AiPrise
7 min read
October 29, 2025
Comprehensive Guide to AML Transaction Monitoring Scenarios
Key Takeaways










False positives are draining your team’s time. Missed suspicious activity slipping through outdated rules. Lack of real-time context leading to inaccurate alerts. These aren’t rare issues; they’re everyday pain points for compliance officers and risk teams.
Today, financial institutions need smarter, faster, and more contextual transaction monitoring strategies. In 2024, the value received by known illicit cryptocurrency addresses dropped to $40.9 billion; it was still likely to be a record year for criminal inflows.
Why? Because that number reflects only the suspicious wallets we’ve identified so far, the real scale of laundering is likely far higher. In a threat situation, these opaque and fast-moving, rule-based systems alone aren't enough.
This blog will guide you through the process of how AML transaction monitoring scenarios work. You will understand where they break down, and how to design more intelligent systems that actually meet today’s compliance standards and tomorrow’s risks.
If you're short on time, here are five takeaways you’ll get from this guide:
- Understand what AML transaction monitoring scenarios are and how they work
- See real-world examples of high-risk transaction behavior across industries.
- Learn the challenges institutions face with false positives and evolving threats.
- Get best practices for building smarter, more dynamic monitoring scenarios.
- Discover how AiPrise enhances your existing setup with real-time behavioral signals
What Are AML Transaction Monitoring Scenarios?
AML transaction monitoring scenarios are predefined rules or behavioral patterns designed to detect suspicious activities. They include everything from structuring and layering to transactions in high-risk jurisdictions.
Each scenario serves as a filter applied to transaction data, flagging behavior that deviates from expected norms. These flags inform investigations and support regulatory filings like SARs (Suspicious Activity Reports).
Also Read: Microstructuring: Challenges in AML Compliance
Understanding these scenarios can help you better when you know why AML transaction monitoring scenarios matter is what turns alerts into real protection.
Why AML Transaction Monitoring Scenarios Matter
Regulators expect institutions to not only detect money laundering risks, but to anticipate them. Scenarios form the foundation of a proactive compliance strategy. When tuned properly, they help:
- Reduce false positives
- Catch more true threats early
- Provide defensible audit trails for regulators
- Align monitoring with evolving customer behavior and risk levels
Without strong scenarios, transaction monitoring becomes reactive and resource-heavy, opening the door to regulatory fines, reputational damage, and actual financial crime.
Common AML Transaction Monitoring Scenarios in 2025
With money laundering tactics becoming more subtle and diverse, transaction monitoring rules must evolve to detect suspicious behavior early. In 2025, regulators expect businesses to go beyond basic alerts and recognize more nuanced activity patterns across industries.
Below are the most common AML transaction monitoring scenarios that compliance teams must actively watch for:
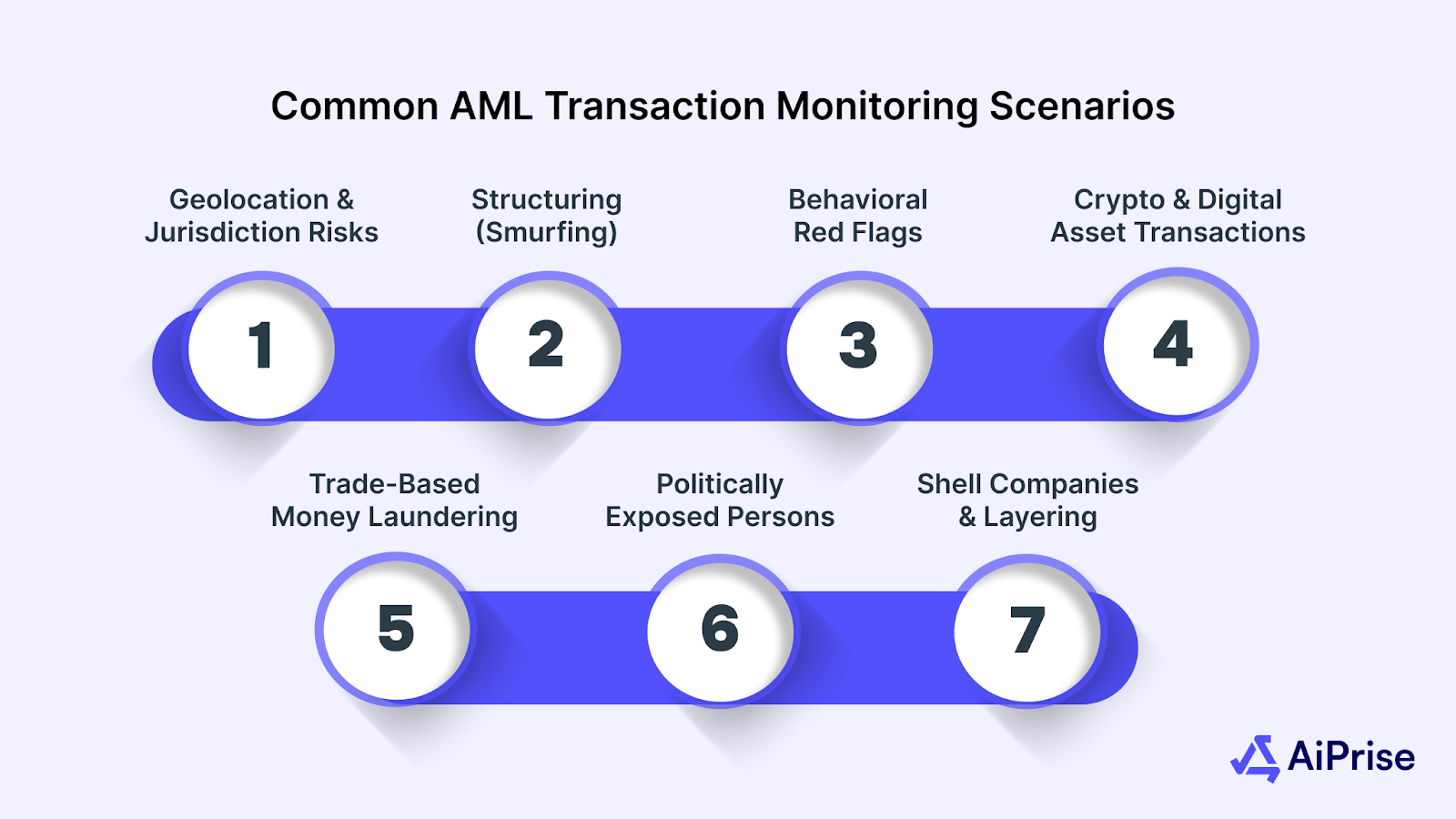
1. Geolocation and Jurisdiction Risks
Illicit transactions often involve jurisdictions known for weak AML regulations or international sanctions.
- Transfers to or from countries flagged for money laundering risks.
- Multiple transactions originating from flagged IPs or unusual geographic clusters.
2. Structuring (Smurfing)
Criminals break large amounts into smaller pieces to avoid triggering mandatory reporting thresholds.
- Several small deposits just below the regulatory threshold made within short time intervals.
- Splitting large payments across multiple accounts to hide the source of funds.
3. Behavioral Red Flags
Sudden shifts in account behavior may signal fraudulent intent or laundering attempts.
- Previously dormant accounts showing abrupt spikes in incoming or outgoing funds.
- Fast movement of funds without any supporting documents or clear economic purpose.
4. Crypto and Digital Asset Transactions
Digital currencies are frequently exploited due to their semi-anonymous and fast-moving nature.
- Transfers to and from exchanges without regulatory licenses or with known AML violations.
- Use of mixers, tumblers, or privacy-focused coins to obscure transaction trails.
5. Trade-Based Money Laundering
Fraudsters hide illicit funds by manipulating trade invoices or goods valuation.
- Goods priced well above or below market value to disguise fund movements.
- Invoice descriptions that don’t match the buyer’s business or expected trade activity.
6. Politically Exposed Persons (PEPs)
PEPs and their networks pose heightened risks due to their access to public funds and influence.
- Large or frequent transactions linked to a PEP or close associate flagged in screening.
- Suspicious account activity shortly after onboarding, such as back-to-back international transfers.
7. Shell Companies and Layering
Layering often involves routing funds through shell entities to obscure the money trail.
- Fund flows through businesses with no physical presence, website, or known employees.
- Complex ownership chains used to hide the true beneficiary or source of funds.
Also Read: Understanding Customer Screening for AML Compliance
Most systems can flag a transaction, but the real challenge lies in spotting what they miss, especially when criminals adapt faster than your rules do.
Real-World Challenges in Scenario-Based Monitoring
Even the most well-designed scenarios often fall short when outdated systems and siloed data stand in the way. These gaps not only increase operational load but also leave institutions vulnerable to financial crime.
Common challenges include:
- High False Positive Rates: Generic rule sets flag too many legitimate transactions, overwhelming compliance teams and wasting investigative resources.
- Static Thresholds: Fixed rules fail to adapt to a customer’s evolving behavior or risk profile, making the system less accurate over time.
- Lack of Real-Time Signals: Delays in data ingestion mean alerts arrive after the suspicious transaction has already cleared, reducing response time.
- Disconnected Data: Without linking identity, device, or behavioral data, scenarios lack the context needed for precise risk detection.
- Regulatory Scrutiny: Weak or outdated logic in AML scenarios can attract audits, penalties, and serious reputational harm.
To reduce noise and catch what actually matters, AML teams need smarter scenario design built on context, not just thresholds.
Best Practices for Designing Effective AML Scenarios
To build effective AML transaction monitoring systems, it’s not enough to simply detect outliers, you need to detect risk with precision. That means designing scenarios that reflect both regulatory expectations and real-world criminal behavior.

Here are the key practices that help AML teams stay effective:
- Use a Risk-Based Approach: Build rules that align with customer risk tiers, transaction types, geographies, and known red flags within the business model.
- Integrate Real-Time Customer Data: Pull in live signals like IP address, device type, and behavioral patterns to enrich context and validate whether a transaction truly appears suspicious.
- Layer Static and Behavioral Rules: Blend fixed transaction thresholds with dynamic behavior-based triggers to reduce false positives and improve detection accuracy.
- Continuously Tune and Optimize: Monitor performance, track false positive rates, and refine thresholds or retrain detection models based on emerging risks or audit outcomes.
- Ensure Clear Documentation: Every rule should be traceable to a risk rationale, clearly documented, and ready to stand up to scrutiny from auditors or regulators.
Also Read: Understanding the Digital Asset Anti-Money Laundering Act 2023
If you're still relying on rigid rules and outdated systems, AiPrise helps you detect risk faster with real-time signals, context-rich alerts, and adaptive AI.
Industry-Specific AML Intelligence with AiPrise

AiPrise works with high-risk, high-volume sectors where traditional transaction monitoring struggles to keep up. AiPrise helps compliance teams across industries detect complex patterns and reduce false positives, without disrupting core systems.
Each industry has unique transaction patterns, which is why scenario customization and real-time behavioral data are so important.
1. Fintechs & Neobanks
AiPrise helps fintechs and digital banks monitor fast-moving transactions without missing identity fraud or layered laundering attempts. It uses data signals from logins, devices, and sessions to spot anomalies across the customer lifecycle.
2. Crypto & Web3 Platforms
With coverage for 30+ chains and 150+ DeFi protocols, AiPrise gives crypto platforms real-time intelligence on wallet behavior, smart contract interactions, and cross-chain risks. This flags suspicious flows and risky entities as they happen.
3. Lending Marketplaces
For lenders, AiPrise detects fraud rings, synthetic identities, and fund redirection schemes by monitoring identity mismatches, session tampering, and unusual disbursement behavior.
4. Cross-border Remittance Services
AiPrise enables remittance providers to monitor mule activity and smurfing by linking sender and receiver data with geolocation, IP, and behavioral indicators. It traces patterns that span across borders and accounts.
5. Insurtech & Claims Processing
By mapping customer behavior from policy signup to claim payout, AiPrise detects indicators of application fraud, ghost broking, and claim manipulation. This helps reduce loss while ensuring compliance with evolving AML norms.
Automate your compliance processes with AiPrise and focus on growing your business. Speed Up Your Compliance by 10x today!
Conclusion
Rules alone can’t keep up with how fast financial crime evolves. Static systems, outdated data, and high false positives slow down your team and let real threats slip through. Compliance is no longer just about catching suspicious activity, it’s about catching the right activity, fast.
You need monitoring that adapts to risk in real time, flags context-rich alerts, and gives your team what they need to act, not just react. With AiPrise, you go beyond flagging but also understand the “why” behind every transaction.
And you act on it before it becomes a risk. Ready to future-proof your compliance?
AiPrise helps you speed up KYC, KYB, AML, and fraud risk management by 10x.
Cut false positives. Add context to alerts. Stay audit-ready, all in one place- Book a demo.
FAQs
Q1: What are AML transaction monitoring scenarios?
A1: AML transaction monitoring scenarios are predefined rules or behavior patterns used to detect suspicious financial activity. These include things like structuring, large transfers, or unusual account behavior.
Q2: Why is AML transaction monitoring important?
A2: It helps financial institutions detect and report potential money laundering and fraud. Effective monitoring also ensures compliance with global regulatory standards.
Q3: What triggers a suspicious activity alert in AML?
A3: Alerts are triggered by actions like large cash deposits, rapid transfers, use of high-risk countries, or unusual changes in customer behavior or transaction patterns.
Q4: How can you reduce false positives in AML monitoring?
A4: Use behavior-based rules, real-time data signals, and risk-based segmentation. Regularly tuning and testing scenarios also helps improve accuracy.
Q5: Which industries need AML transaction monitoring?
A5: Fintechs, crypto platforms, neobanks, lenders, insurance companies, and money service businesses all require AML monitoring due to high transaction volumes and regulatory risk.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.





Speed Up Your Compliance by 10x
Automate your compliance processes with AiPrise and focus on growing your business.










