AiPrise
12 min read
December 10, 2025
A Complete Guide to Money Laundering Scams in 2026

Key Takeaways










The global scourge of money laundering has escalated into a multi‑trillion‑dollar problem. Recent research estimates that up to $5.5 trillion is laundered worldwide every year, equivalent to roughly 5% of global GDP. Despite increased regulatory scrutiny, criminals continue to exploit complex ownership structures, cross‑border flows, and emerging technologies to hide illicit funds.
For businesses, financial institutions, compliance teams, and regulators, understanding and anticipating laundering schemes is no longer optional. As enforcement tightens and laundering techniques evolve, you need clear knowledge of red flags, compliance failures, and protection strategies.
This guide breaks down the most common money‑laundering scams in 2026, showing how they operate, why they succeed, and how firms can stay ahead.
Key Takeaways
- Money laundering in 2026 is driven by speed, scale, and technology, with AI, real-time payments, crypto, and cross-border platforms enabling criminals to move illicit funds faster than ever before.
- Money mules remain the backbone of modern laundering networks, recruited through fake jobs, romance scams, and crypto offers to move funds through personal accounts, wallets, and payment apps.
- The most common laundering scams today span online banking and e-wallet abuse, crypto and NFT investment fraud, shell companies, trade-based laundering, online gambling platforms, and real estate.
- Advanced laundering techniques now combine AI-generated identities, device spoofing, cross-chain crypto transactions, and layered jurisdiction hopping to evade traditional AML controls.
- Effective prevention requires unified identity verification, behavioral monitoring, transaction risk controls, and real-time scoring to detect mule activity and suspicious fund movement before losses and compliance violations occur.
What is Money Laundering?
Money laundering is the illegal process of making proceeds from crime appear legitimate. Criminals disguise the origins of money obtained through activities like fraud, corruption, insider trading, smuggling, ransomware, and other illicit operations. The goal is to turn “dirty” money into “clean” funds that can be freely used in the legal economy.
The process typically follows three stages, though in practice they often overlap or repeat:
Placement: This is the initial introduction of illicit funds into the financial system. Common methods include:
- Depositing cash into bank accounts or fintech platforms
- Blending criminal proceeds with legitimate business income
- Using money transfer services, prepaid cards, or crypto exchanges
- Cross-border physical cash movements
Layering: Layering involves creating complex transaction chains to obscure the money trail. This stage is designed to make detection by authorities difficult. Techniques include:
- Wire transfers across multiple accounts and jurisdictions
- Converting money into cryptocurrencies or digital assets
- Using shell companies, offshore trusts, or structured finance products
- Over-invoicing, phantom transactions, or trade-based money laundering
Integration: Integration is the stage where laundered money re-enters the economy appearing legal. Common integration methods include:
- Investing in real estate, luxury goods, art, or high-value commodities
- Funding legitimate businesses or startups
- Purchasing financial instruments, equities, or cryptocurrencies
- Using complex invoicing to disguise ownership and transaction value
Money laundering is increasingly facilitated by technology, including online banking, crypto platforms, and decentralized finance (DeFi) networks.
It also involves unwitting participants, known as money mules, who may be recruited via social engineering or phishing scams.
How Money Laundering Impacts the Global Economy
Money laundering remains a significant global issue. According to the United Nations Office on Drugs and Crime (UNODC), it accounts for 2–5% of global GDP, or roughly $800 billion–$2 trillion annually. In the UK, the National Crime Agency estimates that over £100 billion is laundered each year.
Emerging technologies, cross-border digital payments, and crypto adoption have added new layers of complexity, making real-time monitoring and advanced AML systems essential.
While the core stages of placement, layering, and integration remain, criminals now leverage:
- Cryptocurrencies and NFTs to move large sums anonymously
- Decentralized exchanges (DEXs) to bypass traditional financial oversight
- AI-powered fraud tools to automate transaction obfuscation
- Cross-border e-commerce and trade-based laundering
Understanding these methods is critical for regulators, banks, fintech companies, and crypto platforms to prevent illicit funds from entering the financial system.
The Role of Money Mules in Money Laundering
Money mules are now one of the fastest-growing enablers of global money laundering. They are typically recruited through:
- Fake job and work‑from‑home offers
- Romance and investment scams
- Social media payment requests
- Crypto “trading assistant” schemes
In most cases, the money mule is unaware of the criminal nature of their actions: they may be recruited via a fake “work‑from‑home” job, social media offer, romance scam, or online ad that promises easy money for little effort.
Others may be complicit, knowingly helping criminals launder funds, sometimes for regular payouts or a cut of laundered money.
Once the money enters the mule’s account, the mule quickly transfers it onward to other accounts, crypto wallets, prepaid cards, or cash-out services. This helps criminals conceal the original source, making it harder for authorities to trace the money back to illegal activity.
Thus, money mules play a central role in many laundering schemes, acting as human intermediaries that camouflage financial crime behind seemingly legitimate transactions.
Here’s why money mules dramatically amplify money-laundering risk:
- Anonymity and low traceability: By using a third‑party’s account, the real perpetrator remains hidden. Law enforcement sees the mule’s name instead of the criminal’s.
- High volume, low visibility: Mules can be very many, each moving small amounts. Because individual amounts are small, they often don’t trigger alerts, yet cumulatively, they enable large-scale laundering.
- Blending illicit and legitimate funds: When mules are unaware of the crime, their activity may look like normal banking, which reduces suspicion.
- Global reach via digital channels: Crypto, online banking, digital payments, remittances, all make it easier to route money across borders quickly, bypassing older AML controls. Many mule operations now exploit crypto platforms, payment processors, and fintech services.
Because of these factors, mule networks remain a core pillar of modern money‑laundering schemes. Detecting and disrupting them is often one of the earliest ways to block illicit funds from re‑entering the legal economy.
Financial institutions, crypto platforms, and compliance teams can watch for behavior patterns that often indicate mule activity:
- An account repeatedly receives funds from unknown third parties and immediately transfers them out (rapid in‑and‑out flow)
- Multiple deposits from different senders followed by quick withdrawals or crypto conversions
- Access from multiple geographic locations, VPN usage, or device/IP switching
- Frequent small to mid‑sized deposits and withdrawals that don’t match the account’s typical profile
- Hesitancy or refusal to comply with Know‑Your‑Customer (KYC) or identity‑verification requests
- Transfers to or from high‑risk jurisdictions, crypto exchanges, or prepaid/alternative payment systems
Platforms that combine transaction monitoring, behavioral analytics, device/device‑fingerprinting, and network‑graph analysis are often best positioned to identify mule‑driven laundering early and trigger further investigation.
Suggested Read: How to Spot a Fake Identity: A Guide to Combating Synthetic Fraud

AiPrise continuously monitors user behavior and transaction risk across digital workflows with its Fraud and Risk Scoring solution. It identifies patterns linked to mule activity, fraud, and illicit fund movement. This helps businesses take action before laundering schemes mature.
Next, let’s look at some of the common money laundering scams in 2026.
Common Money Laundering Scams to Look Out For
Money laundering schemes are constantly evolving, leveraging technology, global financial networks, and unsuspecting individuals to move illicit funds. While methods can vary widely, several types of scams are particularly prevalent today.
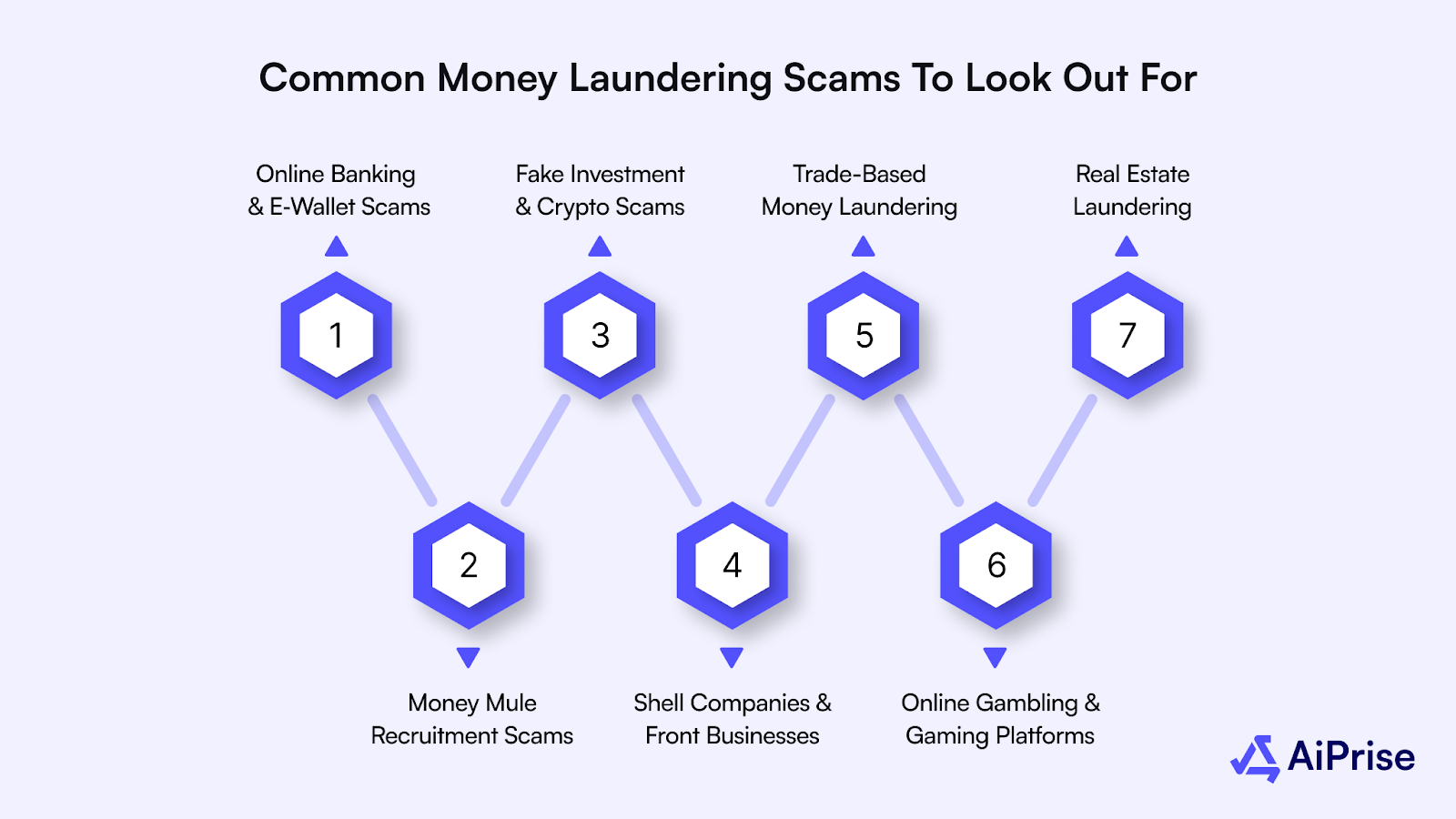
Here are some of them:
Online Banking & E‑Wallet Scams
Fraudsters exploit online banking, mobile payment apps, and digital wallets to receive illicit funds and transfer them quickly. Mules or compromised accounts are often used to layer transactions, making it difficult for authorities to trace the source. Rapid peer-to-peer transfers and cross-border remittances are commonly abused.
Example: Cybercriminals hack or socially engineer accounts to receive stolen funds, which are then quickly dispersed through multiple e-wallets or digital bank accounts.
Money Mule Recruitment Scams
Recruitment scams lure unsuspecting individuals to act as intermediaries, receiving illicit funds and forwarding them. Often advertised as “easy work-from-home jobs,” these scams exploit naivety or financial desperation. Mules may unknowingly facilitate large-scale laundering, exposing themselves to legal liability.
Key red flag: Unsolicited job offers requiring recipients to receive and forward funds.
Fake Investment Schemes & Crypto Scams
Fraudulent investment platforms, Ponzi schemes, or fake crypto exchanges attract deposits from victims. Criminals then move the funds through multiple wallets or shell companies to obscure the trail. These scams are increasingly leveraging decentralized finance (DeFi) platforms to hide identities and cross-border movements.
Emerging trend 2026: Use of tokenized assets or NFTs to move illicit funds under the guise of legitimate investment.
Shell Companies & Front Businesses
Criminals create fake companies to disguise illicit income as legitimate revenue. Money may flow through invoicing, fake contracts, or trade-based schemes, often involving international transactions. This makes it challenging for regulators and banks to distinguish between lawful business operations and laundering.
Example: Over-invoicing or phantom services where a shell company issues inflated invoices to transfer illicit money across borders.
Trade-Based Money Laundering (TBML)
TBML involves manipulating trade transactions to move money. Common tactics include over- or under-invoicing goods, multiple shipments for the same products, or falsifying import/export documentation. This method is often used to integrate illicit funds into legitimate international trade networks.
Note: With globalization and digital trade platforms, TBML is increasingly automated and harder to detect.
Online Gambling & Gaming Platforms
High-volume online gaming and betting platforms are increasingly exploited to launder money. Criminals deposit illicit funds, conduct betting or gaming activity, and cash out “clean” winnings. Sports events or high-traffic e-sports platforms are particularly attractive due to high transaction volumes.
Tip: Regulatory gaps in online gaming and crypto-based betting make this sector a growing laundering vector.
Real Estate Laundering
Investing illicit funds in high-value real estate continues to be a common method of integration. Criminals purchase properties using mules, shell companies, or mixed sources of legitimate and illicit funds. The assets can later be sold or rented, generating a seemingly legal income stream.
Example: Buying luxury apartments or commercial property via a chain of offshore accounts and companies to obscure beneficial ownership.
Emerging Trends in 2026
- Crypto and DeFi laundering: Criminals increasingly use decentralized exchanges, stablecoins, and cross-chain transactions to move funds anonymously.
- AI-assisted scams: Fraudsters use AI-generated identities or synthetic accounts to bypass KYC/AML checks.
- Layered cross-border transactions: Criminals exploit multiple jurisdictions with varying regulatory enforcement to obscure fund origins.
Money laundering scams exploit technology, cross-border systems, and unsuspecting individuals. Awareness of these common schemes is essential for regulators, financial institutions, and crypto platforms to detect, prevent, and report illicit activity.
Also Read: How AI is Transforming AML Compliance
With a clear understanding of money laundering and its impact, let’s look at some useful techniques to tackle money laundering.
Strategies to Counter Money Laundering Scams
Preventing and mitigating money laundering scams requires a proactive, multi-layered approach. Businesses, financial institutions, and crypto platforms must implement strategies that protect operations, customers, and regulatory compliance.
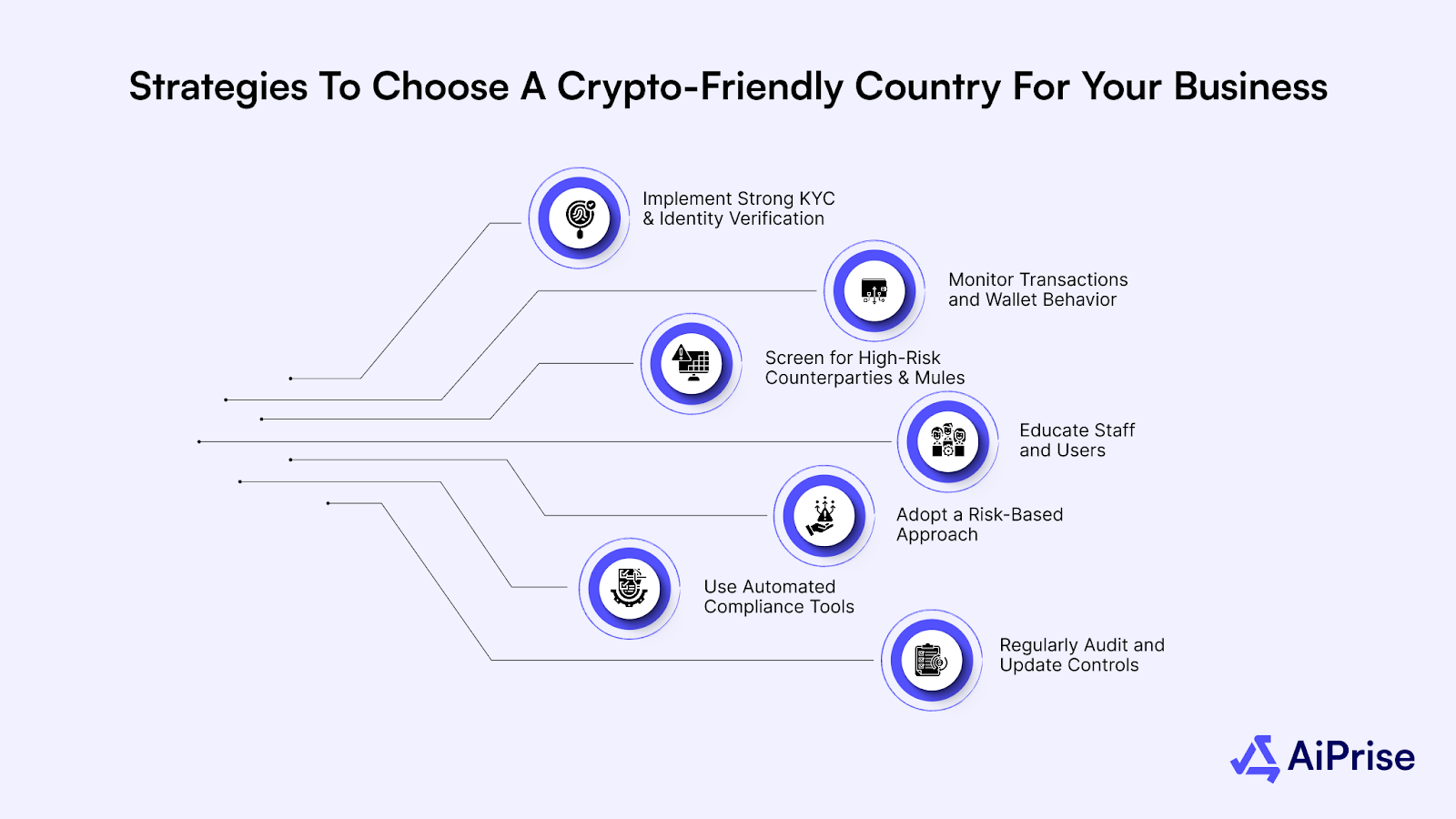
Here are some things to keep in mind:
Implement Strong KYC and Identity Verification
Verify the identities of all clients, counterparties, and entities before onboarding. Use advanced identity verification tools to detect fake, stolen, or synthetic identities. Strong Know Your Customer (KYC) processes reduce the risk of inadvertently facilitating illicit transactions.
Monitor Transactions and Wallet Behavior
Deploy systems to track unusual transaction patterns, rapid fund movements, or high-risk cross-border transfers. Behavioral analytics and real-time monitoring can identify suspicious activity before it escalates.
Screen for High-Risk Counterparties and Mules
Regularly check clients, wallets, and counterparties against sanction lists, watchlists, and known mule networks. Identify and block potentially compromised or illicit intermediaries early.
Educate Staff and Users
Train employees and users on common money laundering scams, red flags, and social engineering tactics. Awareness reduces vulnerability to fraudulent schemes, including mule recruitment and phishing attacks.
Adopt a Risk-Based Approach
Not all transactions carry equal risk. Apply enhanced due diligence for high-value transfers, cross-border activity, or dealings with politically exposed persons (PEPs). Tailor controls and monitoring according to the risk profile.
Use Automated Compliance Tools
Leverage technology platforms that integrate transaction monitoring, identity verification, behavioral analytics, and risk scoring. Automation reduces human error, accelerates suspicious activity detection, and ensures compliance with AML regulations.
Regularly Audit and Update Controls
Continuously review policies, procedures, and monitoring systems to address evolving scams and regulatory changes. Frequent audits help detect gaps and strengthen defenses against emerging laundering techniques.
Organizations that adopt these strategies can minimize exposure, protect clients, and stay compliant with global AML regulations.
Also Read: How Banks Utilize Machine Learning For Fraud Detection
Financial institutions, fintech platforms, and digital businesses need technology that can detect suspicious behavior early, verify identities accurately, and flag high-risk transactions before laundering schemes escalate.

How AiPrise Helps Businesses Detect Money Laundering Scams
AiPrise unifies identity verification, behavioral intelligence, and risk scoring into a single orchestration layer, giving compliance, fraud, and risk teams a faster, clearer way to identify potential money laundering activity tied to users, payment methods, and transaction networks.
By detecting anomalies before they mature into criminal operations, the platform helps firms prevent regulatory violations, reduce financial crime exposure, and maintain smooth customer and transaction workflows.
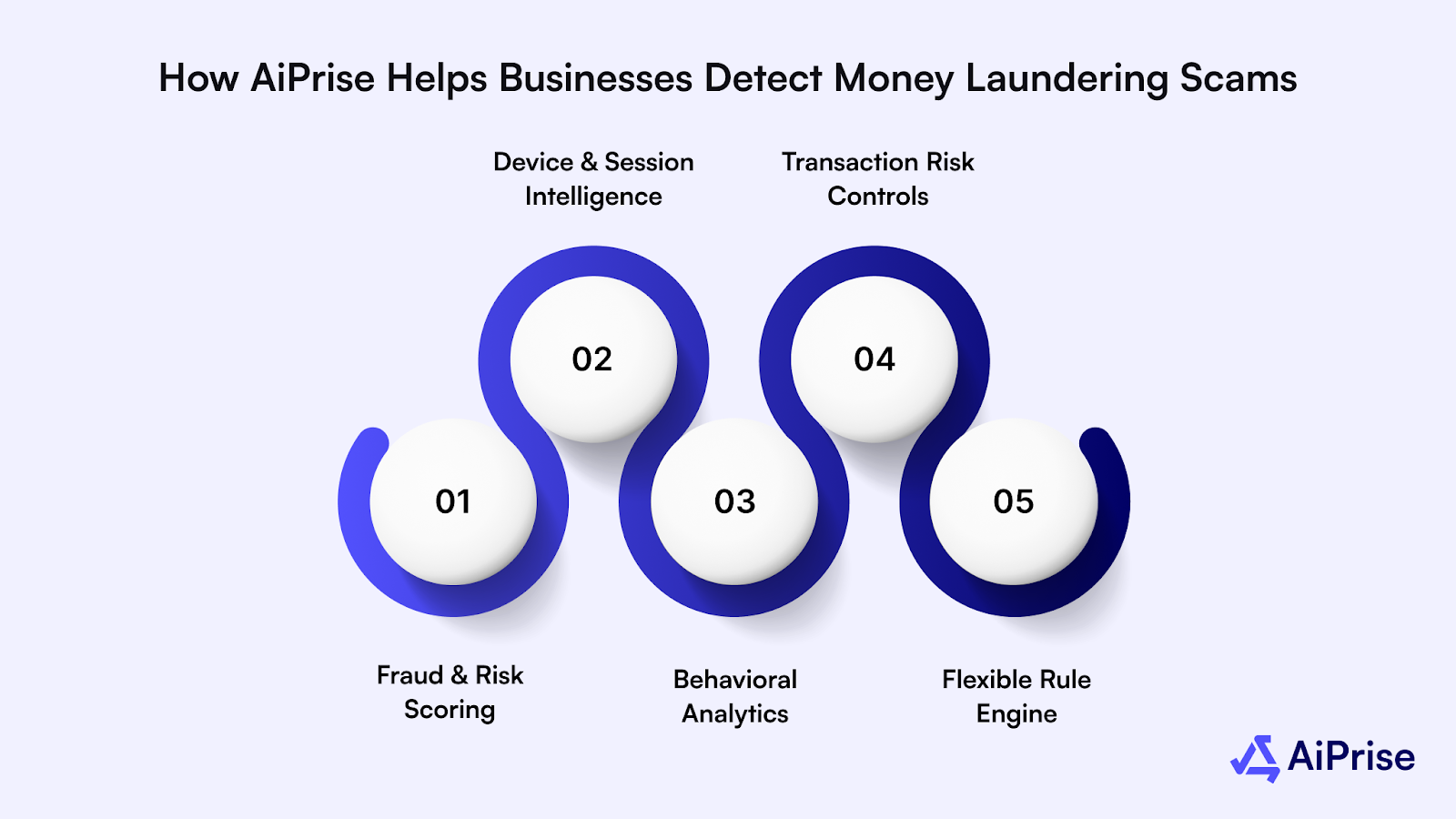
With AiPrise, businesses can:
- Fraud & Risk Scoring: Analyze risk at onboarding and across the full transaction lifecycle using 100+ signals, including identity data, behavior patterns, devices, IP intelligence, corporate registries, and adverse media to flag high-risk users and mule activity.
- Device & Session Intelligence: Detect compromised devices, browser spoofing, emulator usage, VPN abuse, and remote access tools (RATs) commonly used in money laundering and account takeover schemes.
- Behavioral Analytics: Monitor navigation behavior, interaction patterns, typing cadence, and session anomalies to identify social engineering victims, synthetic identities, and coercion-based mule behavior.
- Transaction Risk Controls: Apply transaction-level checks such as source-of-funds validation, counterparty reputation scoring, velocity limits, cooling-off periods, and automated holds for suspicious transfers.
- Flexible Rule Engine: Configure risk rules and automated workflows aligned with internal AML policies, regulatory requirements, and acceptable risk thresholds.
AiPrise gives businesses end-to-end visibility and adaptive control, helping them detect money laundering scams early while maintaining a seamless experience for legitimate customers.
Book a Demo to see how AiPrise strengthens identity verification and reduces money laundering risk across your operations.
Wrapping Up
Money laundering scams continue to evolve in scale and sophistication as digital payments, online platforms, and cross-border transactions accelerate. Businesses face growing challenges in identifying mule networks, tracing illicit fund movement, and staying aligned with tightening global AML regulations.
AiPrise delivers unified risk intelligence by combining identity verification, behavioral analytics, and transaction risk monitoring into a single platform. By detecting suspicious activity early and revealing hidden laundering patterns, it helps organizations reduce financial crime exposure and strengthen compliance operations with greater confidence.
Talk to Us Today to see how AiPrise helps businesses detect money laundering scams earlier, control risk, and protect their operations end-to-end.
FAQs
1. How are AI and deepfakes being used in money laundering scams in 2026?
Criminal groups now use AI-generated identities, voice cloning, and deepfake videos to bypass identity checks and recruit money mules. These tools allow scammers to fake executives, landlords, or employers convincingly, convincing victims to move funds or open accounts without realizing they are enabling laundering operations.
2. Are cryptocurrencies still the primary tool for money laundering in 2026?
Crypto is no longer the dominant laundering channel alone. While stablecoins, mixers, and privacy wallets are still used, criminals increasingly combine crypto with fintech apps, instant payment systems, gaming platforms, and prepaid financial products to fragment transactions and reduce traceability across multiple systems.
3. Why are young adults and gig workers being targeted as money mules more than ever?
Scammers exploit job insecurity, remote work trends, and payment app familiarity to recruit unsuspecting individuals as money mules. Fake employment offers, “account rental” schemes, and payment testing jobs are designed to appear legitimate while silently moving criminal funds through personal accounts.
4. How do real-time payments increase money laundering scam risks?
Instant payment systems remove the delay that once allowed banks to stop suspicious transfers. Once funds move in real time, they are often withdrawn, converted, or sent offshore within minutes, making recovery extremely difficult. This forces organizations to rely more on pre-transaction risk detection rather than post-transaction reviews.
5. What regulatory changes most affect money laundering scam investigations?
Expanded beneficial ownership registries, tighter crypto Travel Rule enforcement, stricter fintech KYC obligations, and cross-border data-sharing agreements now require companies to identify not just users, but also controllers, linked wallets, and indirect beneficiaries behind transactions. Non-compliance now carries higher personal and corporate liability.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.





Speed Up Your Compliance by 10x
Automate your compliance processes with AiPrise and focus on growing your business.












.png)

.png)








.png)















