attempting to gain credibility or access to employment. These forged documents may include altered dates, signatures, or institutional logos.
Financial Documents
Forged Bank Statements and Tax Documents: Fake financial documents are used to mislead institutions or authorities during loan applications, tax filings, or background checks. These forgeries often fail basic authenticity tests, such as bank logos, formatting consistency, and correct document stamps.
You have learned about the various types of forged documents. How about identifying them in the first place?
How to Identify Forged Documents
Identifying forged documents requires a systematic approach involving both traditional verification methods and advanced technologies. Here are key steps and techniques that businesses and institutions can use to detect counterfeit documents:
Verification Using KYC and KYB Procedures
Know Your Customer (KYC) and Know Your Business (KYB) procedures are essential tools for verifying the authenticity of identity documents. These procedures help businesses comply with regulatory requirements and safeguard them against fraud.
KYC Procedures for Individual Verification
KYC involves gathering personal information such as name, date of birth, and address, then verifying these details against trusted data sources, such as government databases or financial institutions. This helps ensure the individual presenting the ID is legitimate.
KYB Procedures for Business Verification
While KYC focuses on individuals, KYB checks are designed to verify the authenticity of business entities. This involves checking business registration records, corporate structure, and key personnel to confirm the legitimacy of the company. For businesses, additional steps may include validating tax documents and financial statements.
Both processes involve examining identification documents and cross-referencing the data with government-issued databases or other trusted sources to ensure the information is valid and consistent. For high-risk or high-value transactions, both KYC and KYB procedures are essential to prevent identity fraud and business-related crimes.
Confirming the Authenticity of IDs
Confirming the authenticity of an ID goes beyond just inspecting the visible features. It requires a multi-layered approach that includes checking the physical properties, security features, and overall quality of the document. Here’s how to confirm whether an ID is genuine:
Paper Quality and Watermarks
Genuine IDs are printed on high-quality materials that feel sturdy and resilient. The paper often contains embedded security fibers or watermarks that are difficult to replicate. When held up to light, you might see a watermark that is only visible in specific conditions. Forged IDs, on the other hand, tend to use cheaper paper, often resulting in a flimsy feel and the absence of a watermark or a poorly reproduced one.
How to Test: Hold the document up to light to look for watermarks or security threads. Run your fingers over the surface to feel for any embedded fibers that may not be present in fake IDs.
Security Features
Authentic documents are equipped with advanced security features that are often challenging to copy. These may include:
- Holograms: Genuine IDs often incorporate holographic images that shift in color when tilted.
- Microprinting: Tiny text or patterns that are difficult to reproduce without high-end equipment.
- UV-Reactive Inks: Certain details are visible only under UV light, such as the state logo or specific numbers.
Forged documents may either lack these features entirely or have low-quality reproductions that fail to match the standard of genuine IDs.
How to Test: Use UV light to inspect UV-reactive inks. Tilt the ID under a light to check holograms, and use a magnifying lens to check for microprinting.
Alignment and Wear and Tear
Genuine IDs are printed with precision, ensuring that all elements (text, photos, and security features) are aligned perfectly. Any signs of misalignment or distortion are red flags. Additionally, genuine documents, even after extended use, don’t show significant wear on the photo or text. Counterfeit documents may exhibit:
- Poorly aligned text or images: Elements may appear shifted or out of place.
- Visible wear and tear: The laminate may begin to peel, the photo may show signs of tampering, or the text may become faded from repeated alterations.
How to Test: Hold the ID at different angles to check for uneven printing. Inspect the edges of the card for signs of tampering, peeling, or excessive wear.
Having understood the physical aspects of document verification, let’s now look at the technology that can significantly aid in identifying forged IDs.
Implementing Technology for Improved Detection
As counterfeiters become more sophisticated, businesses must adopt cutting-edge technologies to stay ahead in the fight against forged identification documents. From biometric verification to blockchain and RFID chips, technology offers a powerful toolkit for improving identity verification. Below are some key technological advancements that can significantly enhance document detection and security:
Biometric Verification
- Fingerprint and Facial Recognition: Biometric verification provides a higher level of security by using unique physical traits to verify identity. Fingerprint or facial recognition can compare the data on the document with a live scan of the individual to ensure they match.
Blockchain Technology
- Immutable Document Records: Blockchain technology is being used to store and verify identity information in an immutable ledger. This provides a secure, transparent, and tamper-proof method for verifying identity documents, reducing the chances of forgery.
Digital Seals and RFID Chip Verification
- Digital Seals: Many modern IDs now contain digital seals or certificates that can be verified using a scanner or mobile app. These seals add an additional layer of security and make it nearly impossible to replicate.
- RFID Chips: Some documents now contain embedded RFID (Radio Frequency Identification) chips, which store information that can be quickly scanned and verified through electronic readers.
Fraud Detection Software
Fraud detection software plays a critical role in modern identity verification systems, offering enhanced security and the ability to detect fraudulent activities efficiently. Below are two key functions that help businesses protect themselves from fraud during the verification process:
Access to Extensive Databases for Cross-Referencing and Verification
Fraud detection software often integrates with large databases of verified information, such as government records and watchlists, allowing for cross-referencing. This ensures that the information on the document is consistent with global or local databases, helping detect fraudulent identities in real time.
Ensuring System Integrity During Online Verification Sessions
For online verification, fraud detection software ensures system integrity by monitoring for irregular behaviors, such as IP address mismatches, multiple failed verification attempts, or suspicious geographic locations. This allows for immediate action to be taken if fraud is suspected.
How to Enhance Security Measures
With the rise in fraudulent activities and identity theft, businesses must adopt robust security measures to enhance the verification process and prevent the use of fake identities. Below are advanced strategies and technologies that can strengthen security during ID verification:
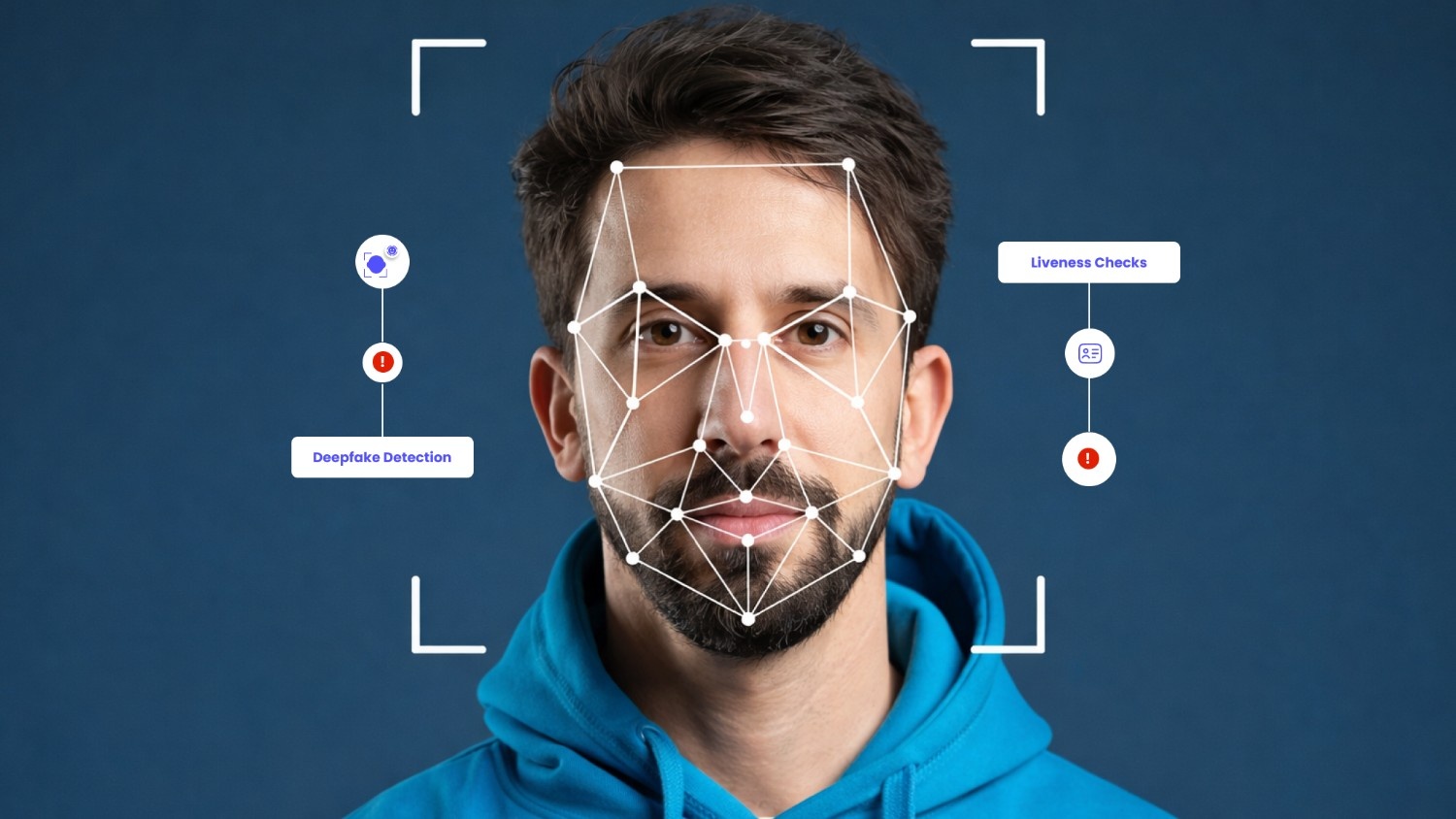
Liveness Checks During Photo Verification
Modern verification systems now use liveness checks, which require individuals to perform a task, such as blinking or turning their head, during the photo verification process. This ensures that the person being verified is present and prevents the use of stolen photos.
Tracking IP Addresses to Detect Suspicious Activities
Monitoring IP addresses during online verification sessions can help identify suspicious activities, such as attempts to use multiple fake identities from the same location or device. By flagging these behaviors, businesses can prevent fraud before it occurs.
AiPrise: Securing Your Business Against Fraud
AiPrise offers cutting-edge solutions for detecting forged identification documents, utilizing state-of-the-art technologies such as AI, machine learning, and biometric verification.
With AiPrise’s KYC, KYB, and AML solutions, businesses can ensure that they are verifying identities in compliance with global regulations while reducing the risks of fraud.
AiPrise’s unique approach integrates advanced tools like digital seals, blockchain-based identity verification, and fraud detection software to offer a comprehensive, secure solution. This allows businesses to verify not just the authenticity of an ID but also confirm the integrity of the individual or organization behind it.
Whether you are in banking, finance, or any sector requiring secure identity verification, AiPrise provides the tools you need to protect your business from fraud.
Conclusion
By carefully applying KYC and KYB procedures, along with thoroughly checking the authenticity of documents through paper quality, security features, and alignment, businesses can better detect forged identification documents. These steps, combined with advanced tools like UV light, magnifiers, and scanners, offer a multi-layered approach to verifying identities and ensuring the integrity of your operations.
Whether you are working in finance, hospitality, or any other industry where identity verification is crucial, understanding these indicators and having the right tools will help you protect your business from fraud and mitigate the risks of accepting forged documents.
AiPrise provides robust solutions for KYC, KYB, and AML verification, helping businesses enhance their identity verification processes. With cutting-edge tools such as biometric authentication, AI-powered fraud detection, and real-time verification systems, AiPrise enables organizations to minimize risks and ensure compliance with global standards.
Explore AiPrise’s identity verification solutions today. Learn how our advanced technology can streamline your process and secure your business from fraudulent activities. Book A Demo
FAQs
What security features can I check to identify a forged ID?
Check for UV-reactive inks, holograms, microprinting, and embedded watermarks. These features are hard to replicate and indicate authenticity.
Can a QR code on an ID verify its authenticity?
Yes, scanning a QR code linked to a verified database can quickly confirm whether the ID is legitimate.
How does biometric verification help detect fake IDs?
Biometric verification compares physical traits like facial features or fingerprints to the data on the ID, ensuring the person presenting it matches the details.
What is the role of IP address tracking in detecting fraud?
IP address monitoring can identify suspicious activity, such as multiple verification attempts from the same location, which may indicate fraud.
Why is liveness detection important in ID verification?
Liveness detection ensures the person is physically present by requiring actions like blinking or moving, preventing the use of stolen photos or videos.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.













.png)






.png)













.png)

.png)
.png)









