AiPrise
15 mins read
July 28, 2025
Digital ID Fraud and Black Market: A Comprehensive Guide

Key Takeaways










A woman in New Brunswick had her account hijacked; what started as a simple Facebook login ended with her friends being scammed out of thousands. The scammer used her digital identity by sending fake messages to her contacts, collecting payments fraudulently, and then disappearing without a trace.
That’s digital ID fraud: when someone steals or fabricates identity data to impersonate you online. With tools like black market ID generator 3.0, fraudsters can now create fake identities in bulk, using AI to mimic real faces and documents.
The FBI warned in 2024 that criminals are actively using generative AI to scale these attacks, making scams more convincing and harder to trace.
This guide shows businesses how digital identities are compromised, traded on the black market, and misused, and importantly, how to protect your organization and customers.
In a Nutshell:
- Digital ID fraud involves using stolen or AI-generated data to create fake identities, with tools like black market ID generator 3.0 enabling large-scale fraud.
- Fraudsters exploit the black market to buy and sell personal data, using it to bypass security checks and commit financial crimes.
- AiPrise’s multi-layered approach combines AI-driven document verification, biometric checks, and real-time cross-referencing against global data sources to prevent fraud.
- By automating identity verification, AiPrise helps businesses stay compliant and detect fake profiles before they can be exploited.
What Is Digital ID Fraud?
Digital ID fraud happens when someone steals or fabricates personal data to impersonate an individual online. This could include their name, email, passwords, biometric details, or even device information.
Tools like black market ID generator 3.0 make it easier to generate fake identities at scale, combining leaked data with AI-generated content to build convincing digital profiles.
Here’s a breakdown of what counts as digital ID fraud:
- Using stolen login credentials to access someone else’s online accounts
- Creating fake identities using someone’s name, photo, or personal details
- Applying for loans, credit cards, or benefits using another person’s data
- Taking over social media or email accounts to impersonate the victim
- Registering SIM cards or phone numbers in someone else’s name
- Faking biometric data (like fingerprints or facial scans) to bypass security
- Combining real and fake information to build synthetic identities for fraud
- Selling or buying personal data on platforms like black market ID generator 3.0
- Using stolen identity details to trick others into sending money or sensitive information
All this stolen data fuels a hidden trade. The black market profits by packaging and selling these identities, either as full profiles or in parts, to anyone willing to pay.
How the Black Market Works and Who’s Behind It?
Once your data is stolen, it enters a supply chain. Some people steal it, others clean it up, and someone else makes money from it.
These profiles are then sold in bulk or as high-value “verified” IDs for premium scams.
Prices depend on how complete the identity is and how easily it can be used to open accounts, apply for loans, or pass KYC checks.
Who’s buying?
- Low-level scammers looking for quick cash
- Money mules and synthetic identity fraudsters
- Cybercrime gangs running phishing or loan fraud schemes
- Fake recruiters, sellers, or rental scammers needing a clean front
Who’s selling?
- Malware operators stealing credentials at scale
- Data breach traders
- Developers of identity generation tools and spoofing software
- Former insiders from telecom, finance, or public sector services
Here’s how the different parts of the web are used in this chain:
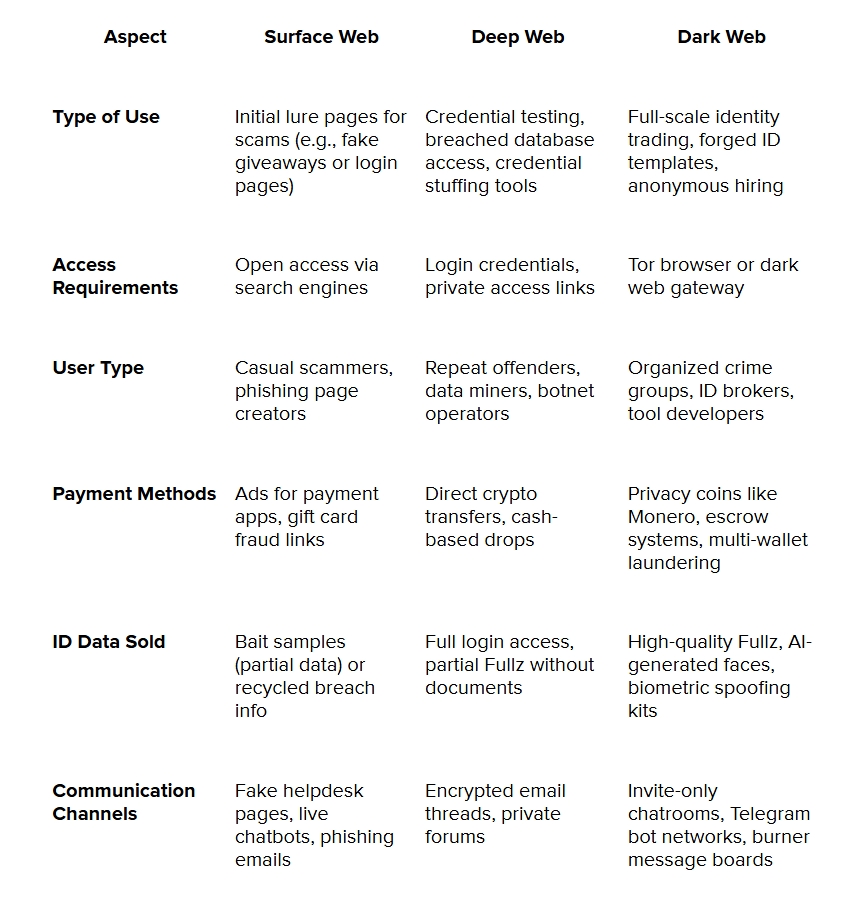
This isn’t some chaotic mess. It’s structured, fast, and quietly growing. And the easier it gets to create fake IDs, the faster the black market moves. Let’s look at how these frauds actually take place.
How Do Frauds Happen? The Mechanics of ID Theft
Digital ID fraud relies on access, not sophistication. Most attacks begin with everyday vulnerabilities, an exposed email, a reused password, or information pulled from a breached database.
Once data is stolen, it is shared across criminal networks using encrypted channels or sold on marketplaces, enabling fraudsters to impersonate victims or access their accounts.
Here’s a step-by-step breakdown of how digital ID theft typically happens:
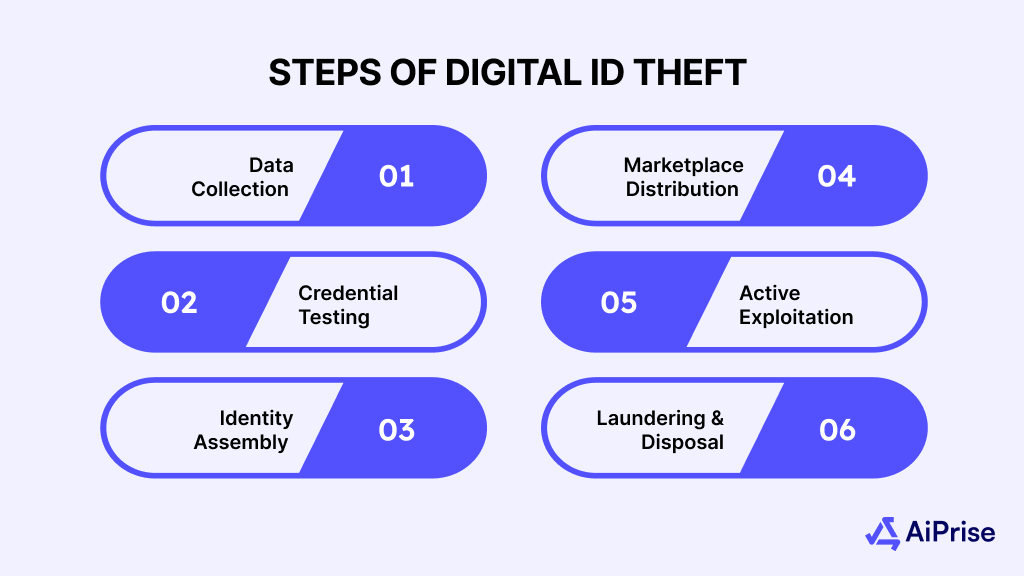
1. Data Collection
The process usually starts with gathering personal data. Attackers pull this information from various sources, often without needing to breach anything themselves.
The common sources from which this personal data is pulled are as follows:
- Phishing emails: Fake bank or tax notices asking for login details
- Malware: Keyloggers or screen scrapers silently installed via infected attachments
- Public data dumps: Email addresses, phone numbers, and passwords from past breaches
- Social media oversharing: Birthdays, schools, or pet names used in password hints
- Data scraping: Bots that collect personal info from public websites, job boards, or resume portals
- Third-party leaks: Platforms like LinkedIn, Facebook, or payment processors hit in past breaches
Example: The LinkedIn data leak in 2021 exposed over 700 million records, many still used in identity theft today.
2. Credential Testing (Credential Stuffing)
Once attackers get credentials, they test them across multiple platforms to see what else they can access.
The tools used for credential testing include the following:
- Automated bots like Sentry MBA or Snipr
- Combo lists (email: password pairs) bought in bulk
- Proxy pools to avoid detection by login systems
Example: A leaked Netflix password could unlock someone’s email or even online banking if reused.
3. Identity Assembly
After enough fragments are collected, fraudsters build a complete identity, real or synthetic.
The fragments fraudsters combine include:
- Name, address, date of birth
- National IDs like SSNs or PAN numbers
- Phone numbers, email addresses
- Biometric data like selfies or fingerprints (from leaked scans or face recognition apps)
- Device fingerprinting (browser type, location patterns, IP history)
4. Marketplace Distribution
Completed profiles are then sold on dark web forums or Telegram groups.
The places where these identities are sold include:
- Dark web markets (e.g., Genesis, White House Market)
- Invite-only Telegram channels with escrow systems
- Encrypted marketplaces with Monero or Bitcoin-only payments
The packages sold include:
- “Fullz” (full ID kits with login + document scans)
- “Verified accounts” for banking or trading platforms
- Fake passports or licenses with facial overlays
5. Active Exploitation
Once sold, identities are used to commit fraud or bypass KYC checks.
The fraud uses for these identities include:
- Opening new bank accounts or mobile wallets
- Applying for loans or credit cards
- Filing fake tax returns or unemployment claims
- Creating fake seller profiles on marketplaces
- Running romance or rental scams using fake social profiles
Example: Fraudsters in the US used stolen IDs to apply for PPP loans during COVID-19, causing billions in losses.
6. Laundering and Disposal
Any stolen funds are moved quickly to avoid tracing.
The common laundering methods used include:
- Peer-to-peer payment apps (Venmo, GCash, Cash App)
- Cryptocurrency mixers to hide transaction trails
- Shell companies or fake e-commerce orders
- Money mules who transfer stolen funds using real accounts
Once the identity becomes risky to use (e.g., flagged or reported), it’s either resold at a discount or discarded.
Not all stolen identities are equal; some are worth more, and some people get targeted more often.
Valuable Identity Data and Common Target Profiles
Stolen identities are treated like products, each with a different value depending on how complete or exploitable the data is. What gets sold, what it costs, and who ends up being targeted all follow patterns shaped by demand, risk, and access.
Understanding these patterns helps you see how identity fraud operates beyond just the theft.
What buyers want:
Buyers want identities that are ready to use or easy to build on. The more complete the profile, the more they’re willing to pay.
What sells best:
- Verified credentials with matching email, phone, and address
- Clean credit histories that pass lender or KYC checks
- Bank logins with two-factor disabled or bypassed
- Biometric data, like face scans or fingerprint,s for document matching
- Government-issued IDs linked to real personal details
- Long-standing accounts that won’t raise flags when accessed from new devices
What drives price?
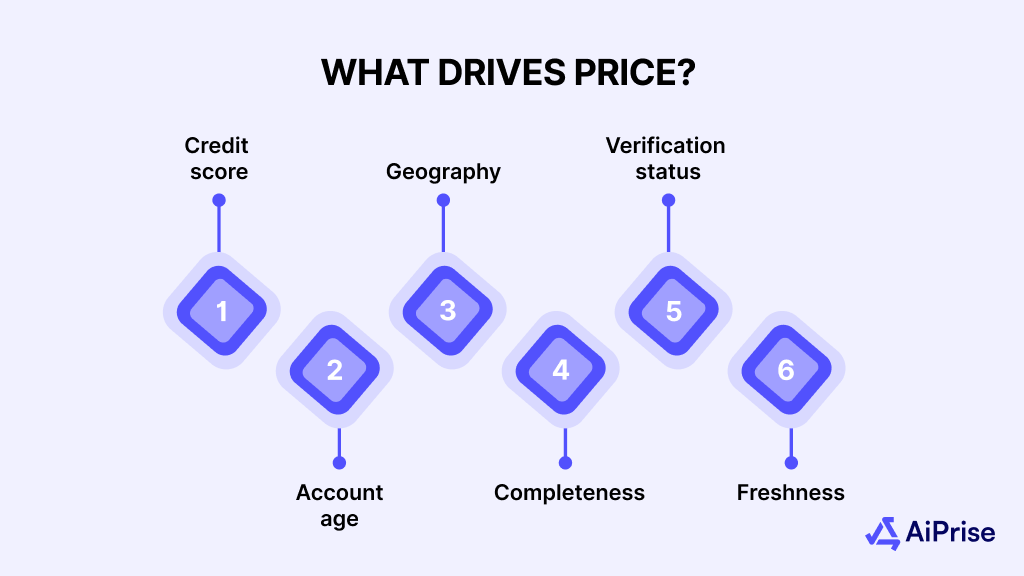
Prices are based on how easily the identity can be used without triggering suspicion.
- Credit score: Higher scores fetch more because they unlock larger credit lines
- Account age: Older accounts appear more legitimate and pass fraud checks more easily
- Geography: IDs from countries with weaker verification get less, while US, UK, and Canada IDs cost more
- Completeness: Full profiles with linked phone numbers, emails, and documents command higher rates
- Verification status: Pre-verified accounts or KYC-passed profiles are priced higher
- Freshness: Recently stolen data is more valuable before passwords or logins are changed
Who’s most targeted?
Some profiles are easier to exploit or more profitable, so they get targeted more often.
- Seniors: Often less active online, making fraud harder to detect quickly
- Students: New credit profiles and limited monitoring make them easy targets
- Deceased individuals: Their data stays active in systems long after death
- High-income earners: More likely to have large credit limits and multiple accounts
- People in countries with weak enforcement: Fewer checks make fraud easier to carry out
- Those exposed in past data breaches: Once leaked, that information keeps circulating and stacking up over time
Once you understand how identity fraud works and why certain profiles are targeted, the next step is figuring out how to reduce your exposure.
How Businesses Can Defend Against Digital ID Fraud
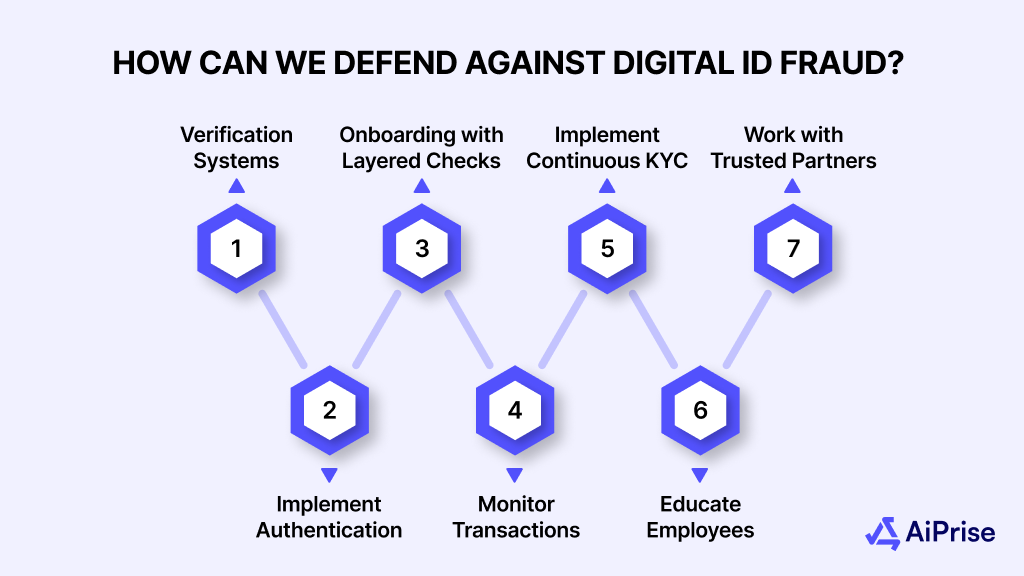
As digital ID fraud continues to rise, businesses must take proactive measures to safeguard their operations and customer data. Here are key actions businesses can implement to protect against this threat:
- Adopt Advanced Identity Verification Systems
Simple document uploads or selfie scans are no longer enough to verify identity. Use advanced verification methods like biometric recognition, real-time data cross-checking, and device-based authentication to ensure the identity is genuine before granting access. - Implement Risk-Based Authentication
Use dynamic risk-based authentication to assess the risk level of each transaction or login attempt. This can include analyzing factors like location, device, and behavior patterns to determine whether additional verification steps are needed. - Enhance Customer Onboarding with Layered Checks
During customer registration, apply multiple verification layers that check the validity of documents and cross-reference personal details with trusted data sources. This minimizes the chance of fraudsters using fake identities to gain access. - Monitor Transactions for Suspicious Behavior
Continuous monitoring of transactions and account activities can help detect suspicious behavior early. Unusual login attempts, changes in spending patterns, or multiple failed verification attempts should trigger immediate alerts for further investigation. - Implement Continuous KYC (Know Your Customer)
Rather than relying on a one-time verification, businesses should adopt continuous KYC practices. Regular re-verification and updating of customer data help ensure that fraudsters don’t maintain access with outdated or stolen credentials. - Educate Employees and Customers on Security Best Practices
Ensure your team is trained to identify phishing attacks, social engineering tactics, and other fraud methods. Likewise, educate customers on creating strong, unique passwords, using two-factor authentication, and monitoring their accounts for unusual activity. - Work with Trusted Fraud Prevention Partners
Collaborate with fraud prevention services that specialize in digital ID verification. These partners can provide tools like document authentication, device fingerprinting, and AI-driven fraud detection to protect your business from evolving threats.
For everything else, stolen logins, fake profiles, or small-scale scams, it’s usually on you to spot it early, report it fast, and limit the damage before it spreads.
How AiPrise Helps Businesses Prevent Digital ID Fraud
AiPrise provides a reliable identity verification platform designed to handle large volumes, meet regulatory standards, and protect against sophisticated fraud.
Here’s how it stands out in enabling secure and efficient digital onboarding:
- Verifies IDs from 200+ countries in under 30 seconds with AI-driven OCR, barcode/MRZ scanning, and enhanced security feature checks for over 12,000 document types.
- Performs biometric checks (facial recognition, liveness detection) to prevent spoofing, deepfakes, and synthetic identity fraud.
- Integrates with 800+ data sources for instant cross-referencing against government, credit, and sanctions lists, ensuring global KYC and KYB compliance.
- Customizable rule engine and risk scoring: Tailor onboarding flows and risk thresholds, automating low-risk approvals and escalating high-risk cases for review, reducing manual review time by up to 95%.
- Continuous fraud monitoring: Real-time alerts, adverse media scans, and ownership checks mean your systems don’t stop at onboarding. AiPrise helps you track identity risk as it changes.
- Fast, flexible setup: With white-label UI, API and SDK support, and multi-language capability, AiPrise can go live in days, without disrupting your current flow.
AiPrise helps you verify identities, spot fraud, and stay compliant all in one place, without slowing things down.
Conclusion
Strong identity checks help you stop fraud before it starts. With the right tools, you can flag fake profiles, meet KYC requirements, and onboard customers without slowing things down.
It’s not just about compliance, it’s about keeping your business a step ahead of digital ID scams.
Want to strengthen your identity checks and cut fraud risks? Book A Demo with AiPrise to see how the platform fits into your workflow and helps you stay secure and compliant.
FAQs
1. What is digital identity fraud?
Digital identity fraud involves using stolen or fake personal information, like names, emails, or ID numbers, to impersonate someone online, often for financial gain.
2. How do scammers get digital identity information?
They collect data from phishing emails, malware, public leaks, social media, and dark web marketplaces. Some use tools like black market ID generator 3.0 to build synthetic identities from stolen data.
3. What can criminals do with stolen identity data?
They can open bank accounts, apply for loans or credit cards, file tax returns, rent properties, or run scams using your identity.
4. What risks does digital identity fraud pose to businesses?
Fraudsters can use stolen identities to open accounts, apply for credit, access company systems, and conduct unauthorized transactions, putting businesses at risk of financial losses and security breaches.
5. Can businesses detect fake or AI-generated IDs?
Yes, with the right identity verification tools that include biometric checks, document verification, and real-time data matching across trusted sources.
6. How does AiPrise help prevent digital ID fraud?
AiPrise uses document verification, biometric checks, and data cross-referencing from over 800 sources to spot fake or manipulated identities. It helps businesses catch fraud early, meet compliance requirements, and streamline customer onboarding.
You might want to read these...

AiPrise’s data coverage and AI agents were the deciding factors for us. They’ve made our onboarding 80% faster. It is also a very intuitive platform.





Speed Up Your Compliance by 10x
Automate your compliance processes with AiPrise and focus on growing your business.





