AiPrise
10 min read
January 23, 2026
Transaction Screening vs Transaction Monitoring: Why Is It Important?

Key Takeaways










Fraud no longer happens in isolated incidents. It moves through everyday transactions, often disguised as legitimate activity, making it harder for you to stop before damage is done. For banks, payment providers, fintechs, and crypto platforms, every such approved transaction carries both revenue and risk.
The scale of the problem is growing fast. Newly released Federal Trade Commission data show that consumers reported losing more than $12.5 billion to fraud in 2024, a 25% increase over the prior year. As transaction volumes rise and payment speeds accelerate, criminals exploit gaps in controls, probe systems repeatedly, and adapt faster than many traditional defenses can respond.
This is why comparing transaction screening vs transaction monitoring matters. These two processes address different stages of financial crime risk, and confusing or relying too heavily on one can leave critical blind spots. Knowing how they differ yet work together helps your organization block high-risk activity early.
Quick Glance
- Screening checks transactions before approval to block sanctioned or prohibited activity, while monitoring reviews completed transactions to detect questionable patterns over time.
- Screening focuses on entities and sanctions lists; monitoring focuses on customer behavior, transaction patterns, and changing financial crime risks.
- Screening alone misses complex schemes like layering, while monitoring alone cannot prevent restricted payments from moving.
- FATF recommendations clearly mandate the use of both screening and monitoring.
- Accurate identity verification, real-time risk signals, updated watchlists, and adaptive monitoring logic reduce false positives and improve detection quality.
- Unified platforms like AiPrise combine identity verification, AML screening, behavioral insights, and risk scoring to strengthen both control approaches without adding friction.
What Is Transaction Screening?
Transaction screening is a preventive control used to review transactions before they are approved or executed. Its primary purpose is to identify and block transactions that may involve prohibited, fraudulent, or high-risk activity. If a transaction shows potential risk, it is flagged for review or stopped entirely before funds move.
It checks transaction data, such as the sender, receiver, and payment details, against sanctions lists, politically exposed persons (PEP) databases, and other AML watchlists. This helps you prevent regulatory violations and financial crime at the earliest possible stage.
From a compliance standpoint, transaction screening plays a key role within the customer due diligence (CDD) framework and broader AML/CFT controls. It helps prevent financial crime linked to fraud, sanctions evasion, money laundering, terrorist financing, proliferation of weapons, and corruption.
For effective risk control, transaction screening should:
- Occur before transaction approval or settlement
- Use updated global watchlists and sanctions
- Incorporate both internal risk signals and external data sources
- Provide clear risk indicators to support decision-making
What Is Transaction Monitoring?
Transaction monitoring is a continuous control that reviews completed and processed transactions to detect suspicious behavior or risk patterns over time. It focuses on analyzing customer activity after transactions occur to identify signs of financial crime that may not be obvious at the individual transaction level.
It evaluates both real-time and historical transaction data to build a clear picture of long-term customer behavior. Comparing current activity against known customer profiles and expected patterns helps you identify anomalies that could indicate illicit activity.
Transaction monitoring typically looks for:
- Large or unusual transactions
- Activity inconsistent with a customer’s risk profile
- Rapid movement of funds across accounts or jurisdictions
- Use of high-risk countries, products, or channels
From a compliance perspective, transaction monitoring is a critical part of AML programs and should not operate in isolation. It supports a broader monitoring for suspicious activity (MSA) approach, which includes ongoing customer due diligence (CDD) and behavioral analysis, not just individual transactions.
Also Read: A Complete Guide to Money Laundering Scams in 2026
Although they are often mentioned together, transaction screening and transaction monitoring rely on different signals. The differences become clearer when you compare how each works, what they focus on, and the risks they are designed to catch.
Transaction Screening vs Transaction Monitoring: A Clear Comparison
Transaction screening and monitoring are both critical AML controls, but they serve very different purposes. Understanding how these processes differ helps you close gaps, reduce false positives, and meet regulatory expectations without slowing legitimate activity.
Here's an example to show how the differences pan out in the real world.
Consider a scenario in which a criminal uses a seemingly legitimate business to move funds through multiple accounts to conceal the source of the funds.
- Transaction screening may not flag these payments because no sanctioned parties are involved.
- Transaction monitoring, however, can detect unusual transaction patterns, rapid fund movement, or abnormal volumes over time and trigger alerts for investigation.
Also Read: What Is the Difference Between Smurfing and Structuring in Money Laundering?
Let's now understand their combined importance in modern AML and fraud risk management programs.
The Importance of Transaction Screening and Transaction Monitoring
For financial institutions, payment providers, fintechs, and crypto platforms, transaction screening and transaction monitoring are not optional controls. They sit at the core of AML compliance and fraud risk management. While regulatory compliance is the primary driver, the real value of these processes goes beyond meeting legal obligations.
Together, transaction screening and monitoring help you stop prohibited activity early, detect evolving risks, and protect customers from financial harm. When implemented correctly, they reduce exposure to enforcement actions while supporting safe growth.
Pro Tip: Strong controls are not static. You must review, tune, and update screening and monitoring systems regularly to keep pace with new typologies, sanctions updates, and regulatory expectations.
What Happens When Controls Fall Short
Failing to screen or monitor transactions properly can lead to serious consequences:
- Regulatory fines and enforcement actions
- Increased scrutiny from regulators and banking partners
- Missed suspicious activity reports (SARs)
- Long-term damage to brand trust and customer confidence
Key Insight: Regulators expect institutions to promptly detect and report suspicious activity. Delays can expose both your organization and responsible individuals to legal action.
Key Questions to Evaluate Your Current Setup
You should regularly assess whether your screening and monitoring programs are fit for purpose. Ask questions such as:
- Are high-risk alerts prioritized effectively, especially with AI support?
- Do manual reviews slow investigations or hide risk context?
- Is the system using internal and third-party data to improve alert accuracy?
- Are sanctions and watchlists updated quickly after regulatory changes?
As you review these areas, reliable, up-to-date screening capabilities are essential, especially for identifying sanctioned entities, PEPs, and adverse media exposure early. Exploring AiPrise's foolproof watchlist screening can help you strengthen these controls while reducing manual effort and alert fatigue.
Also Read: How Continuous Payment Transaction Monitoring Prevents AML Risks
The above-mentioned expectations are not arbitrary. They are grounded in global regulatory standards that define how and when transaction screening and monitoring must be applied.
FATF Standards: The Foundation of Transaction Screening and Monitoring
Global AML expectations around transaction screening and transaction monitoring are primarily shaped by the Financial Action Task Force (FATF). Its recommendations define how financial institutions should prevent, detect, and report financial crime. These standards explain when screening applies, when monitoring takes over, and why both are required in a compliant AML framework.
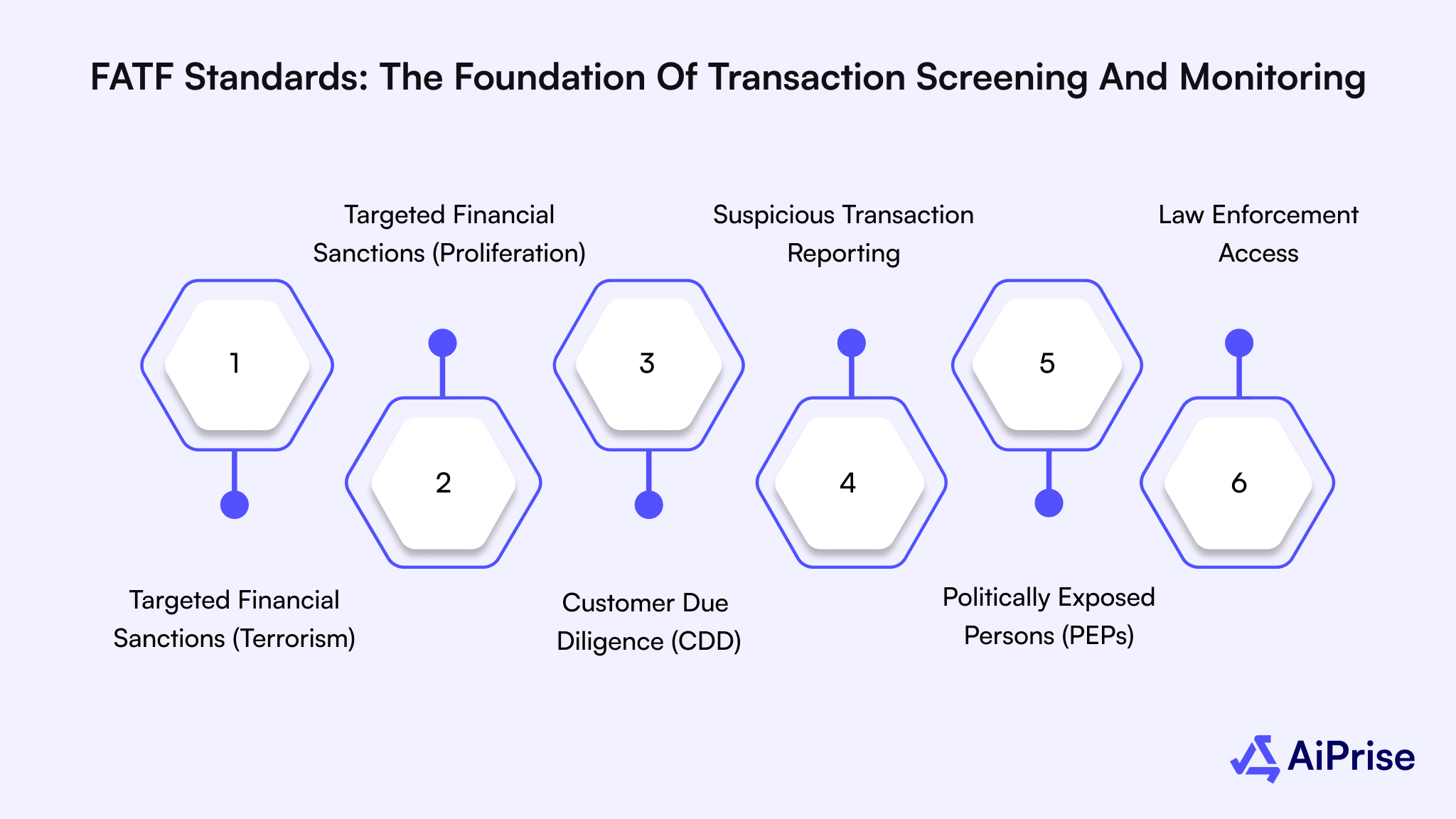
Below is how key FATF recommendations map directly to screening and monitoring responsibilities.
- Recommendation 6 – Targeted Financial Sanctions (Terrorism): Firms are required to screen transactions against terrorism-related sanctions lists. If a match is identified, the transaction must be blocked to prevent terrorist financing or related illicit activity.
- Recommendation 7 – Targeted Financial Sanctions (Proliferation): Organizations must screen transactions to ensure they do not involve individuals or entities sanctioned for the proliferation of weapons of mass destruction.
- Recommendation 10 – Customer Due Diligence (CDD): During onboarding or occasional transactions, firms must verify customer identities and assess risk. This supports transaction screening when suspicious activity is identified early.
- Recommendation 20 – Suspicious Transaction Reporting: If suspicious activity is detected after the customer relationship is established, firms must submit reports to the relevant Financial Intelligence Unit (FIU). This responsibility sits squarely within transaction monitoring.
- Recommendation 12 – Politically Exposed Persons (PEPs): Institutions must identify PEPs, apply enhanced due diligence, and escalate risks where needed. When suspicious activity is identified during payouts or account activity, alerts and SARs fall under transaction monitoring.
- Recommendation 31 – Law Enforcement Access: Law enforcement authorities must be able to access transaction monitoring data during investigations. This reinforces the need for clear audit trails and well-documented monitoring systems.
Key Takeaway: FATF recommendations make it clear that transaction screening and transaction monitoring are not interchangeable.
To consistently meet these FATF-driven expectations, you need technology that integrates screening, monitoring, and risk data without adding operational complexity. This is where a modern, automated fraud detection and risk scoring platform plays a critical role.
How AiPrise Strengthens Transaction Screening and Transaction Monitoring
Transaction screening and monitoring are only as effective as the data, context, and intelligence behind them. Gaps often arise when identity signals, behavioral insights, and compliance checks operate in silos. That separation makes it harder to stop prohibited transactions early or detect suspicious patterns over time.
AiPrise strengthens transaction screening and monitoring by unifying identity verification, behavioral intelligence, and AML controls into a single, connected risk layer. This allows you to block high-risk transactions upfront and continuously monitor customer activity with better accuracy and fewer misses.
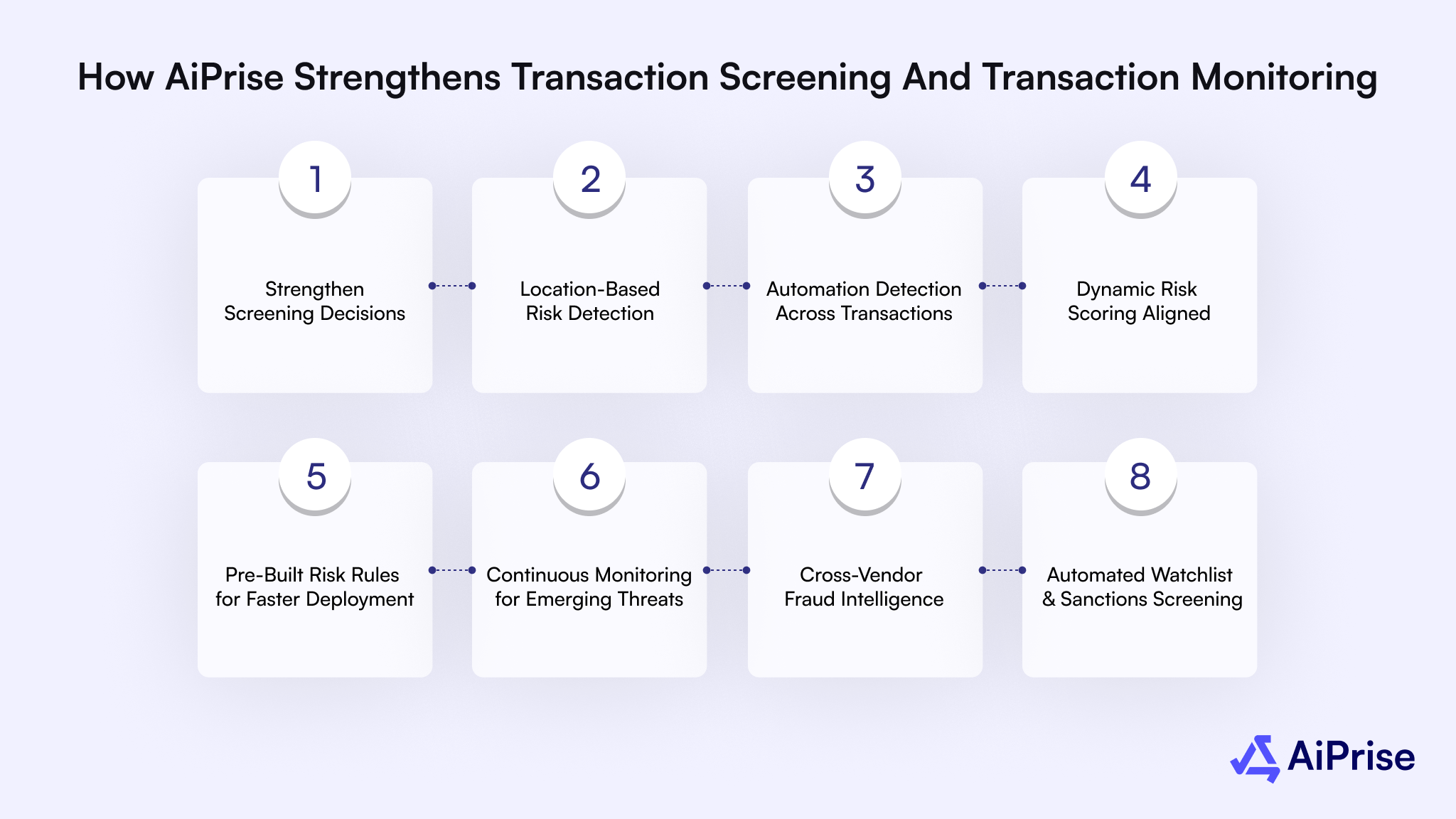
Here's how AiPrise delivers value across both screening and monitoring workflows:
- Identity Signals That Strengthen Screening Decisions: Email and phone insights add critical context during transaction screening. Signals such as email age, phone activity, social presence, and deliverability help identify high-risk identities before transactions are approved.
- IP and Device Intelligence for Location-Based Risk Detection: Accurate IP and device insights reveal where users are transacting from. That helps detect high-risk geographies, proxy usage, or unexpected location changes that may indicate fraud or evasion attempts.
- Bot and Automation Detection Across Transactions: Device analysis helps identify automated behavior and bot-driven activity, supporting both real-time transaction screening and continuous monitoring of abnormal transaction velocity or patterns.
- Dynamic Risk Scoring Aligned to Your Risk Appetite: Customizable risk scores enable you to tune screening and monitoring thresholds to your specific business model, customer base, and regulatory exposure.
- Pre-Built Risk Rules for Faster Deployment: Ready-to-use risk rules offer a quicker option to accelerate implementation for common fraud and AML scenarios.
- Continuous Monitoring for Emerging Threats: Customers and transactions are monitored continuously for fraud and compliance signals, enabling early detection of dicey patterns that single transactions alone would not reveal.
- Cross-Vendor Fraud Intelligence Correlation: AiPrise criss-crosses data from multiple sources to build a comprehensive fraud profile, improving both transaction screening accuracy and long-term monitoring outcomes.
- Automated Watchlist and Sanctions Screening: Transactions and entities are screened against global sanctions lists and PEP databases, supporting regulatory compliance and reducing exposure to financial crime risks.
By connecting transaction screening and transaction monitoring through a unified intelligence layer, AiPrise helps you move from reactive compliance to proactive risk management.

Final Thoughts
Transaction screening and monitoring serve different purposes, but modern AML programs depend on both working in sync. One focuses on stopping restricted payments upfront, while the other reveals hidden risk by tracking customer behavior over time. When these controls are aligned, you gain stronger visibility into financial crime risks without disrupting legitimate transactions.
AiPrise enables this alignment by embedding KYC and KYB checks, AML screening, and continuous risk intelligence directly into transaction workflows. This helps you move beyond surface-level checks and make decisions based on verified data, real behavioral insights, and the regulatory context.
If you're reassessing how effectively your business screens transactions, prioritizes monitoring alerts, or adapts to new AML expectations, Book A Demo. Explore how AiPrise supports smarter decisions across the whole transaction lifecycle.
FAQs
1. Can we use the same data sources for transaction screening and monitoring?
You can share core data sources, but you must apply them differently. Screening depends on sanctions and watchlists, while monitoring requires behavioral history, customer risk profiles, and past investigations to identify patterns rather than one-off risks.
2. How do false positives affect our screening and monitoring operations differently?
In screening, false positives delay payments and hurt customer experience. In monitoring, they overwhelm analysts and slow investigations. Reducing both requires stronger context, verified identity signals, and risk-based alert prioritization.
3. Can transaction monitoring help us detect insider fraud or internal misuse?
Yes. Monitoring can highlight unusual activity tied to employee accounts, privileged access, or internal systems. That way, it can help you detect internal fraud risks that traditional customer-focused controls often miss.
4. How do we manage transaction screening for real-time payments without slowing approvals?
You need low-latency screening supported by accurate matching and contextual risk signals. Overly aggressive name matching or outdated lists increase friction, while tuned logic allows compliant transactions to pass without manual review.
5. How do regulators expect us to link transaction screening decisions to SAR filings?
You must demonstrate how screened transactions, even if blocked, inform broader risk assessments. Regulators expect you to connect failed screenings, repeat attempts, and behavioral patterns when determining whether SARs are required.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.





Speed Up Your Compliance by 10x
Automate your compliance processes with AiPrise and focus on growing your business.




.png)













